Picture this scenario. Your enterprise operations are humming along smoothly when suddenly your primary customer portal crashes. Revenue streams halt. Customer satisfaction plummets. Stock prices tumble. Within minutes, millions in potential revenue evaporate while your IT teams scramble to understand what happened. What you are experiencing is the devastating reality of a denial of service and distributed denial of service assault on your digital infrastructure.
For senior leadership, the difference between DoS attack and DDoS attack is all about a business survival imperative. A single DoS attack type may slow down operations. Still, a coordinated application layer DDoS attack can overwhelm critical systems, leaving no room for recovery without an effective DDoS incident response plan.
- DoS and DDoS attacks pose a direct threat to revenue, customer trust, and market share, placing CEOs, CIOs, and CTOs under immense pressure to ensure business continuity.
- Studies reveal that DDoS downtime can exceed $300K per hour, amplifying brand damage and eroding stakeholder confidence, which becomes a top concern for CFOs and CMOs.
- Mitigating these risks requires advanced cybersecurity solutions, including AI driven monitoring, cloud based scrubbing, and tested DDoS mitigation strategies.
- Boards and CEOs increasingly rely on trusted cybersecurity consulting services and proven cybersecurity service providers to deliver enterprise cybersecurity solutions that ensure long term resilience and uninterrupted operations.
We have seen firsthand how unprepared organizations crumble under these threats. The DoS vs DDoS attack domain has evolved into a sophisticated battlefield where outdated defenses collapse. By adopting modern strategies and partnerships, you not only protect millions in revenue but also position your organization’s cybersecurity posture as a model for the industry.
Talk to Our Security Experts Today
What is a DoS Attack?
A Denial of Service (DoS) attack is the digital equivalent of a single protester blocking your company’s main entrance. Unlike large scale distributed campaigns, DoS attack types originate from a single source but are no less damaging. The attacker overwhelms your systems with malicious traffic, consuming bandwidth, processing power, or memory, until legitimate users are effectively locked out.
What makes a denial of service attack dangerous is its simplicity. With minimal resources, attackers can cause outsized disruption, especially for organizations without advanced cybersecurity solutions in place.
Common DoS Attack Types Executives Should Know
- Volume Based Floods: High levels of traffic saturate network bandwidth.
- Protocol Exploits: Weaknesses in communication protocols are manipulated to exhaust server resources.
- Application Layer Exploits: Targeted requests crash critical applications, mirroring the tactics later amplified in application layer DDoS attacks.
- Buffer Overflow Attacks: Excessive data overwhelms software, causing systems to malfunction or shut down.
Each of these DoS attack types requires specialized defenses, monitoring, and an incident playbook aligned with enterprise risk frameworks.
The Business Impact
The consequences of a DoS attack extend far beyond temporary downtime. When critical services fail:
- Revenue suffers as e commerce portals and customer platforms become inaccessible.
- Customer trust erodes, and loyalty shifts to competitors who can guarantee reliability.
- Market positioning deteriorates, especially during peak business cycles.
To prevent these outcomes, enterprises increasingly depend on cybersecurity consulting services and trusted cybersecurity service providers to implement resilient controls. These partnerships enable organizations to proactively identify vulnerabilities, respond swiftly to threats, and maintain operational continuity.
By embedding enterprise cybersecurity solutions into infrastructure, executives ensure continuity even when single source threats escalate.
Useful Link: How a Security Operations Center (SOC) Can Safeguard Your Business From Cyber Threats
What is a DDoS Attack?
A Distributed Denial of Service (DDoS) attack adopts the concept of a traditional DoS assault and magnifies it exponentially. Unlike a single source disruption, the difference between DoS attack and DDoS attack lies in scale, coordination, and complexity. DDoS campaigns deploy vast networks of compromised devices, known as botnets, to overwhelm enterprise systems with traffic that appears legitimate but is devastating in volume. The business impact of DDoS attack includes lost revenue, customer churn, and long term brand damage.
These attacks enlist thousands of unsuspecting devices: home computers, IoT sensors, smartphones, and even unsecured enterprise servers. The distributed nature of the assault makes it nearly impossible to block traffic based solely on origin, as malicious requests are dispersed across global networks.
The Modern DDoS Landscape
The denial of service and distributed denial of service incidents have evolved alongside the digital economy:
- Botnets leverage cloud resources and global bandwidth for massive disruption.
- Attacks target multiple layers simultaneously, networks, infrastructure, and business critical applications.
- Application layer DDoS attacks focus on web portals, databases, and APIs with carefully disguised traffic that looks like genuine user activity.
Why This Matters for Enterprises
For executives, application layer DDoS attacks are particularly concerning. They bypass conventional defenses by imitating normal user behavior, making them harder to detect through standard monitoring. Left unchecked, they can paralyze digital services, disrupt customer access, and erode stakeholder confidence within minutes.
Addressing these risks requires:
- Proactive DDoS mitigation strategies built into enterprise infrastructure.
- A tested DDoS incident response plan aligned with business continuity requirements.
- Investment in advanced cybersecurity solutions from trusted cybersecurity service providers who deliver scalable, AI driven defenses.
- Ongoing partnerships with cybersecurity consulting services to ensure your organization adapts to emerging attack vectors.
Ultimately, protecting against DDoS threats is not all about technology; it is about safeguarding revenue, reputation, and long term resilience through modern enterprise cybersecurity solutions.
Key Stats Every Executive Should Know About DoS vs DDoS Attacks
1) Attack Volume and Scale
- 5 million DDoS attacks blocked in Q1 2025, a 358% increase YoY.
- Of those, 700 were hyper volumetric attacks (exceeding 1 Tbps or 1 Bpps). (Source: Cloud Flare)
2) Largest DDoS Incident Throughput
- The biggest recorded attack in early to mid 2025 had a bandwidth of 3,119.977 Gbps.
- That same report shows an attack with 1,497.216 million packets per second (Mpps). (Source: Net Scout)
3) Trend in Web (Application Layer) DDoS Attacks
- Radware reports a 550% increase in Web DDoS attacks, with a corresponding doubling in frequency, volume, and duration. (Source: Radware )
4) Attack Enablement and Volume Surge
- Behind the scenes, the “tools ” for DDoS (amplifiers, protocol exploits) have grown exponentially. Early 2025 data suggests a 350% increase in attack volume (Gbps/Tbps scale) compared to earlier in the decade.
5) Global Threat Intelligence Scope
- Over 15,600 Autonomous System Numbers (ASNs) were detected involved in DDoS activity across 205 countries/territories.
- Distribution of attack duration: 52.5% of attacks lasted 5 to 15 minutes; only 10% lasted over an hour. (Source: Net Scout)
Types of DoS and DDoS Attacks
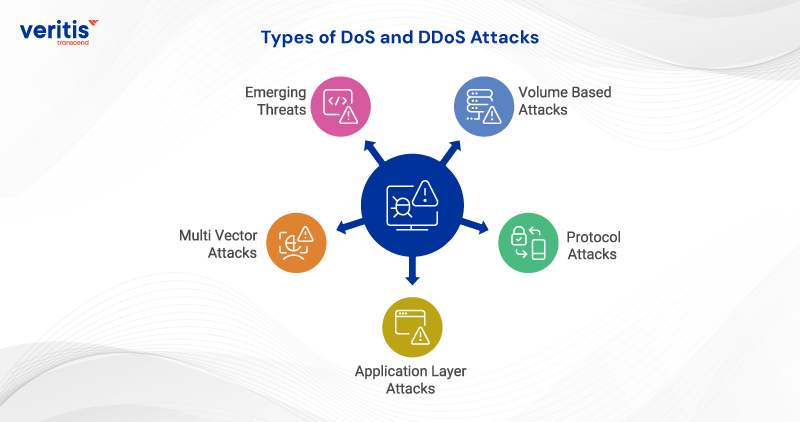
Executives evaluating DoS vs DDoS attack risks should understand the most common categories. The difference between DoS attack and DDoS attack lies in scale and complexity, but both exploit different vectors to disrupt business continuity.
1) Volume Based Attacks
Flood bandwidth with massive traffic (e.g., UDP or ICMP floods). Disrupts online transactions and services. Requires scalable enterprise cybersecurity solutions and cloud based filtering.
2) Protocol Attacks
Exploit server resources and network protocols (e.g., SYN floods, Ping of Death). Firewalls and load balancers often crash. Mitigation relies on cybersecurity consulting services and intelligent monitoring.
3) Application Layer Attacks
The most sophisticated application layer DDoS attacks mimic regular requests (e.g., HTTP floods, DNS queries). It is hard to detect without AI driven defenses and a tested DDoS incident response plan.
4) Multi Vector Attacks
Combine multiple tactics at once, creating maximum disruption. Effective DDoS mitigation strategies for large organizations involve demand layered, automated defenses.
5) Emerging Threats
Botnets built from IoT and cloud systems amplify denial of service and distributed denial of service risks. Trusted cybersecurity service providers deliver the intelligence and advanced cybersecurity solutions needed to stay ahead.
Useful Link: Securing Digital Transactions: Addressing Unique Challenges for Cybersecurity in Banking
What is the Difference Between DoS and DDoS?
A DoS vs DDoS comparison enterprise operations impact shows localized disruption versus enterprise wide outages.
| Aspect | DoS Attack | DDoS Attack |
| Definition | A denial of service attack from a single source that overwhelms a system with traffic. | A distributed denial of service attack using multiple compromised devices (botnets) to flood systems. |
| Scale and Complexity | Limited in scale, making it easier to detect and stop. | Massive scale; traffic appears from legitimate global sources. |
| Attack Vectors | A single attacker exploits bandwidth, protocols, or applications (DoS attack types like floods or buffer overflows). | Multi vector, blending volume, protocol, and application layer DDoS attacks simultaneously. |
| Mitigation | Managed through rate limiting, IP blocking, and basic filtering. | Requires advanced cybersecurity solutions, including traffic analysis, cloud scrubbing, AI based detection, and DDoS mitigation strategies. |
| Response Plan | These issues are often resolved quickly by IT teams with limited resources. | Requires a coordinated DDoS incident response plan with enterprise wide defenses. |
| Business Impact | Localized downtime; minimal financial loss if resolved fast. | Sustained downtime; studies show DDoS downtime costs enterprise organizations an average of $300 per hour. |
| Executive Concern | Tactical disruption; manageable with basic defenses. | Strategic threat to revenue, customer trust, and brand reputation requires trusted cybersecurity consulting services and a reliable cybersecurity service provider for enterprise cybersecurity solutions. |
How to Prevent DoS and DDoS Attacks?
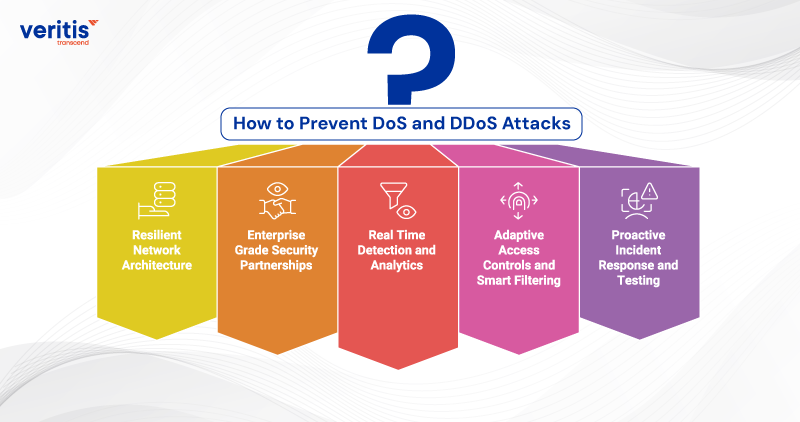
Executives today must treat the difference between DoS attack and DDoS attack comparison as a board level concern. Defenses must cover infrastructure, applications, and people, combining technology with trusted cybersecurity service provider expertise. Below are five critical strategies for modern enterprises.
1) Resilient Network Architecture
Building resilience is the first line of defense against DoS attack types and distributed campaigns. Over provisioned bandwidth, redundant links, and global server distribution minimize disruption. Segmentation ensures critical assets remain isolated during denial of service and distributed denial of service incidents.
2) Enterprise Grade Security Partnerships
Modern enterprises cannot operate independently. Partnering with cybersecurity consulting services and experienced cybersecurity service providers delivers scalable defenses like CDNs, anycast routing, and cloud based scrubbing centers. These partnerships embed enterprise cybersecurity solutions designed to withstand evolving DoS vs DDoS attack vectors.
3) Real Time Detection and Analytics
Advanced cybersecurity solutions use AI driven traffic analysis to identify anomalies before they escalate into application layer DDoS attacks. Continuous monitoring of applications, APIs, and databases ensures that threats are detected early and contained quickly, thanks to automated triggers from the DDoS incident response plan.
4) Adaptive Access Controls and Smart Filtering
Mitigation today goes beyond static firewalls. Intelligent rate limiting adjusts dynamically to abnormal request surges, protecting against both DoS attack vs DDoS attack disruptions. Geo blocking, multifactor session validation, and behavioral analysis help differentiate genuine users from malicious traffic in application layer DDoS attacks.
5) Proactive Incident Response and Testing
A living DDoS incident response plan is key to business continuity. Regular simulation drills, red team exercises, and executive tabletop reviews ensure readiness. Coordinated response frameworks supported by DDoS mitigation strategies protect revenue streams, customer trust, and shareholder confidence.
Key Characteristics of DoS and DDoS Attacks
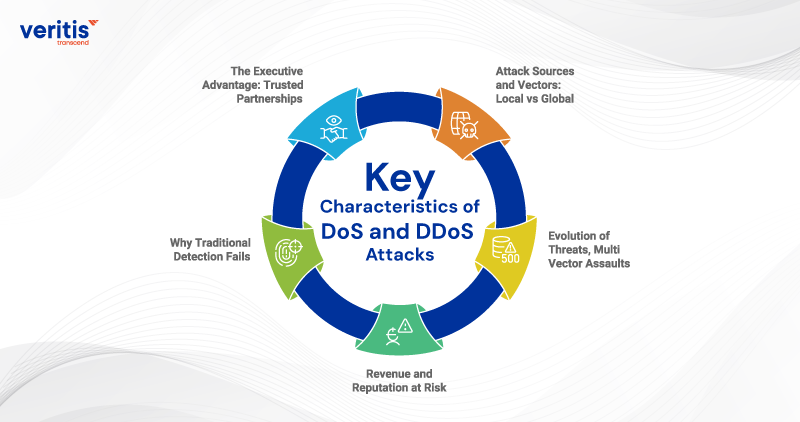
The difference between a DoS attack and a DDoS attack is clear: one is a localized disruption, the other a coordinated assault. For executives, these attacks underscore the need for effective risk mitigation strategies to protect revenue, customer trust, and shareholder value.
1) Attack Sources and Vectors: Local vs Global
- DoS attack types use single, identifiable sources.
- DDoS attacks are distributed worldwide, blending multiple attack vectors.
- Mitigation requires advanced cybersecurity solutions beyond basic firewalls.
2) Evolution of Threats, Multi Vector Assaults
- Modern denial of service and distributed denial of service incidents combine bandwidth floods, protocol exploits, and application layer DDoS attacks.
- They strike infrastructure and business logic simultaneously.
- Defense requires layered DDoS mitigation strategies.
3) Revenue and Reputation at Risk
- DoS events often cause short term, localized downtime.
- DDoS attacks trigger enterprise wide outages, halting transactions and customer access.
- Executives need a tested DDoS incident response plan to protect brand equity and financial stability.
4) Why Traditional Detection Fails
- Application layer DDoS attacks mimic legitimate user traffic.
- Legacy monitoring tools miss these subtle patterns.
- AI driven analytics within enterprise cybersecurity solutions are now crucial.
5) The Executive Advantage: Trusted Partnerships
- Many organizations struggle with false positives and alert fatigue.
- Partnering with cybersecurity consulting services and a proven cybersecurity service provider ensures tailored defenses, continuous monitoring, and board level risk alignment.
How to Protect Against DoS and DDoS Attacks?
Executives need to treat DoS vs DDoS attack defense as a board level investment, not a technical afterthought. The right strategy blends infrastructure, intelligence, and trusted partners. AI for DDoS detection enables faster identification of attack patterns and a real time automated response.
1) Build Resilient Infrastructure
Over provision bandwidth, segment networks, and distribute data centers. This limits the blast radius of DoS attack types and strengthens defenses against denial of service and distributed denial of service campaigns.
2) Deploy Enterprise Grade Mitigation
Adopt layered DDoS mitigation strategies: intelligent routing, cloud scrubbing, and on premise appliances. A single tool won’t stop DoS attack vs DDoS attack disruptions; defenses must work in concert.
3) Embrace AI Detection
Invest in advanced cybersecurity solutions with machine learning. These detect application layer DDoS attacks disguised as regular traffic and trigger automated responses that reduce downtime costs.
4) Test and Evolve Your Response Plan
A DDoS incident response plan is only as strong as its last test. Run simulations with IT, security, and leadership teams to ensure fast decisions, clear escalation, and minimal business disruption.
5) Choose the Right Partners
Partner with proven cybersecurity consulting services and a trusted cybersecurity service provider like Veritis. These alliances deliver 24/7 monitoring, global threat intelligence, and tailored enterprise cybersecurity solutions aligned with compliance and business continuity.
Useful Link: How Are AI Automation Tools in Cybersecurity Transforming Enterprise Defense?
Advanced Mitigation Techniques
The difference between DoS attack and DDoS attack demands adaptive defenses that blend scale, intelligence, and automation. Effective incident response for DDoS threats requires rapid coordination across IT, security, and business teams.
1) Cloud Based Scrubbing and Protection
- Cloud driven DDoS mitigation strategies absorb massive traffic before reaching origin servers.
- Anycast routing and global scrubbing centers stop threats closer to the source.
- Choose a cybersecurity service provider with proven scale and integration into enterprise cybersecurity solutions.
2) Behavioral Analytics with Machine Learning
- Advanced cybersecurity solutions analyze user behavior to detect anomalies.
- Essential for spotting application layer DDoS attacks disguised as regular traffic.
- Reduces false positives while clarifying the DoS vs DDoS attack detection challenge.
3) Real Time Automated Response Systems
- Automated defenses detect, react, and adapt instantly to evolving patterns.
- A strong DDoS incident response plan ensures coordination across IT, security, and business teams.
- Manual only responses are too slow to contain modern threats.
4) Multi Layered Enterprise Cybersecurity Solutions
- DoS attack types hit network and protocol layers.
- Application layer DDoS attacks disrupt APIs, databases, and customer portals.
- Layered enterprise cybersecurity solutions ensure resilience across all vectors.
5) Expert Consulting and Strategic Partnerships
- Work with cybersecurity consulting services like Veritis for strategy, testing, and optimization.
- Engage a trusted cybersecurity service provider for 24/7 monitoring and global intelligence.
- Partnerships turn DDoS mitigation strategies into long term business enablers.
Business Continuity Considerations
Business continuity relies on proactive DoS vs DDoS mitigation techniques to balance cost, recovery, and compliance.
1) Cost Analysis
- DDoS downtime costs enterprise organizations an average of $300K+ per hour in lost revenue.
- Direct costs: recovery operations, remediation tools, regulatory penalties.
- Indirect costs: brand damage, customer churn, investor concern, and competitive disadvantage.
- A DoS vs DDoS comparison of financial impact guides smarter risk management and budget allocation.
- Balancing investment in advanced cybersecurity solutions with potential loss scenarios is a board level decision.
2) Recovery Planning
- Business continuity planning for denial of service and distributed denial of service attacks must cover:
- Technical restoration (infrastructure, applications, and data).
- Clear communication protocols for customers, regulators, and stakeholders.
- Defined escalation and decision making chains.
- Recovery objectives must account for the scope of DoS attack types and the scale of DDoS attack vs DoS attack scenarios.
- Effective recovery requires coordination between IT, business units, and external cybersecurity service providers.
- Metrics and simulations validate the readiness of the DDoS incident response plan and ensure alignment with compliance standards.
3) Regulatory and Compliance Impact
- Extended downtime may trigger regulatory scrutiny and financial penalties, especially in industries like banking, healthcare, and telecom, where Cybersecurity in Banking is subject to particularly stringent oversight.
- Cybersecurity consulting services help align continuity planning with compliance standards such as GDPR, HIPAA, and PCI DSS.
- Executives must ensure enterprise cybersecurity solutions not only mitigate threats but also meet audit, reporting, and governance requirements.
Case Study: Mitigating DDoS Attacks for a Global Fintech Firm
A global fintech enterprise was frequently disrupted by DDoS attacks that overwhelmed its public facing platforms, impacting service availability and customer trust. The firm turned to Veritis to design a resilient security strategy. Veritis deployed a layered defense that included cloud based DDoS mitigation, web application firewalls, intelligent traffic filtering, and real time threat monitoring. This comprehensive approach ensured uninterrupted digital services, enhanced incident response readiness, and aligned the client’s infrastructure with industry compliance standards. As a result, the organization significantly reduced downtime and improved operational resilience across its global platforms.
The complete case study is available here: Global Financial Firm Secures Infrastructure Against DDoS Threats.
Conclusion
The difference between DoS attack and DDoS attack represents more than technical distinctions. These threats pose fundamental mitigating DDoS risks to business operations, customer relationships, and competitive positioning. Executive leadership must understand these risks and invest appropriately in comprehensive protection strategies.
The evolution of denial of service and distributed denial of service attacks demands sophisticated enterprise cybersecurity solutions that address multiple attack vectors simultaneously. Organizations cannot rely on traditional network security approaches when facing modern DDoS attack scenarios that combine volume based assaults with application layer exploitation techniques.
Effective DDoS mitigation strategies require integration between network infrastructure, security technologies, cloud services, and incident response procedures. The complexity of modern attack scenarios demands partnership with experienced cybersecurity consulting services that can provide specialized expertise and scalable mitigation capabilities.
Business leaders who prioritize cybersecurity as a strategic enabler rather than a cost center create competitive advantages through reliable service delivery, customer trust, and operational resilience. The DoS vs DDoS mitigation difference ultimately determines whether organizations thrive or struggle in our increasingly digital business environment.
Contact Veritis today to discuss how our enterprise cybersecurity solutions can transform your organization’s security posture from reactive vulnerability to proactive resilience. Together, we’ll build defense strategies that protect your digital assets while enabling continued business growth and innovation.