
Expanding work environment in the form of remote workforce and increasing cyberthreats are posing a serious challenge to the IT industry.
The situation is getting intense causing security risks within organizations, affecting their overall performance.
A shift to digital transformation is presenting the problem in a bigger picture, as operating digitally often gives scope for vulnerability to open/malicious attacks.
On the other side, organizations are moving to new software practices like DevOps at an increasing rate, considering the significance of collaboration in achieving success in digital journey.
So, security remains a key concern across this journey!
Worried?
IT industry presents a solution! As a security extension of DevOps, DevSecOps services assures security in a DevOps environment.
What is DevSecOps?

To secure an application from within, the term “DevSecOps” has lately gained popularity in the software development industry. DevSecOps, commonly referred to as Secure DevOps, is an expansion of DevOps that emphasizes security.
DevSecOps is a new model that is built on the principles of DevOps. DevSecOps solutions go beyond DevOps by including the security component in the SDLC. DevOps merged development and operations in a continuous, synchronized cycle. As a result, DevSecOps security tools are built into the cloud application from the beginning, significantly reducing the number of resources and time lost due to a cyberattack.
DevSecOps consulting focuses on integrating security from the early stage of the Software Development Life Cycle (SDLC), a strategy known as “Shifting Security to the Left,” in contrast to the DevOps paradigm, which assigns the security checks and testing to separate security teams in the later stages of SDLC. DevSecOps automation, in contrast to DevOps, is highly cautious about including security in all phases of software development training.
DevSecOps process in the SDLC is a cost-effective technique for protecting software against careless cyberattacks because integrating DevSecOps security tools at the end is expensive and challenging. Since the start of the software evolution, it has also enabled engineers to do controlled testing. A software/operational application’s vulnerabilities can be frequently monitored and quickly reported to developers thanks to built-in security. Additionally, periodically executing benefits of DevSecOps & risk tolerance and risk vulnerability studies increases reliance on the program and less on the software security shield installed on the perimeter. As a result, the necessity for developers to code with “security” in mind is reduced.
For the operations and development team to produce improved workflow and provide services quickly, the DevSecOps maturity model may be fabricated by manual procedures and integrating DevSecOps automation compatible tools into continuous integration and continuous delivery pipelines (DevSecOps CI/CD).
When developers and information security teams work together more collaboratively, automation is critical in establishing process value and efficiency. The primary focus of automation is the timely repetition of necessary development cycles. Additionally, it maintains a close working relationship between developer teams, keeps up with natively emerging technologies like microservices and containers, prevents operational interruptions, and incorporates security measures at vulnerable locations. Surprisingly, it reduces recurring manual errors and attempts that result in complex and challenging deliveries.
Useful link: What is DevSecOps Services?
DevOps Security Challenges
Despite its many advantages, DevOps introduces new dangers and cultural shifts that raise security issues that are usually beyond the scope of traditional security management tools and techniques. Automated software delivery and deployment into the cloud or as a container are frequently not supported by these conventional methods because they are too slow, expensive, or complex.
Attackers using cyberspace target privileged credentials used in DevOps. Privilege access management is among the most challenging security issues in DevOps settings. Privileged credentials used in DevOps processes must be strong and highly vulnerable to cyberattacks.
Attackers can gain complete access to DevOps pipelines, private databases, or even a company’s entire cloud once they have privileged credentials. Attackers are aware of this and are increasingly looking for sensitive information such as passwords, access keys, SSH keys, tokens, and other sensitive data such as certificates, encryption keys, and API keys. Additionally, in DevOps settings, attackers can use weak credentials to their advantage, leading to crypto-jacking, data breaches, and intellectual property destruction.
DevSecOps Security – DevOps, Cybersecurity Combine!

Success in today’s market scenario relies on the time taken to market and product release frequency. This is where DevOps made a difference in executing tasks under a collaborative culture at a rate faster than before with high responsiveness.
Bringing together two different teams – Development (Dev) and Operations (Ops) and platforms to deploy and test codes, DevOps contributed to the success of software delivery and enhanced business scalability.
The difference between DevOps and DevSecOps is that it initiates this engagement with the security team early in the SDLC. In the past, security was mostly dealt with during the SDLC Testing phase, when development was entirely finished, and the cost of addressing issues was significant. Including security from the beginning can lower the cost of patching vulnerabilities and increase the likelihood that security will be built rather than bolted on.
However, DevSecOps security remained separate, creating a dire need to integrate cybersecurity principles with the DevOps lifecycle to balance technology and possible risks. This integration should be included right from the beginning and continued across all phases of the product lifecycle as ‘security by default’, which is otherwise the ‘Azure DevSecOps Strategy’!
Useful link: DevOps outsourcing: Things to Know About Before Getting Started
How DevSecOps Help?

DevSecOps pipeline holds the ability to combine DevOps and cloud-native security applications, thus adding a protective cover to the operating environment, over and off the network. It brings together DevOps and security teams, and its success relies on creating a culture that encourages cross-team collaboration and innovation.
With the mindset that “everyone is accountable for security,” the DevSecOps process is a method of tackling IT security. It entails integrating security procedures into a company’s DevOps process. The objective is to integrate security into every phase of the software development process. DevSecOps maturity model indicates you shouldn’t save security for the SDLC’s end, contrary to its predecessor development methods.
If your business already uses DevOps, consider switching to AWS DevSecOps. DevSecOps pipeline is fundamentally built on the DevOps principle, which will support your case for switching. And by doing this, you’ll be able to assemble proficient individuals from many technical disciplines to improve your DevSecOps security procedures.
The big difference that DevSecOps automation makes can be realized only when the process outcomes and metrics are aligned with the organization’s security goals. These metrics can be the time taken to fix patches, speed-up coding, and testing processes, time to respond and recover, and more that are key to DevOps.
Security can no more be a separate entity, and DevSecOps consulting methodologies demand other teams stay aligned to security in their DevOps journey!
DevSecOps Best Practices
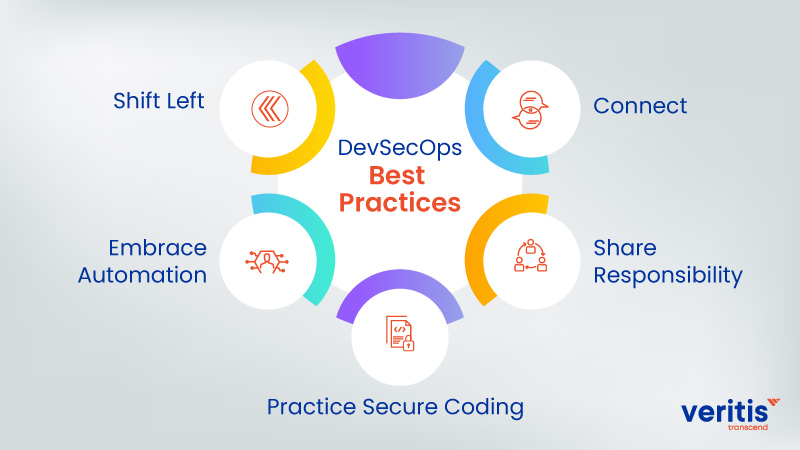
The following elements aid in and play a significant part in implementing DevSecOps.
1) Shift Left
Instead of waiting until the very end of the delivery chain, the shift-left testing strategy recommends building security into your apps at the initial stage. You can detect potential vulnerabilities and start working on fixing them immediately, which obviously benefits of DevSecOps. Also, fixing faults will be more affordable for you the earlier you uncover them. It’s terrific practice, but it does have its share of drawbacks. Shifting left may momentarily interfere with your current DevOps process workflow, which is a regular difficulty. While overcoming this challenge may be challenging, adopting DevSecOps services will help you move leftover time.
2) Embrace Automation
Automation plays a significant role in DevSecOps tools, just like in DevOps. Automation of security is required in a CI/CD environment to keep pace with the delivery of your code. This is particularly true for big businesses where developers frequently push different code versions to production.
While automating security testing, it’s crucial to take care. Making incorrect automatic tool selections can have adverse effects. Most developers use static application security testing (SAST) technologies to continuously monitor and spot any possible problems early in the development process. However, the success of your company’s products depends on selecting the appropriate security automation tool and implementing it.
3) Practice Secure Coding
The ability to create software that is highly resistant to flaws is the evident significance of secure coding. Compromising a company’s confidential information is just one of the many software security hazards that can arise from not using secure coding practices. Because of this, your developers must have the necessary skills—even if doing so requires investing time and money. Setting and following coding standards is also beneficial because it aids developers in producing clean code.
4) Share Responsibility
One of the guiding concepts of DevSecOps is collaboration across the development, security, and operations teams. However, this is insufficient. The C-Suite and the entire firm must support and buy into a DevSecOps program for it to succeed.
5) Connect
Eliminating communication silos and fostering team collaboration are vital components of a DevSecOps program. In addition, a DevSecOps program should involve all stakeholders in important decisions, ensure security is prioritized, and ensure everyone knows their roles.
Useful link: All You Need to Know About DevSecOps and its Implementation
Conclusion
DevSecOps can enhance the Agile development paradigm by providing tools for the proper modifications in the Agile environment to increase software delivery efficiency. It only requires setting up release management and CI/CD technologies to implement DevSecOps solutions.
To prevent cyberattacks and security violations, it is essential to take protection while coding. DevSecOps best practices must be strictly followed to reduce security breach risks and prevent identity theft. Additionally, it pushes programmers to build secure, streamlined code that adheres to industry standards.
Is your organization DevSecOps ready?
For your DevSecOps strategy, Veritis, the Stevie Award winner for DevOps solutions, delivers the best-customized solution. Veritis provides various technology services for your company at a cost-effective solution. Contact us to embrace productivity with the best DevSecOps tools.
Got Questions? Schedule A Call
Also Read:
- Global DevSecOps Market Poised for a 4-fold Rise in 2018-23
- DevSecOps: An Ultimate Defense To Organization’s Software Security
- DevSecOps Solution to Cloud Security Challenge
- DevOps Security: Challenges and Best Practices
- Derive ‘ROI’ from ‘DevOps’: An Overview of Performance and Metrics
- What are the best DevSecOps practices for security and balance agility?