Every person who works for a company, whether they use computers or are in charge of keeping things safe, plays a part in protecting the company from cyber-attacks. The things they do, or don’t do, can make a big difference in whether the company stays safe or gets attacked. If the company gets attacked, it can hurt their reputation and cost them a lot of money. So, everyone needs to do their part to keep the company secure.
Cybercrime is a rapidly growing type of crime that affects businesses across all industries. Staying informed about the latest cybersecurity trends and best practices is important to avoid your company’s name appearing in the news due to a security breach.
Cyber threats are a real problem in today’s digital world, and it’s crucial to have a strong cybersecurity solution to protect yourself. Cyber security services assessment helps businesses evaluate their online security, find weaknesses and risks, and create a comprehensive plan to stay secure. It also helps prevent cyber attacks and secure information.
Moreover, organizations must follow cyber security services to protect their data and customer information from online threats. Educating employees about cybersecurity risk is important, as it helps them recognize and prevent cyber attacks. Managed security services experts assist businesses in avoiding vulnerable cyber-attacks.
What Are the Reasons Behind Data Breaches Occurring?

A data breach occurs when protected or confidential data is accessed, exposed, lost, or stolen without authorization. Data breaches can occur through various means, but the primary causes typically include:
1) Criminal Hacking
This is the most common cause of data breaches, and it involves cybercriminals using malicious software, such as malware or ransomware, to gain unauthorized access to a company’s computer systems. After gaining unauthorized access, attackers can steal sensitive data, including customer Personally Identifiable Information (PII), financial details, or valuable trade secrets for cybersecurity business.
2) Human Error
Human error is another common cause of data breaches. This can include employees clicking on malicious links in phishing emails, misconfiguring network security settings, or losing laptops or USB drives containing sensitive data.
3) System Glitches
System glitches can also lead to cybersecurity breaches. This can happen when software or hardware vulnerabilities or errors in data processing procedures occur.
4) Physical Theft
Data breaches can sometimes occur due to the physical theft of data-carrying devices, such as laptops, hard drives, or USB drives.
According to the 2023 Verizon Data Breach Investigations Report, the top three causes of data breaches were:
Criminal Hacking: 45% of breaches
Human Error: 22% of breaches
System Glitches: 14% of breaches
The report also found that the average cost of a data breach in 2023 was USD 4.24 million.
Here are some guidelines to secure your data against breaches:
- Use strong passwords and change them regularly.
- Be careful about what information you share online.
- Stay cautious of phishing emails and other fraudulent scams.
- Keep your software up to date.
- Back up your data regularly.
By implementing these practices, you can enhance your cybersecurity tips and lower the chances of a data breach.
Useful link: Security Breaches Rising Exponentially; Weak Authentications Exploited
Where Does Your Data End Up, and Who Has Access to It?
To effectively protect something, you must first be aware of its existence. That’s why it’s important to understand your data and its level of sensitivity clearly.
It would be best to have a clear picture of how your data is being utilized, who has access to it, and where it is being shared. Take the time to gather data from all sources, including different devices and online services, and organize them based on their sensitivity and who can access them.
Once you have this information, you can develop and implement best practices, programs, and rules to safeguard your data.
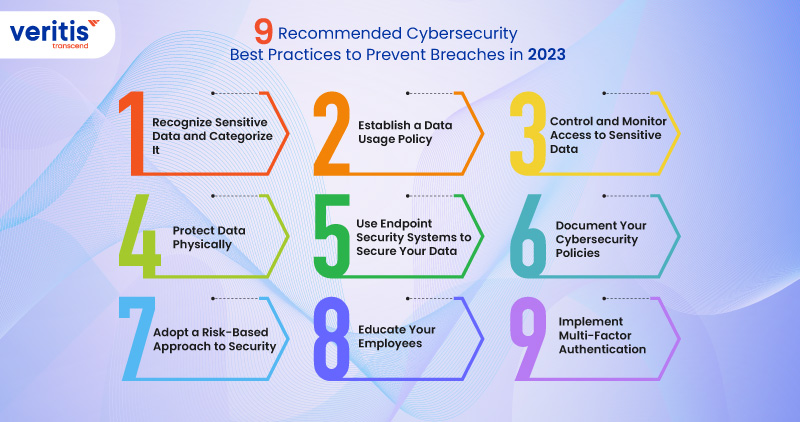
9 Recommended Cybersecurity Best Practices to Prevent Breaches in 2023
1) Recognize Sensitive Data and Categorize It
It’s crucial to clearly understand the types of information you possess to protect your data effectively. Begin by allowing your security team to scan your data storage areas and generate reports on their findings. Then, they can organize the data into different groups based on its value to your organization.
Keep the categorization updated as data changes or is shared. Establishing rules that prevent users from falsely altering the data’s classification is also important. Only authorized users should be able to upgrade or downgrade the data classification.
2) Establish a Data Usage Policy
Simply classifying data is not enough; it’s important to create a policy that outlines how data should be accessed, who can access it based on its classification, and guidelines for proper data usage. Control user access to specific areas and deactivate access when it’s no longer needed.
Remember to enforce strict consequences for any violations of the policy.
3) Control and Monitor Access to Sensitive Data
It’s important to provide appropriate access privileges to authorized users. Follow the cybersecurity principles of least privilege, which means granting users only the necessary permissions required to perform their tasks. This ensures that the right people can access the data for cybersecurity trends.
Here are a few essential permission levels to consider:
A) Full Control: Users have complete data ownership, allowing them to store, access, modify, delete, and manage permissions.
B) Modify: Users can access, modify, and delete data.
C) Access: Users can access the data without making changes or deleting it.
D) Access and Modify: Users can access and make changes to the data but cannot delete it.
Controlling and monitoring access this way can reduce the cyber supply chain risk management of unauthorized individuals accessing sensitive data.
4) Protect Data Physically
Remember the physical security of your data. Make sure to lock your workstations when they’re not in use to prevent unauthorized access or theft of devices. This helps keep your hard drives and other storage components secure for cybersecurity business.
Another important practice is setting up a password in your computer’s BIOS (Basic Input/Output System) to prevent hackers from accessing your operating system. Pay attention to the security of devices like USB flash drives, Bluetooth devices, smartphones, tablets, and laptops.
Useful link: 8 SaaS Security Best Practices to Secure Applications
5) Use Endpoint Security Systems to Secure Your Data
The endpoints in your network, such as servers and workstations, are constantly targeted by threats. Establishing a strong endpoint security infrastructure is important to minimize the cyber supply chain risk management of data breaches. Here are some steps you can take:
A) Install Antivirus Software: Make sure to have antivirus software on all your servers and workstations. Regularly scan your systems to detect and remove malware, such as ransomware.
B) Use Antispyware: Spyware is malicious software that collects personal information without your knowledge. Install antispyware tools to block and remove these threats.
C) Employ Pop-Up Blockers: Pop-ups can be annoying and potentially harmful. Use pop-up blockers to prevent unwanted programs from running on your system.
D) Set Up Firewalls: Firewalls act as a protective barrier between your data and cybercriminals. Install a firewall on your network, and consider using internal firewalls for added security.
Implementing these measures can enhance your endpoints’ security and better protect your valuable data.
6) Document Your Cybersecurity Policies
It’s insufficient to rely on verbal communication or assumptions regarding cyber security services. Take the time to document your cybersecurity practices, cybersecurity policies, and protocols in detail. This documentation will help facilitate online training, provide checklists, and ensure the transfer of specific knowledge to your employees and stakeholders.
7) Adopt a Risk-Based Approach to Security
Consider the risks your company may encounter and how they can impact employee and customer data. Conduct thorough risk assessments to:
- Determine the location and nature of your assets.
- Assess the current state of your cybersecurity risk.
- Develop an effective security strategy.
Adopting a cyber supply chain risk management ensures cybersecurity compliance with regulations and protects your organization against potential data leaks and cybersecurity breaches.
8) Educate Your Employees
Educate all employees about your organization’s cybersecurity tips and cybersecurity policies. Conduct regular training sessions to inform them about any new protocols and changes in the industry. Use real-life examples of cybersecurity breaches to illustrate the importance of cybersecurity for business. Encourage employees to provide feedback on your current security system.
9) Implement Multi-Factor Authentication
Multi-factor authentication (MFA) offers enhanced data security by adding an extra layer of protection during account login. Even if someone knows your password, they still need to provide additional verification, like a security token, fingerprint scan, voice recognition, or mobile phone confirmation. This significantly increases hackers’ difficulty in gaining unauthorized access to your accounts.
Conclusion
Cybersecurity best practices go beyond the steps mentioned earlier. They include regularly backing up your data, encrypting it when it’s being transmitted and when it’s at rest, and promoting safe password practices.
However, it’s important to realize that cybersecurity for business is not about eliminating all threats, which is impossible. Ignoring it is also not a wise choice. By adopting the right security measures, you can significantly reduce the risks involved and protect your data to a great extent.
Implementing cybersecurity best practices is vital for protecting your business from data breaches. Educating employees, establishing strong policies, monitoring access, implementing endpoint security, and conducting risk assessments are key to enhancing security.
Veritis, the Stevie Award winner, provides tailored solutions, including risk assessments, security training, data protection, and incident response planning to mitigate risks and protect your business. Prioritizing cybersecurity and partnering with trusted experts like Veritis ensures data protection and upholds customer trust.
Got Questions? Schedule A Call
Also Read:
- 9 Data Security Best Practices for Your Business
- Top 5 Tech Trends CIOs Must Focus on for 2023
- Things CTO Needs to Consider Selecting a Cloud Network Security Solution
- What is Security as a Service (SECaaS)?
- DevSecOps Implemention : Enhancing Security for an Energy Services Firm
- DevSecOps – The DevOps Answer to Cybersecurity Challenges