DevSecOps Services
Integrating ‘Security as Code’ Culture Within DevOps
Recently, DevOps adoption has led to a significant transformation in enterprise computing. DevOps practices are instrumental for organizations deriving value-added benefits such as increased agility, speed, reduced costs, and features such as serverless computing, dynamic provisioning, and pay-as-you-go cost models.
Despite its enormous popularity, DevOps has been found wanting in cases requiring a secure code delivery. This has led to the developing of a new approach that facilitates the co-existence of information security with DevOps, commonly referred to as ‘DevSecOps’.
The Need for DevSecOps
DevOps has made it possible to develop customized software and business applications faster by aligning development and operations teams through DevOps. However, in most cases, security has not been accorded a high priority in DevOps implementation and is often viewed as a roadblock to rapid development.
Though organizations are increasingly focused on breaking down the traditional silos between the development, testing, and operations teams, many of them haven’t been integrating security into their development process, becoming susceptible to the risk of threats and vulnerabilities.
Here is where DevSecOps Services comes in. The DevSecOps approach includes incorporating security as a significant component of DevOps practices. Through continuous monitoring, assessment, and analysis, DevSecOps services ensure that loopholes and weaknesses are identified early in the development process and remediated immediately.
DevOps Vs. DevSecOps
While DevOps refers to the collaborative environment between the development, testing, and operations teams to achieve continuous delivery, DevSecOps involves integrating the security component into the DevOps process.
DevSecOps tools tackle DevOps Automation security issues, such as configuration management, composition analysis, etc.
What Exactly is DevSecOps?
DevOps is commonly understood as a combination of processes and tools that facilitate ongoing collaboration between the software engineering and infrastructure teams.
These, in turn, automate the rapid and reliable delivery of applications and services across organizations. DevOps includes several focus areas: automated provisioning, continuous integration, continuous monitoring, and test-driven development.
As an extension of the DevOps mindset, DevSecOps services embed security controls and processes into the DevOps workflow and automate the core security tasks. These DevSecOps cyber security principles are introduced early in the development process and are implemented throughout the Software development life cycle (SDLC).
In addition to providing DevOps teams with security knowledge and practices, DevSecOps services incorporate application development knowledge and processes into security teams for efficient collaboration.
There is no unanimity in the IT field about the usage of the term ‘DevSecOps,’ which is sometimes referred to as ‘DevOpsSec’, ‘SecDevOps’ or ‘Rugged DevOps.’
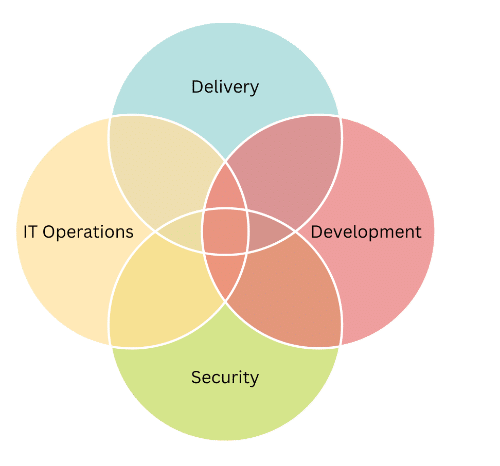
Major Components of the DevSecOps Model
Organizations must incorporate a cultural and technical shift in their approach to DevSecOps services to address real-time security threats more efficiently.
A practical DevSecOps approach requires consideration of six major components. These include:
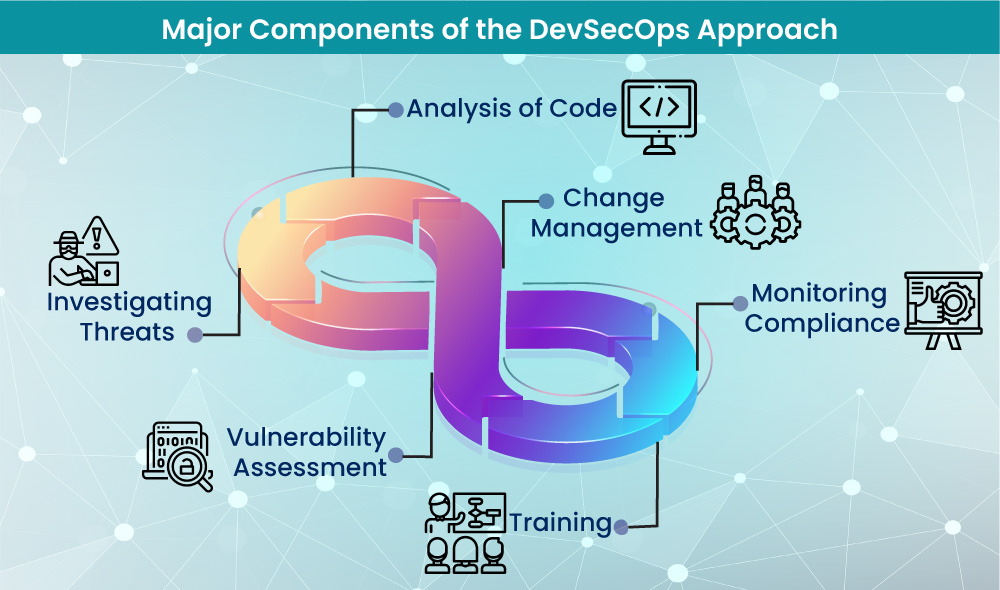
Analysis of Code
This enables the quick identification of vulnerabilities through the delivery of code in small chunks.
Change Management
This allows users not only to submit changes that can increase speed and efficiency- but also to determine if the impact of the change is positive or negative.
Monitoring Compliance
Organizations should comply with regulations such as the General Data Protection Regulation (GDPR) and Payment Card Industry Digital Security Standard (PCI DSS) and be prepared for audits at any time by the regulators.
Investigating Threats
Potential emerging threats accompany each code update. It is crucial to identify these threats at the earliest and respond immediately.
Vulnerability Assessment
This involves the analysis of new vulnerabilities and the response to them.
Training
Organizations need to involve their software and IT engineers in security-related training and equip them with the guidelines for set routines.
Adopting a DevSecOps Cyber Security Strategy
Moving from DevOps to DevSecOps is not a simple proposition, but can be achieved successfully in phases with proper planning. There are three key steps that organizations need to consider while adopting DevSecOps:
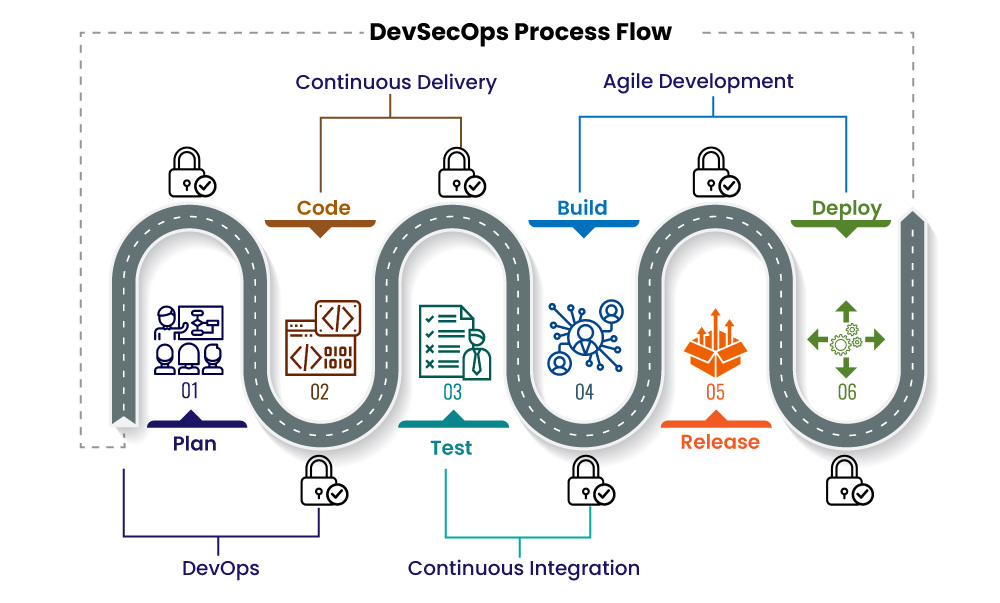
Assessment of Current Security Measures
Security teams perform threat modeling and conduct risk assessments, which help them to analyze the sensitivity levels of an organization’s assets and their likely threats. Additionally, they can understand the current security controls and prioritize those requiring modification.
Integrating DevSecOps With Security Operations
A DevSecOps cyber security strategy implementation can be considered successful only if the development, security, and operations teams are committed to working in coordination and embedding security processes and controls into the entire DevOps workflow. Continuous monitoring of security concerns during development and ensuring a quick response are vital for integrating security operations with the DevSecOps services.
Merging Security into DevOps
Integrating security measures into the development process involves the examination of the development workflow and ensuring minimal disruptions because of the incorporation of security practices and automation.
Essential DevSecOps Tools
Essential DevSecOps Tools adoption involves assessing application security risks and code testing for which specialized tools are essential.
Operating automated testing tools in an integrated development environment (IDE) enables developers to incorporate security into the DevOps workflow and avoid launching a new environment for testing code every time.
Several tools have been developed to facilitate various aspects of DevSecOps implementation. These include:
Visualization Tools
Tools such as Kibana and Grafana help identify, evolve, and share security information with operations.
Automation Tools
Tools like StackStorm help provide scripted remediation whenever security defects are detected.
Hunting Tools
These tools help in detecting security anomalies. A few examples include Mirador, OSSEC, MozDef, and GRR.
Testing Tools
Testing is a critical element of DevSecOps, with an extensive range of tools such as GauntIt, Spyk, Chef Inspec, Hakiri, Infer, and Lynis being used.
Alerting Tools
Tools such as Elastalert, Alerta, and 411 provide alerts and notifications upon discovering security defects requiring remediation.
Threat Intelligence Tools
These tools capture and collate threat intelligence, including OpenTPX, Critical Stack, and Passive Total.
Attack Modeling Tools
These help in operationalizing attack modeling and security defenses.
DevSecOps Services, a Top Business Priority
Integrating security with DevOps is not just a technological consideration but also involves people and processes. Successful DevSecOps implementation requires IT teams to focus on business risks and security.
The global DevSecOps market is expected to grow at a CAGR of 23.84% during 2023-2030. DevSecOps tools ensure a secure application delivery and a much quicker time to market.
Organizations can achieve unparalleled success by proactively adopting DevSecOps automation and redefining their operations, engineering, and security to work cohesively.
Data Insights: DevSecOps Services and Business Impact
Global Market Forecast
1) USD 5.9 billion by 20232) 31.2% CAGR
>11.5X
Speed of DevSecOps programs over traditional practices in fixing flaws60%
Survey participants reported that DevSecOps presents technical challenges2:7
Median-mean ratio of app scans required with DevSecOps annually338%
Mature DevOps firms likely to integrate automated security54 %
Survey participants cited enhancing security, quality, and/or resilience as their reasoning for adopting DevSecOps best practices91%
Firms consider security integration throughout software development50%
Higher profit growth with DevSecOps as per software security experts2.5X
Performance rate of DevSecOps firms in outpacing competitorsHow to Implement DevSecOps?
DevSecOps combined them into a single streamlined process by incorporating security at the code level, thus ensuring the safety of applications and procedures at all levels of the process chain.
Five features speak about the successful implementation of DevSecOps:
- Mandatory security at every stage
- Thorough Assessment before security
- Security-related changes right at the code level
- Automation of all possible processes
- Continuous monitoring through alerts and dashboards
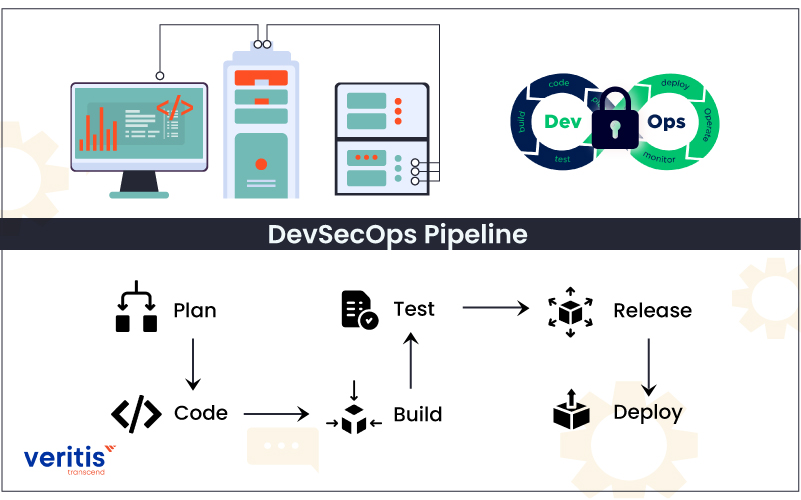
Business Benefits of DevSecOps
By shifting from DevOps to DevSecOps services, organizations can transform their handling of the development pipeline. Increased collaboration between the development, security, and operations teams ensures that vulnerabilities are identified, and security threats are minimized in the early stages.
DevSecOps provides several other advantages to enterprises: greater agility and speed for the security teams, enhanced communication and collaboration between the teams, and identification of code vulnerabilities.
DevSecOps also enables organizations with an ability to rapidly respond to change, in addition to providing opportunities for quality assurance testing and automated builds.
Some additional benefits also result from the adoption of DevSecOps, which include:
Automatic Securing of Code
DevSecOps tools reduce the risk of introducing security flaws through human error by automating tests and enabling excellent coverage, consistency, and predictable processes. Additionally, any issues can be tracked and fixed as soon as they occur during development.
Continuous Security Enablement
Using DevSecOps automation tools, organizations can create a closed-loop process for testing and reporting, ensuring that all security concerns are immediately resolved.
Leveraging Security Resources
DevOps automates most of the standard security processes and tasks that require less hands-on time, such as event monitoring, account management, code security, and vulnerability assessments. It allows security professionals to focus on threat remediation and eliminate strategic risk.
Why Choose Veritis for DevSecOps Consulting Services
Veritis, a Stevie Award, and Globee Business Award winner, is one of the few end-to-end DevSecOps Consulting Services and Solutions providers. Our consultants specialize in assessment, implementation, and support for the DevSecOps initiatives of our clients, spanning from simple to complex enterprise-level IT projects.
We develop consultative solutions that enable clients to secure product development with DevSecOps capabilities. We produce tailored DevSecOps platforms integrating security into areas such as build automation, test automation, deployment automation, monitoring, environment management, and others.