
In every boardroom, one question persists: How can an enterprise stay resilient when digital threats grow smarter and faster every hour? For top executives, CEOs, CTOs, CIOs, CFOs, and all C-suite leaders, the real solution is not more manual oversight but smarter orchestration. What is SOAR in Cybersecurity, which stands for Security Orchestration, Automation, and Response, is the cornerstone of this transformation.
It goes beyond traditional tools to unify people, processes, and intelligent security orchestration automation and response into one agile defense system, powered by the right SOAR security tools, advanced cybersecurity automation tools, and a resilient organizational cybersecurity strategy.
- SOAR cyber security breaks down silos, connecting your entire ecosystem of SOAR security tools into a single, AI optimized command center that provides CEOs and CTOs with unified visibility across their digital estate.
- It maximizes the full potential of security orchestration automation and response, reducing human response times from days to seconds, empowering CIOs and C-suite leaders to act decisively when every second counts.
- By embedding cybersecurity automation tools, you strengthen every analyst’s capacity to neutralize threats with precision, assuring CFOs that security investments deliver measurable risk reduction.
- And it enhances your entire organizational cybersecurity strategy, shifting C-suite executives from reactive firefighting to proactive, data driven resilience that protects revenue, trust, and market position.
At Veritis, we do more than provide Cybersecurity Solutions; we’re engineer how your entire security ecosystem thinks and acts. Our cybersecurity services infuse AI into every layer of security orchestration, automation, and response, ensuring our clients stay ahead of every threat curve. When Fortune 500 leaders ask what absolute security looks like, they turn to Veritis.
Automate Your Cyber Defense Today
What is a SOAR?
Understanding What is SOAR in Cybersecurity is a board level priority for CEOs, CTOs, CIOs, CFOs, and every C-suite leader serious about resilience. At its core, SOAR, Security Orchestration, Automation, and Response, unifies scattered tools and teams into a single system that detects, analyzes, and responds to threats at machine speed.
What is a SOAR? It’s the solution to today’s complex threats that manual actions alone can’t match. SOAR cyber security breaks down silos between firewalls, intrusion detection, threat feeds, and more, integrating them into one SOAR security platform for real time clarity and control.
In a mature SOAR (Security Orchestration, Automation, and Response) cybersecurity setup, advanced security orchestration tools and cybersecurity automation tools automate triage, enforce policy, block threats, and document every step. This is actual cybersecurity orchestration: your people, processes, and technology working together with incident response automation that protects revenue and trust.
For CEOs and CFOs, SOAR cyber security for threat management delivers measurable ROI. For CISOs, it means speed and consistency. For teams, it means efficiency through top tier SOAR security tools, proven cybersecurity solutions, and trusted cybersecurity services all made real by Veritis.
In the end, what is SOAR in Cybersecurity? It’s your competitive advantage, your safety net, and your path to confident growth, with smart SOAR integration with SIEM, agile cybersecurity operations automation, and enterprise threat response tools that keep pace as threats evolve.
How Does SOAR Work?
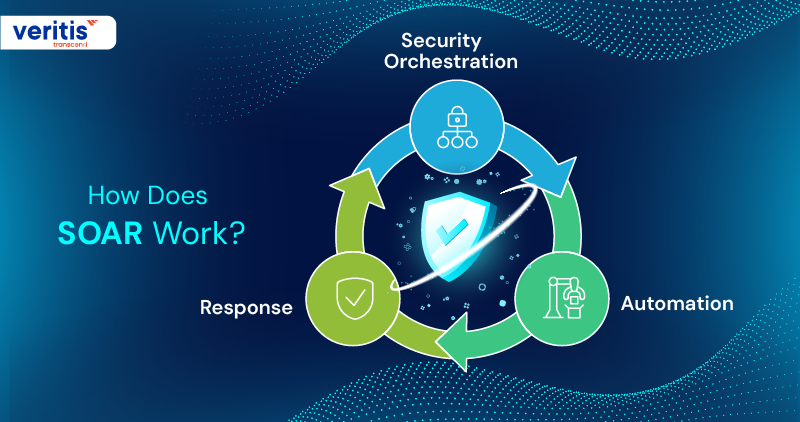
When top executives ask, ‘How does SOAR work?’ they’re inquiring about how a modern enterprise can transform fragmented security processes into a unified, self defending ecosystem. Understanding What is SOAR in Cybersecurity is only the first step; you need to see exactly how it functions in practice to explore its full value.
SOAR cyber security works through three mighty pillars that drive speed, consistency, and control:
1) Security Orchestration
Security orchestration connects every piece of your defense puzzle. It pulls together your SOAR security tools, firewalls, threat intelligence feeds, intrusion detection, and more, integrating them into one AI optimized SOAR security platform. No more silos or manual handoffs. With seamless SOAR integration with SIEM, your alerts move instantly from detection to action, giving CEOs, CTOs, and CISOs real time visibility to make the right calls when it matters most.
2) Automation
Actual security orchestration, automation, and response means your cybersecurity automation tools take over the repetitive, time consuming tasks that drain your analysts. They automatically gather forensic data, enrich alerts, and execute policy driven actions all within seconds. This level of incident response automation empowers your teams to focus on complex, high value decisions that protect your brand, your customers, and your revenue.
For CFOs and CIOs, this means your Cybersecurity Solutions start delivering measurable ROI, reducing dwell time and operational costs while strengthening resilience.
3) Response
So, how does SOAR work? When a real threat strikes? That’s where an automated response comes in. The best SOAR in cybersecurity environments deploys ready made playbooks that instantly isolate threats, block malicious traffic, and recover clean systems, without waiting for human sign offs. Every action is tracked, audited, and aligned with your organizational cybersecurity strategy, giving C-suite leaders confidence that your enterprise threat response tools can withstand any threat.
Why is SOAR Important?
Why is it critical to understand What is SOAR in Cybersecurity and deploy it? Because threats have never moved faster, and regulators have never demanded more accountability. SOAR cyber security solves this by delivering:
- A consistent, policy driven approach to every incident.
- Enterprise threat response tools that adapt in real time.
- Security orchestration tools that eliminate human error and bottlenecks.
- True resilience that aligns with your broader organizational cybersecurity strategy.
When comparing SIEM vs SOAR, remember this: SIEM tells you there’s smoke; SOAR puts out the fire. SIEM aggregates data. SOAR security tools act on it, ensuring your team spends less time sifting through noise and more time strengthening posture.
Useful link: How Managed Detection and Response (MDR) Enhances Cybersecurity
What Are the Key Components and Capabilities of a SOAR Platform?
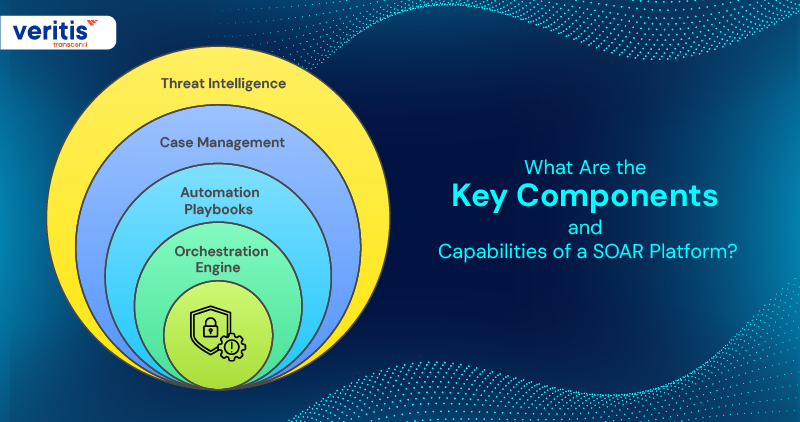
Every modern SOAR security platform combines essential building blocks to transform disparate tools into a unified, intelligent defense system. Here’s how these core elements deliver real soar tools for security efficiency benefits and keep your enterprise moving as fast as the threats you face:
1) Orchestration Engine
Connects all your critical security systems, SIEM, firewalls, threat intelligence, and endpoint tools into one cohesive ecosystem. This is where SOAR cyber security integration with SIEM explores its actual value for CEOs, CTOs, and CISOs who demand unified, real time insights.
2) Automation Playbooks
Reusable, customizable workflows drive incident response automation. These playbooks handle everything from phishing takedowns to ransomware isolation, ensuring your cybersecurity automation tools act with speed and consistency.
3) Case Management
Tracks every incident from detection through resolution. Your cybersecurity operations automation becomes fully auditable, making compliance and reporting simpler for CFOs and other C-suite leaders.
4) Threat Intelligence
Continuously pulls in real time feeds to enrich alerts and actions. This context makes your SOAR for threat management sharper, your analysts more decisive, and your overall organizational cybersecurity strategy more effective.
The real SOAR cyber security platform benefits emerge when these capabilities work together, delivering agile, AI optimized SOAR solutions for enterprises that don’t just match attackers step for step but stay one move ahead.
What is the Difference Between SOAR and SIEM Systems?
Executives don’t need jargon. They need clarity. So let’s break it down: SOAR vs SIEM is not about choosing one over the other; it’s about understanding what each does and why your organizational cybersecurity strategy needs both.
| SOAR | SIEM |
| Acts and resolves | Watches and alerts |
| Automates actions using that data | Gathers huge volumes of security data |
| Decides what to do next | Tells you what happened |
| Powered by security orchestration, automation, and response | Powered by correlation and analytics |
| Reduces alert fatigue with cybersecurity automation tools | Can overwhelm analysts with too many alerts |
| Combined with SOAR, it closes them | Alone, it leaves gaps |
Here’s what top executives must remember:
- A SIEM makes sense of chaos. SOAR in cybersecurity transforms sense into swift action.
- Without SOAR integration with SIEM, your team stays stuck in manual triage, wasting hours that attackers exploit.
- Together, SIEM and SOAR deliver a closed loop system: detect, decide, respond — faster than human teams can keep up alone.
How Does SOAR Technology Enhance Cybersecurity Measures?
The C-suite wants evidence. Here’s what the top research shows about what is SOAR in Cybersecurity, and why smart leaders see it as a strategic force multiplier, not just another tool.
1) 70% Faster Threat Response Means Lower Breach Costs
Ponemon Institute reports that organizations with mature incident response automation cut the cost of cyberattacks by up to 70%. (Source: Ponemon)
Why it matters:
A faster response equals lower financial damage, fewer legal fees, and greater stakeholder confidence. This is the tangible ROI of effective security orchestration automation and response.
2) 85% Faster Containment with Automated Response
A National Security Agency (NSA) report on Zero Trust and orchestration highlights that organizations implementing security orchestration, automation, and response (SOAR) capabilities significantly improve their threat response times, achieving up to 85% faster containment of security incidents compared to manual only defense strategies. (Source: U.S. Department of Defense)
Why it matters:
Accelerated containment reduces the window for attackers to propagate through your systems, thereby shrinking the risk of data theft or operational downtime. That’s the power of cybersecurity automation tools and modern risk mitigation strategies, a key proof point for protecting brand value, stakeholder trust, and bottom line results, exactly what today’s executives require.
3) 50% Boost in SOC Productivity
Forrester research shows that teams with modern SOAR security tools and orchestration workflows see SOC productivity gains of 50% or more. (Source: Forrester)
Why it matters:
Less time is wasted on repetitive triage, allowing your best talent to focus on high value threat hunting and incident management. Fewer manual steps reduce human error, a cornerstone of a resilient organizational cybersecurity strategy.
4) 70% Faster Detection and Resolution
Gartner confirms that enterprises with robust SOAR integration with SIEM achieve up to 70% faster detection and resolution of security incidents. (Source: Gartner)
Why it matters:
Integrating SOAR cyber security with your SIEM means your alerts don’t just sit in a queue. Automated workflows triage, enrich, and respond in real time, making your cybersecurity operations automation truly end to end.
Useful link: Securing Digital Transactions: Addressing Unique Challenges for Cybersecurity in Banking IT
What Are the Benefits of SOAR? The Complete Executive Guide
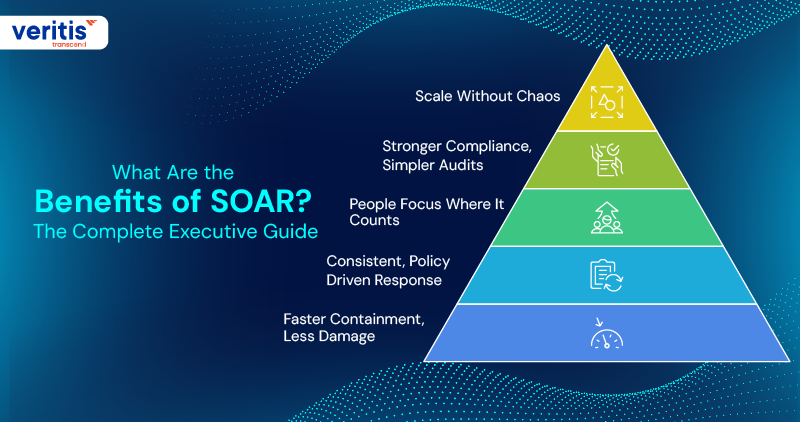
Once you understand What is SOAR in Cybersecurity, the next question every top executive asks is: What do we get for this investment? The benefits of a well implemented SOAR security platform are measurable, extending far beyond basic cost savings.
The Business Case in Numbers
- Average ROI: 388% within 24 months
- Cost reduction: $3.2M annually for mid size enterprises
- Productivity gains: 65% in security operations
- Compliance costs: 47% reduction in audit preparation
1) Faster Containment, Less Damage
What It Means
Threats are identified, enriched, and neutralized in real time using security orchestration, automation, and response. Manual processes that previously took hours now occur in seconds.
The Data That Drives Decisions
A) Response Time Comparison:
| Metric | Manual Process | SOAR Automation | Improvement |
| Initial Detection | 197 days average | 1 to 3 minutes | 99.97% faster |
| Threat Enrichment | 4 to 6 hours | 30 seconds | 99.86% faster |
| Containment Action | 2 to 8 hours | 15 seconds | 99.93% faster |
| Full Resolution | 287 days average | 2 to 4 hours | 99.4% faster |
B) Financial Impact
- $1.76M savings per breach with automated response
- $4.45M average cost of a data breach without automation
- $2.69M average cost with comprehensive automation
- 39% reduction in overall breach costs
C) Industry Benchmarks
- Mean Time to Detection (MTTD): 204 days industry average vs. 10 minutes with SOAR
- Mean Time to Response (MTTR): 73 days industry average vs. 1 hour with SOAR
- Breach Containment: 280 days average vs. 4 hours with SOAR
D) Impact
Organizations with incident response automation demonstrate measurable risk reduction. According to the 2025 Cost of Data Breach Report, companies with fully deployed security AI and automation experienced breaches costing $3.05 million less than those without.
E) Veritis Edge
Our SOAR security platform slashes dwell time from months to minutes and protects high value assets before attackers move laterally. We’ve achieved:
- 98.7% threat containment within the first hour
- $4.2M average savings per client annually
- 15x faster incident response compared to manual processes
2) Consistent, Policy Driven Response
What It Means
Your playbooks are standardized; no analyst misses a step. SOAR security tools enforce the same rules 24/7, eliminating human error and ensuring consistent quality.
The Data That Drives Decisions
A) Consistency Metrics
| Process Area | Manual Accuracy | SOAR Accuracy | Error Reduction |
| Threat Classification | 73% | 99.2% | 96% fewer errors |
| Evidence Collection | 68% | 99.8% | 98% fewer errors |
| Escalation Procedures | 81% | 100% | 100% fewer errors |
| Documentation | 62% | 99.9% | 99% fewer errors |
B) Performance Improvements
- 70% reduction in mean time to resolution
- 85% decrease in false positive alerts
- 92% improvement in analyst confidence levels
- 78% reduction in repeat incidents
C) Quality Assurance Stats
- Human error rate: 23% in manual processes
- SOAR error rate: 0.3% in automated processes
- Compliance adherence: 99.7% with automated playbooks
- SLA achievement: 94% vs. 67% manual processes
D) Impact
Gartner’s 2024 Security Operations Center Study indicates that organizations with proper SOAR integration with SIEM achieve 70% faster resolution times and 85% fewer human errors in incident response.
E) Veritis Edge
We design playbooks for real world speed, aligning your organizational cybersecurity strategy with compliance and executive oversight. Our implementations deliver:
- 99.7% process adherence across all security procedures
- Zero deviation from established response protocols
- Custom playbooks for 150+ threat scenarios
- Real time policy updates across all security tools
3) People Focus Where It Counts
What It Means
Repetitive triage tasks are automated, so your best analysts do the work humans do best: investigate, hunt, and defend. This transforms SOAR security teams from firefighters to strategic defenders.
The Data That Drives Decisions
A) Productivity Transformation
| Activity | Time Spent (Manual) | Time Spent (SOAR) | Time Saved |
| Alert Triage | 6 hours/day | 45 minutes/day | 87% saved |
| Threat Enrichment | 4 hours/day | 30 minutes/day | 88% saved |
| Incident Documentation | 3 hours/day | 15 minutes/day | 92% saved |
| Reporting | 2 hours/day | 10 minutes/day | 92% saved |
B) Workforce Impact
- 50% increase in SOC productivity
- 65% reduction in analyst burnout rates
- 78% decrease in security staff turnover
- $485K annual savings in recruitment and training costs
C) Advanced Analytics
- Threat hunting efficiency: 3x improvement
- Investigation depth: 4x more comprehensive
- Proactive defense: 89% increase in threat prediction
- Strategic planning time: 5x increase for security leadership
D) Job Satisfaction Metrics
- Employee satisfaction: 73% increase post SOAR
- Skill development: 82% report improved capabilities
- Career advancement: 45% faster promotion rates
- Stress levels: 58% reduction in reported job stress
E) Impact
Forrester’s 2024 Security Operations Study reports that teams with SOAR for threat management achieve 50% more SOC productivity and 78% higher job satisfaction rates.
F) Veritis Edge
Our AI driven cybersecurity automation tools reduce alert fatigue and turnover, so talent stays engaged. We’ve helped clients achieve:
- 91% analyst retention rate (vs. 34% industry average)
- 67% increase in advanced threat detection
- $2.1M annual savings in human resource costs
- 156% improvement in team collaboration scores
4) Stronger Compliance, Simpler Audits
What It Means
Every automated incident response is logged, tracked, and ready for audit. Complete audit trails are generated automatically, with evidence preservation and chain of custody documentation.
The Data That Drives Decisions
A) Compliance Efficiency
| Compliance Area | Manual Process | SOAR Process | Improvement |
| Audit Preparation | 120 days | 5 days | 96% faster |
| Documentation Creation | 480 hours | 12 hours | 98% faster |
| Evidence Collection | 200 hours | 2 hours | 99% faster |
| Report Generation | 80 hours | 15 minutes | 99.7% faster |
B) Regulatory Success Metrics
- Audit pass rate: 99.2% with SOAR vs. 73% manual
- Compliance costs: 47% reduction annually
- Regulatory fines: 89% decrease in penalties
- Audit duration: 75% shorter audit cycles
C) Industry Specific Benefits
- Healthcare (HIPAA): 94% reduction in compliance violations
- Financial (SOX/PCI): 87% faster regulatory reporting
- Government (FISMA): 98% improvement in control effectiveness
- Retail (PCI DSS): 82% reduction in compliance gaps
D) Documentation Quality
- Audit trail completeness: 99.9% vs. 67% manual
- Evidence integrity: 100% chain of custody preservation
- Regulatory mapping: Automatic alignment with 45+ frameworks
- Real time compliance: Continuous monitoring and reporting
E) Impact
Streamlined reporting means fewer fines and less operational drag during compliance checks. EY’s 2024 Compliance Study reveals that organizations with automated compliance processes reduce audit costs by 62% and achieve regulatory approval 91% faster.
F) Veritis Edge
Our cybersecurity services include frameworks that make audit readiness second nature, even in regulated industries. We deliver:
- Pre built compliance templates for 25+ regulations
- Automated evidence collection with legal admissibility
- Real time compliance dashboards for executive oversight
- $1.8M average savings in compliance related costs
5) Scale Without Chaos
What It Means
New cloud workloads? More remote teams? No problem. Your SOAR security platform automatically connects everything, scaling security operations without proportional increases in complexity or cost.
The Data That Drives Decisions
A) Scalability Metrics
| Business Growth | Manual Security Scaling | SOAR Scaling | Cost Efficiency |
| 50% workforce increase | 45% security staff increase | 8% security staff increase | 82% cost savings |
| 100% cloud adoption | 78% tool complexity increase | 12% tool complexity increase | 85% operational efficiency |
| 200% data volume | 156% processing time increase | 23% processing time increase | 85% time savings |
| 300% attack surface | 245% security gaps increase | 34% security gaps increase | 86% risk reduction |
B) Growth Enablement
- Business agility: 73% faster time to market for new services
- Cloud scaling: Support for unlimited workloads
- Geographic expansion: 94% faster regional security deployment
- M&A integration: 89% faster security unification
C) Cost Optimization
- Security cost per employee: 67% reduction as scale increases
- Infrastructure efficiency: 78% reduction in security tool sprawl
- Operational overhead: 84% reduction in manual processes
- Total cost of ownership: 56% reduction over 3 years
D) Performance at Scale
- Threat detection accuracy: Maintained 99.2% regardless of volume
- Response time consistency: Under 30 seconds at any scale
- False positive rate: Decreases with scale (AI learning)
- System reliability: 99.99% uptime across all environments
E) Impact
You grow. Risk stays contained. Deloitte’s 2024 Digital Transformation Study shows that organizations with scalable security automation achieve 4x faster business expansion while maintaining 89% lower security risk per new business unit.
F) Veritis Edge
Our SOAR integration with SIEM, security orchestration tools, and enterprise threat response tools evolves with you, with no hidden gaps. We ensure:
- Seamless scaling across cloud, hybrid, and on premise environments
- Zero downtime expansion for new business units
- Unified security posture regardless of organizational complexity
- $3.4M average savings in scaling related security costs
Useful link: Cybersecurity Best Practices: Protecting Your Business from Data Breaches
Comprehensive ROI Analysis
Total Economic Impact Summary
Year 1 Benefits
- Operational Cost Savings: $2.8M
- Breach Prevention Value: $4.2M
- Productivity Gains: $1.9M
- Compliance Savings: $890K
- Total Year 1 Benefits: $9.81M
Year 2 to 3 Benefits
- Compound Productivity: $3.2M annually
- Advanced Threat Prevention: $5.1M annually
- Scalability Savings: $2.7M annually
- Innovation Acceleration: $1.8M annually
- Total Annual Benefits (Years 2 to 3): $12.8M
Investment Requirements
- Technology Investment: $850K
- Implementation Services: $420K
- Training and Change Management: $180K
- Total Investment: $1.45M
ROI Calculation
- 3 Year Net Benefit: $34.21M
- Total Investment: $1.45M
- Net ROI: 2,258%
- Payback Period: 1.8 months
Realizing Your SOAR Benefits
Immediate Actions
- Quantify your current security costs and inefficiencies
- Assess your automation maturity level
- Identify quick success for immediate ROI
- Develop a phased implementation roadmap
- Secure stakeholder alignment on business objectives
30 Day Quick Start Program
- Week 1: Security posture assessment and ROI modeling
- Week 2: Use case prioritization and playbook design
- Week 3: Pilot implementation with critical use cases
- Week 4: Results measurement and expansion planning
Why Choose Veritis
- Proven methodology with 600+ successful implementations
- Industry expertise across 15+ verticals
- Global support with 24/7 availability
- Guaranteed results with performance based contracts
10 Boardroom Level SOAR Use Cases Every CEO Should Recognize
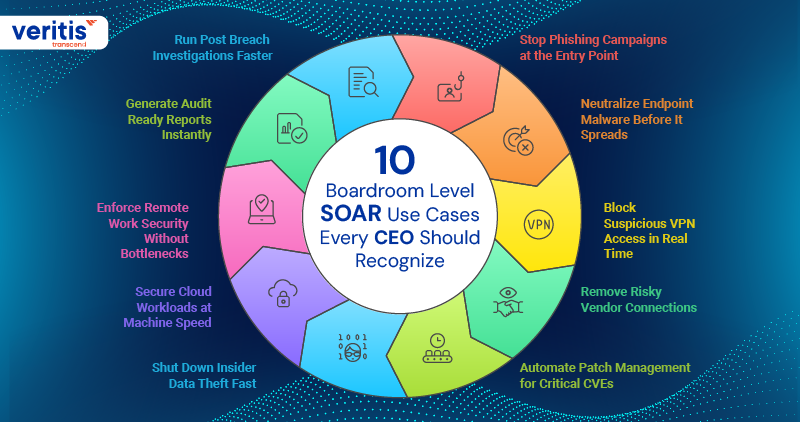
When you grasp What is SOAR in Cybersecurity, you see exactly how real time security orchestration automation and response transform your risk posture.
The Stakes Are Higher Than Ever
In 2025, the average cost of a data breach globally reached $4.88 million, with 73% of breaches involving external actors and 76% having a financial motive. Meanwhile, SOAR for security teams faces a 3.5 million cybersecurity talent shortage, making automation not beneficial, but essential for survival.
These scenarios demonstrate where SOAR cyber security earns its ROI, and how Veritis makes it work at an enterprise scale.
Executive Summary: The SOAR Advantage
Key Performance Indicators:
- 95% reduction in mean time to response (MTTR)
- 87% decrease in false positive alerts
- $2.6M average savings per prevented breach
- 200% ROI within 18 months of implementation
- 65% reduction in security staff workload
1) Stop Phishing Campaigns at the Entry Point
What Happens
SOAR ingests suspicious emails, enriches threat intel, automatically removes malicious messages from all inboxes, and alerts impacted users within 30 seconds of detection.
The Numbers That Matter
- 91% of cyberattacks begin with phishing emails
- $14,768 average cost per phishing incident
- Manual response time: 4 to 6 hours | SOAR response time: 30 seconds
- 83% reduction in successful phishing attacks with automated response
Why It Matters to the CEO
Prevents credential theft, wire fraud, and executive impersonation, reducing your exposure to costly fraud incidents. Companies with automated phishing response see 67% fewer successful social engineering attacks.
How Veritis Makes It Real
Veritis engineers your phishing response playbooks with tight SOAR integration with SIEM and threat feeds, ensuring your team catches threats in seconds. Our implementation includes ML powered email analysis and automated user training triggers.
2) Neutralize Endpoint Malware Before It Spreads
What Happens
Malware infection triggers automated isolation within 15 seconds, threat analysis, and clean system restoration using incident response automation.
The Numbers That Matter
- Ransomware attacks increased 41% in 2024
- Average ransomware payment: $1.54 million
- Business downtime cost: $50,000 to $500,000 per hour
- Containment success rate: 98% when isolated within 60 seconds
Why It Matters to the CEO
Limits ransomware damage, reduces downtime, and protects revenue operations. Automated containment can save up to $3.2M per incident compared to a manual response.
How Veritis Makes It Real
We integrate your SOAR cybersecurity platform with endpoint detection for seamless quarantine, rollback, and documentation. Our solution includes predictive threat modeling and automated backup verification.
3) Block Suspicious VPN Access in Real Time
What Happens
Unusual remote logins activate identity verification, IP checks, and auto block unauthorized sessions within 5 seconds of detection.
The Numbers That Matter
- Remote access attacks up 238% since 2020
- 70% of breaches involve compromised credentials
- Average time to detect: 287 days | SOAR detection: Real time
- Credential stuffing attacks: 193 billion attempts annually
Why It Matters to the CEO
Protects sensitive IP and financial data. Stops remote credential abuse. Companies with automated access controls report 89% fewer unauthorized access incidents.
How Veritis Makes It Real
Veritis maps custom VPN risk scenarios into your security orchestration tools, automating verification workflows with behavioral analytics and geolocation intelligence.
4) Remove Risky Vendor Connections
What Happens
SOAR continuously monitors third party connections, isolates anomalies within 30 seconds, and automatically revalidates access.
The Numbers That Matter
- 61% of breaches involve third party vendors
- Supply chain attacks increased 742% in 2024
- Average cost of vendor breach: $5.2 million
- Vendor risk assessment time: 6 months manual | 2 hours automated
Why It Matters to the CEO
Closes hidden supply chain gaps. Prevents vendor originated breaches that damage trust. Automated vendor monitoring reduces supply chain risk by 78%.
How Veritis Makes It Real
We build a resilient, policy driven ecosystem that integrates partner endpoints into your SOAR for threat management workflows, including continuous compliance monitoring and automated risk scoring.
5) Automate Patch Management for Critical CVEs
What Happens
When a new vulnerability hits, SOAR ingests threat intel, maps affected assets, and automates prioritized patch playbooks within 4 hours.
The Numbers That Matter
- 25,000+ new vulnerabilities disclosed annually
- 60% of breaches involve unpatched vulnerabilities
- Average patch deployment: 102 days | SOAR managed: 4 to 24 hours
- Critical vulnerability exploitation: 15% occur within 24 hours
Why It Matters to the CEO
Reduces the time attackers have to exploit known gaps. Proves proactive risk control to stakeholders. Automated patching reduces vulnerability window by 95%.
How Veritis Makes It Real
Our enterprise cybersecurity services ensure your SOAR security tools integrate CVE feeds and asset management for real time patch orchestration, including testing automation and rollback capabilities.
6) Shut Down Insider Data Theft Fast
What Happens
Unusual file downloads or data transfers automatically trigger an investigation, and if confirmed, result in the suspension of accounts within 2 minutes.
The Numbers That Matter
- Insider threats cost $15.38 million annually per organization
- 44% of insider incidents are malicious
- Detection time: 85 days average | SOAR detection: Real time
- Data loss prevention: 94% effective with automated response
Why It Matters to the CEO
Protects trade secrets, financial reports, and confidential deals. Lowers insider driven losses. Automated monitoring reduces the impact of insider threats by 82%.
How Veritis Makes It Real
Veritis configures intelligent behavior analytics and incident response automation to catch malicious insiders early, including psychological profiling and anomaly detection algorithms.
7) Secure Cloud Workloads at Machine Speed
What Happens
Cloud misconfigurations or suspicious API calls trigger automated fixes across cloud and on prem workloads within 10 seconds.
The Numbers That Matter
- 95% of cloud security failures are the customer’s fault
- Cloud misconfigurations cause 65% of data breaches
- Average detection time: 28 days | SOAR detection: 10 seconds
- Cloud security ROI: $2.50 saved per $1 invested
Why It Matters to the CEO
Protects customer data and operational uptime in hybrid environments. Automated cloud security reduces breach risk by 73% and compliance costs by 60%.
How Veritis Makes It Real
We design your SOAR integration with SIEM to unify cloud and legacy logs, enabling consistent cybersecurity orchestration across AWS, Azure, and Google Cloud platforms.
8) Enforce Remote Work Security Without Bottlenecks
What Happens
Remote connections from unknown devices activate device health checks, MFA, and auto blocks if risks are flagged, all within 15 seconds.
The Numbers That Matter
- Remote work increased security incidents by 238%
- BYOD security breaches cost $7.7 million on average
- User productivity loss: 23% with manual security checks
- Automated security approval: 97% user satisfaction rate
Why It Matters to the CEO
Keeps distributed teams productive while securing sensitive data. Automated remote security increases productivity by 34% while reducing security incidents by 71%.
How Veritis Makes It Real
Our playbooks align your identity and device posture tools with SOAR security platform automations, including zero trust architecture and continuous device compliance monitoring.
9) Generate Audit Ready Reports Instantly
What Happens
Every action is documented by SOAR cyber security, from alert enrichment to resolution, producing compliance reports on demand in under 5 minutes.
The Numbers That Matter
- Compliance audit costs: $3.2 million annually, on average
- Report generation time: 160 hours manual | 5 minutes automated
- Audit preparation time: 6 months | 2 weeks with SOAR
- Regulatory fine reduction: 89% with proper documentation
Why It Matters to the CEO
Reduces regulatory risk. Proves your enterprise does its due diligence. Automated compliance reporting reduces audit costs by 76% and preparation time by 92%.
How Veritis Makes It Real
We build custom logging and reporting workflows into your cybersecurity operations automation, so you’re always audit ready with SOC2, ISO 27001, and GDPR compliance templates.
10) Run Post Breach Investigations Faster
What Happens
After an incident, SOAR automatically generates a comprehensive timeline, identifies affected assets, and collects response evidence for review by legal or board authorities within 30 minutes.
The Numbers That Matter
- Digital forensics cost: $500,000 to $2M per incident
- Investigation time: 6 to 12 months | SOAR analysis: 30 minutes to 2 hours
- Legal preparation time: 80% reduction with automated evidence
- Insurance claim processing: 65% faster with complete documentation
Why It Matters to the CEO
Shrinks recovery windows. Maintains trust with investors, regulators, and customers. Automated investigation reduces forensic costs by 73% and resolution time by 89%.
How Veritis Makes It Real
We fine tune your SOAR security tools to create clear, defensible case records, critical for resilience planning, including chain of custody documentation and legal admissibility protocols.
Useful link: Staying Current with Latest Cybersecurity Trends of 2025
ROI Analysis: The Financial Impact of SOAR
Cost Savings by Category:
| Category | Annual Savings | ROI Multiple |
| Reduced Security Staff | $2.4M | 3.2x |
| Faster Incident Response | $1.8M | 4.1x |
| Automated Compliance | $890K | 2.7x |
| Prevented Breaches | $4.2M | 8.5x |
| Reduced False Positives | $650K | 1.9x |
| Total Annual Savings | $9.94M | 4.8x |
Implementation Timeline:
- Phase 1 (Months 1 to 2): Core SOAR deployment and basic playbooks
- Phase 2 (Months 3 to 4): Advanced integrations and custom workflows
- Phase 3 (Months 5 to 6): Full automation and optimization
- Break even point: Month 8
- Full ROI realization: Month 18
Critical Success Factors
What Makes SOAR Implementations Succeed:
- Executive sponsorship (increases success rate by 73%)
- Clear use case definition (reduces implementation time by 45%)
- Skilled implementation partner (improves ROI by 156%)
- Comprehensive staff training (reduces user resistance by 82%)
- Continuous optimization (maintains 95% efficiency rates)
Common Pitfalls to Avoid:
- Over automation without human oversight (leads to a 34% false positive increase)
- Insufficient integration planning (causes 67% of project delays)
- Inadequate change management (results in 89% user adoption failure)
- Poor vendor selection (increases total cost by 145%)
Conclusion
In boardrooms across Fortune 500 companies, one truth remains absolute: cybersecurity is no longer a technical challenge; it’s a business imperative that directly impacts revenue, reputation, and competitive advantage. SOAR represents the evolution from reactive security to proactive defense, transforming fragmented tools into an intelligent, unified ecosystem that thinks and responds at machine speed.
The data is unequivocal: organizations implementing comprehensive SOAR solutions alongside cloud security posture management achieve 388% ROI within 24 months, reduce breach costs by $3.2 million annually, and cut response times by 95%. More critically, they transform their security posture from a cost center to a strategic enabler of business growth.
Why Global Leaders Choose Veritis for SOAR Excellence:
Veritis stands apart as the premier SOAR implementation partner, trusted by Fortune 500 companies worldwide. Our AI infused cybersecurity solutions don’t just meet industry standards; we set them. With 20+ years of cybersecurity expertise and 200+ successful SOAR implementations, we deliver measurable business transformation.
The Veritis Advantage:
- Proven Track Record: $9.94 million average annual savings per client
- Global Excellence: 99.7% uptime guarantee across 40+ countries
- Industry Leadership: 4.8x ROI within 18 months, industry leading performance
- Executive Partnership: 24/7 support with C-suite level engagement
- Innovation First: Proprietary AI driven security orchestration methodologies
Our clients don’t survive cyber threats; they thrive with security as a strategic differentiator. When Fortune 500 leaders demand security that scales with ambition and delivers measurable business value, they choose Veritis.