Introducing changes to business processes or technology platforms always carries a certain level of risk. In the case of cloud it services, organizations rely on cloud governance teams, also known as cloud custodians, to mitigate these risks and ensure a smooth transition without disrupting adoption or innovation efforts.
Cloud computing offers numerous advantages, such as faster and more agile responses to changing business needs. However, it also presents a significant risk: the loss of control. This risk can manifest as cost overruns, inefficient utilization of cloud resources, security breaches, cloud data governance leaks, and non-compliance with regulations.
Given the increasing shift towards the cloud, businesses must adapt their processes to align with new technologies. This is where cloud governance services play a crucial role. Like corporate governance, cloud governance serves as a framework designed to manage and optimize services in the cloud. By implementing a cloud governance framework, organizations can effectively address security risks and ensure the seamless operation of their cloud-based services, enabling teams to leverage the benefits of efficiency and innovation while mitigating potential security issues.
Get Expert Advice on Cloud Services
What is Cloud Governance?
Rules and regulations apply to every system, process, or organization—so why should the cloud be any different? While the cloud has data security and privacy rules, there aren’t any pre-set rules or regulations for how businesses should function in the cloud. Hence, businesses must create operations, monitor, and adjust rules to stay competitive and relevant.
The cloud has revolutionized the ease with which teams within organizations can develop and deploy their systems with a simple click. While this fosters innovation and productivity, it can also lead to certain challenges, including:
- Insufficient integration between cloud systems, even within the same organization.
- Redundant efforts or cloud data governance duplication across different parts of the organization.
- Lack of alignment between cloud systems and overarching business goals.
- One potential risk is deploying cloud systems without sufficient access control measures, leading to new security vulnerabilities.
Cloud governance services play a crucial role in addressing these challenges. It ensures that asset deployment, system integration, data security, and other critical aspects of cloud computing are meticulously planned, considered, and effectively managed. Cloud governance is a dynamic practice because various groups within the organization can create and maintain cloud systems, involve third-party vendors, and undergo frequent changes.
Through cloud governance initiatives, organizations ensure that this complex cloud environment adheres to organizational policies, follows cloud governance best practices, and meets compliance obligations. This proactive approach enables businesses to effectively navigate the complexities of cloud computing while maintaining robust governance and control over their cloud-based systems and assets.
Cloud Governance Model Principles
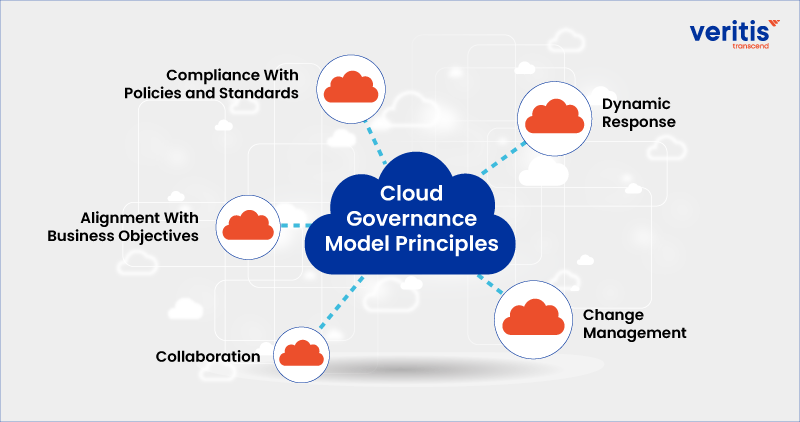
When establishing a cloud governance model, it is crucial to consider the following five principles as a solid foundation:
1) Compliance With Policies and Standards
Ensuring that your organization’s cloud usage standards align with relevant regulations and compliance standards is imperative. This includes adhering to industry-specific requirements and maintaining consistency with other organizations within your sector. Doing so can mitigate risks, protect sensitive data, and maintain legal and regulatory compliance.
2) Alignment With Business Objectives
Your cloud strategy should seamlessly integrate with your overall business and IT strategy. Adopting cloud systems and policies should be driven by their demonstrable ability to support and advance your organization’s overarching business goals. By aligning your cloud initiatives with business objectives, you can maximize the value derived from the cloud and effectively leverage its capabilities to drive innovation and growth.
3) Collaboration
Effective cloud governance strategies require clear agreements and collaboration between stakeholders, including cloud infrastructure owners, users, and other relevant organizational units. This collaboration ensures that all parties use cloud resources appropriately and mutually beneficial. By fostering strong communication and collaboration, you can optimize resource allocation, avoid duplication of efforts, and promote efficient utilization of cloud infrastructure.
4) Change Management
Any changes made to the cloud environment must follow consistent and standardized processes. This involves implementing robust change management practices and subjecting all modifications to appropriate controls. Maintaining a structured approach to change management can minimize disruption, ensure operational stability, and mitigate risks associated with uncontrolled or unauthorized changes in the cloud environment.
5) Dynamic Response
Cloud governance should be responsive and adaptable to the dynamic nature of the cloud environment. This entails employing monitoring tools and leveraging cloud automation capabilities to monitor the cloud infrastructure, detect events, and promptly respond to them. By implementing a dynamic response mechanism, you can quickly address issues, optimize resource utilization, and proactively manage the performance and security of your cloud-based systems.
Incorporating these principles into your cloud governance model will help you establish a robust framework that supports compliance, aligns with business objectives, promotes collaboration, ensures controlled change management, and enables dynamic responses to events in the cloud environment.
Importance of Cloud Governance
Cloud governance is essential for controlling issues, mainly in terms of costs, security, and asset performance. Due to constant changes in the cloud landscape, businesses must stay relevant and competitive.
Due to the change in IT infrastructure, which was traditionally equipment and hardware, the focus was just on procuring the right machinery and setting the budget for the operation and maintenance costs. But with the on-demand cloud services and pay-as-you-go pricing model, it is hard to keep track of the total spending, and before you know it, a small fortune would have been drained away from the total costs.
For cost control, cloud governance strategies ensure everyone has a set agenda and follows the game plan to control costs. This step is paramount in controlling and monitoring the cloud environment and ensuring operations are conducted in compliance.
Challenges in Cloud Governance
Here are some of the biggest challenges encountered when an organization sets out to establish cloud governance:
- Generally, organizations do not establish or set aside resources for ensuring the accountability and safeguarding of confidential information in the cloud
- When organizations are involved in decision-making about leveraging cloud resources, the IT department is not kept in the picture or consulted.
- Various IT functions do not have the complete picture or accountability of the cloud resources utilized.
- Organizations emphasize encryption but are not implementing it on protective apps
- Lack of proper control over employees and third parties in handling confidential cloud data governance makes establishing compliance difficult.
- Organizations increase dependency on cloud apps without undergoing the required security training.
- Lack of security layers like multi-factor authentication for access to sensitive data
Principles of Cloud Governance
For the governance of your cloud environment, there are a few principles to be followed:
1) Operational Governance
This comprises cost-cutting measures, the primary focus of which is to identify and eliminate unused assets and set up time slots for instances in the various stages of development, testing, and QA.
2) Performance Management
This comprises optimizing assets for their workloads, upgrading or downgrading assets based on changing requirements, and effectively storing data while keeping costs in mind.
3) Security Management
The latest governance principles for cloud-based solutions look at the various nuances of cloud security governance and emphasize the importance of encryption, control access, audit trails, application access rules, and monitoring nefarious activity.
Cloud Governance Best Practices
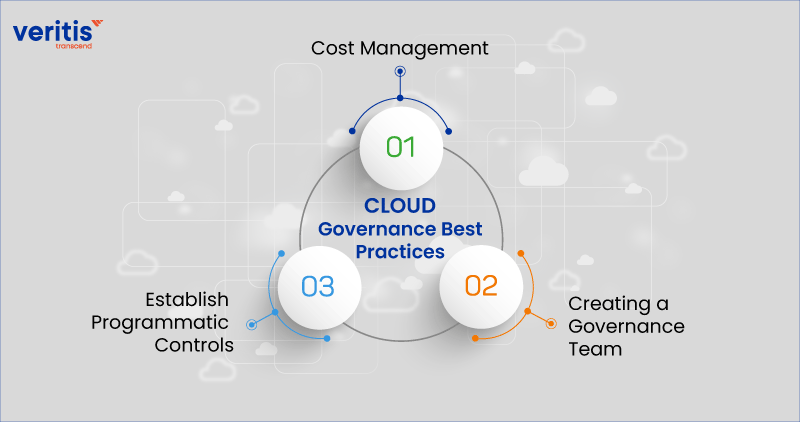
The latest governance principles for cloud-based solutions look at the various nuances of cloud security governance and emphasize the importance of encryption, control access, audit trails, application access rules, and monitoring nefarious activity.
1) Cost Management
One of the topmost concerns while moving to the cloud is cost control. It is difficult to juggle adoption pacing, performance and rising costs while migrating. Therefore, organizations must focus on cost control access across all cloud deployments.
2) Creating a Governance Team
For maximum resource utilization and effectiveness, a governance team must include employees from across the organization, including cloud engineers, security leads, and architects. This organization should track issues like the status of the software library, security policies, budgets, and operations. It is also a great opportunity to assess how each tool works for the company and look for an alternative.
3) Establish Programmatic Controls
After identifying your goals, objectives, and policies, the job is establishing protocols and processes for monitoring cloud usage. The next step is to understand which employees would have access to cloud assets, verify identity, manage the data encryption process, and keep track of financial aspects that establish the connection between compliance and employee accessibility.
Cloud Governance Vs. Cloud Management
One of the primary steps in establishing a quality multi-cloud strategy is defining the difference between governance and management. Organizations need to set rules and establish procedures for controlling, optimizing, operating, and offering security for cloud infrastructures while monitoring the applications that run in the cloud.
Cloud service management is involved in organizing, coordinating, and leveraging resources in accordance with regulatory measures, ensuring the fulfillment of the organization’s objectives.
Cloud governance is the art of defining, monitoring, and auditing rules and policies, setting processes, controlling resources, and auditing.
Benefits of Cloud Governance
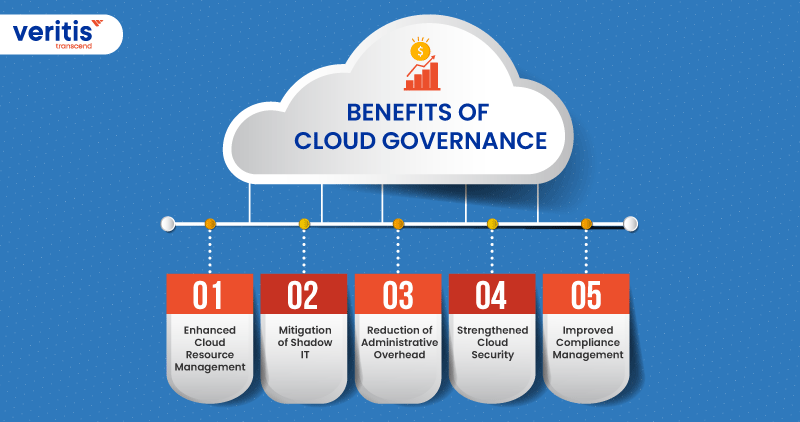
Cloud governance offers several benefits to organizations running critical services in the cloud. Here are a few ways it can positively impact your organization:
1) Enhanced Cloud Resource Management
You can effectively manage and allocate cloud resources by implementing cloud governance tools. Breaking down cloud systems into individual accounts representing departments, projects, or cost centers allows for improved cost control and visibility and limits the potential business impact of security issues. This segregation enables better resource allocation and optimization.
2) Mitigation of Shadow IT
Cloud governance tools help address the risks and costs associated with shadow IT. Employees turning to unauthorized cloud systems due to slow response from traditional IT services can lead to security vulnerabilities and increased complexity. A robust cloud governance framework enables employees to request cloud resources while applying relevant controls and maintaining organizational compliance. This reduces reliance on shadow IT and provides employees with authorized access to cloud systems within established constraints.
3) Reduction of Administrative Overhead
Implementing a comprehensive cloud governance program, supported by appropriate technology solutions, streamlines administrative processes. Rather than relying on manual methods like spreadsheets to track cloud accounts, costs, compliance issues, and resource access, cloud governance solutions provide a centralized platform for defining and applying policies across the entire cloud infrastructure. This reduces administrative overhead, minimizes the risk of non-compliant activities and unexpected costs, and improves operational efficiency.
4) Strengthened Cloud Security
Cloud governance models establish robust authentication strategies to protect information confidentiality, integrity, and availability. By implementing a governance framework, organizations gain visibility into sensitive information, ensure appropriate security controls are in place, and have assurance regarding data security regardless of where it resides or critical systems are deployed. This helps mitigate security risks and enhances the overall security posture of the cloud environment.
5) Improved Compliance Management
Another significant benefit of cloud governance is its ability to facilitate compliance management. By aligning cloud usage with regulatory requirements, industry standards, and internal policies, organizations can ensure adherence to compliance obligations. This includes data privacy regulations, industry-specific regulations, and internal governance frameworks. Cloud governance solutions help establish the necessary controls, processes, and visibility to effectively manage compliance and minimize potential risks.
Overall, cloud governance solutions empower organizations to optimize resource management, mitigate shadow IT risks, reduce administrative overhead, enhance cloud security governance, and ensure compliance with regulations and standards. Additionally, it enables organizations to adapt and evolve their cloud strategies to meet changing business needs, thereby maintaining a strong foundation for successful cloud operations.
Case Study: Strengthening Cloud Governance for an HR SaaS Provider
Veritis took a proactive approach in supporting a cloud-based HR solutions provider. By delivering end-to-end monitoring and support services rooted in a strong cloud governance framework, Veritis ensured security, compliance, and operational efficiency. The company implemented policies around identity and access management (IAM), usage monitoring, data handling, and incident response, thereby ensuring system reliability, regulatory alignment, and transparency across the client’s cloud infrastructure.
This case study serves as a reminder that cloud governance isn’t just about compliance. It’s a critical factor in sustaining performance and trust in SaaS-based environments, a fact that is often overlooked.
Read the complete case study: Monitoring Support Services for Provider of HR Solutions in Cloud.
Conclusion
Implementing cloud governance strategies begins by defining the team responsible for governance and audit-related tasks. This team will be crucial in overseeing and ensuring compliance within the cloud environment. Additionally, understanding how security policies will impact the adoption roadmap is essential. By considering the implications of security policies on cloud adoption, organizations can proactively address potential risks and ensure a secure cloud environment.
Finally, establishing cloud governance best practices for building the cloud governance framework is crucial. These cloud governance best practices should encompass resource management, access controls, monitoring, and change management processes. Effective cloud governance can be achieved by establishing a robust framework based on industry standards tailored to the organization’s requirements.
Veritis, the Stevie Award winner, is an IT consulting services provider that offers an effective cloud transition strategy, identifies the right tools, and ensures organizational change with cloud governance in place. Talk to our cloud architects today!
Get Expert Cloud Solutions – Schedule A Call
Also Read:
- Best Practices that Lead to Good Cloud Governance
- 5 Considerations for Drafting a Multi Cloud Strategy
- Cloud Vs On-Premise: IT Infrastructure Model of Your Choice?
- Cloud Adoption Strategy: Which Approach Would be Most Effective for Your Company?
- What is Cloud Security Posture Management?
