In recent years, adversaries have become more sophisticated, rendering traditional security models obsolete. Organizations now require a security model that is more holistic, multilayered, and event-driven to defend against the new generation of attacks. This is where the ‘Zero Trust Security Model’ comes to the rescue.
At its simplest, Zero Trust model removes the assumption of trust from the security architecture by authenticating every action, user, and device. Based on “Never Trust, Always Verify” principle, the Zero Trust security model helps organizations achieve a more robust and resilient security posture.
While the Zero Trust strategy has quickly become the corporate agenda, the fact remains that the model is easier said than done. The myths and misconceptions surrounding the new security model are impeding adoption. Organizations must debunk the myths to implement Zero Trust swiftly.
Here’s an infographic on common Zero Trust myths to decipher misunderstanding from reality:
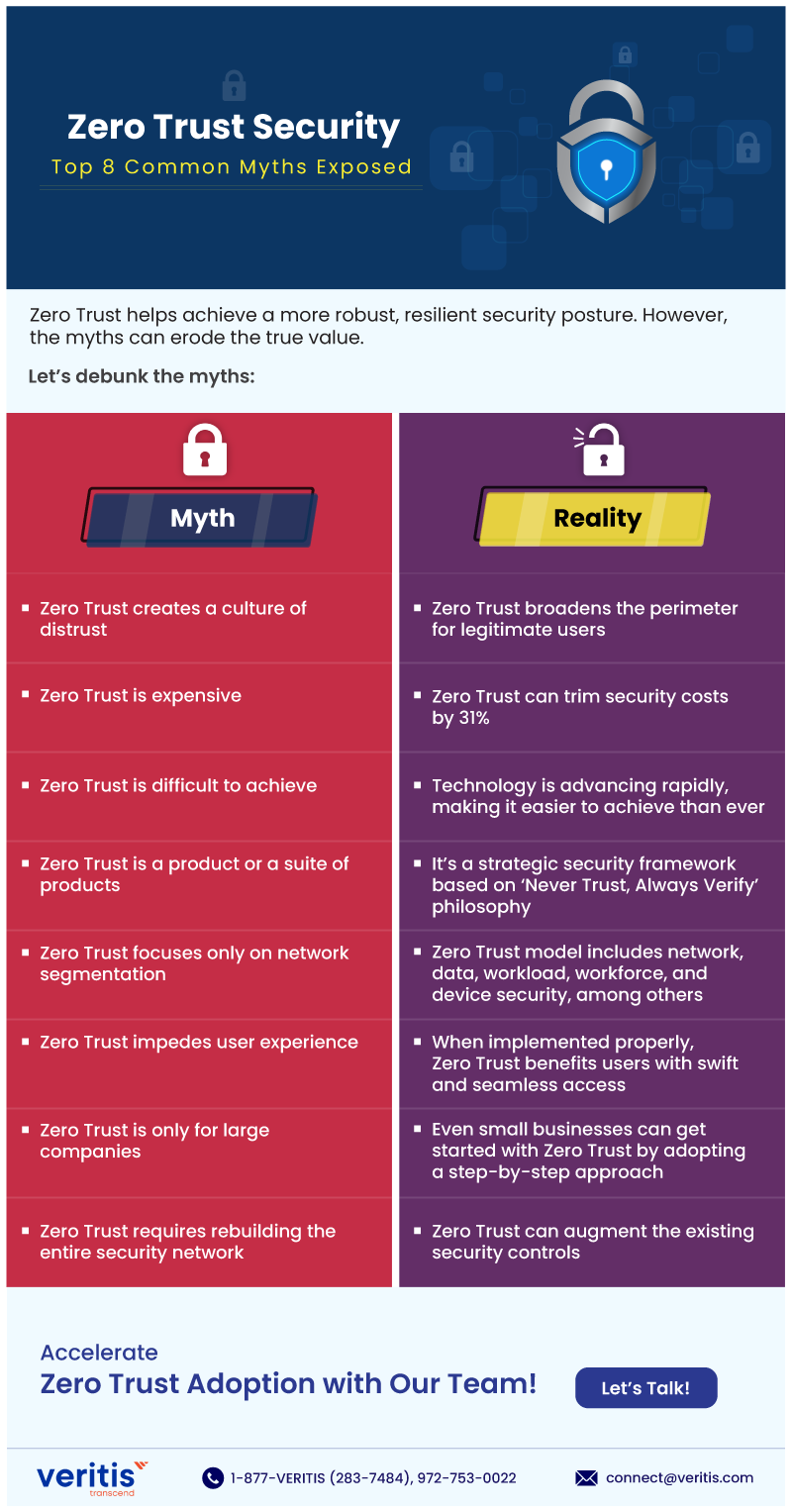
Zero Trust helps achieve a more robust, resilient security posture. However, the myths can erode the true value.
Let’s debunk the myths:
Myth | Reality |
| Zero Trust creates a culture of distrust | Zero Trust broadens the perimeter for legitimate users |
| Zero Trust is expensive | Zero Trust can trim security costs by 31% |
| Zero Trust is difficult to achieve | Technology is advancing rapidly, making it easier to achieve than ever |
| Zero Trust is a product or a suite of products | It’s a strategic security framework based on ‘Never Trust, Always Verity’ philosophy |
| Zero Trust focuses only on network segmentation | Zero Trust model includes network, data, workload, workforce, and device security, among others |
| Zero Trust impedes user experience | When implemented properly, Zero Trust benefits users with swift and seamless access |
| Zero Trust is only for large companies | Even small businesses can get started with Zero Trust by adopting a step-by-step approach |
| Zero Trust requires rebuilding the entire security network | Zero Trust can augment the existing security controls |
Accelerate Zero Trust Adoption with Veritis!
More Infographics:

