
The Future of Quantum Computing: Opportunities, Challenges, and Enterprise Impact
Quantum computing is moving from theory to enterprise reality faster than anyone expected. Error rates are improving, qubit counts...

Quantum computing is moving from theory to enterprise reality faster than anyone expected. Error rates are improving, qubit counts...

Financial leaders are under pressure to move faster, tighten controls, and deliver cleaner insights. This is why digital transformation...

Every digital initiative today runs on agility. Yet one strategic question divides even the most experienced leaders: Kanban vs...

Every enterprise operates in the cloud. The next frontier of growth lies in how effectively they convert cloud computing...

For over three decades, enterprises have pursued Business Process Reengineering (BPR) as a proven path to transformation, but in...

Every second, healthcare systems generate more data than ever imagined, clinical notes, imaging results, wearable sensors, genomics, and patient...

The alert came from an unexpected place, a routine compliance audit. What began as a standard review quickly revealed...

The boardroom falls silent. Your CFO presented quarterly results, and the numbers tell a story nobody wants to hear....
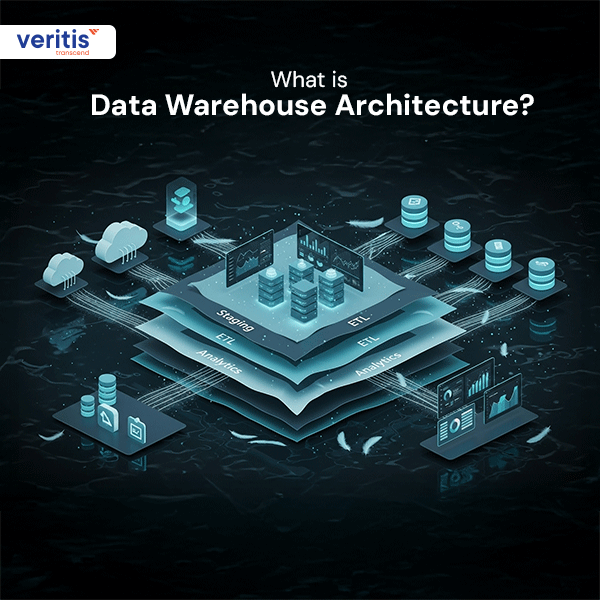
Every executive has experienced it: the long wait for answers while competitors move faster. Imagine your CFO requesting quarterly...
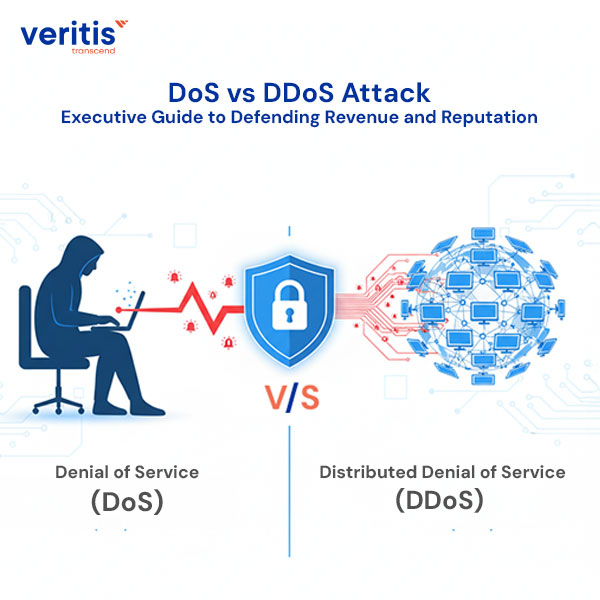
Picture this scenario. Your enterprise operations are humming along smoothly when suddenly your primary customer portal crashes. Revenue streams...