Amid the pandemic, enterprises across the world adopted remote working culture to enable business continuity. This has led to a significant spike in access points and digital user identities.
It is a tightrope walk for enterprises to facilitate near-ubiquitous access to users and protect sensitive information. Many are struggling to define and manage user identities and access permissions.
Organizations need a robust IAM system to enable effective access management, authentication, identity management and governance.
Here’s an infographic that sheds light on eight best practices to implement robust IAM strategy:
Email-us: connect@veritis.com; Call: 972-753-0022
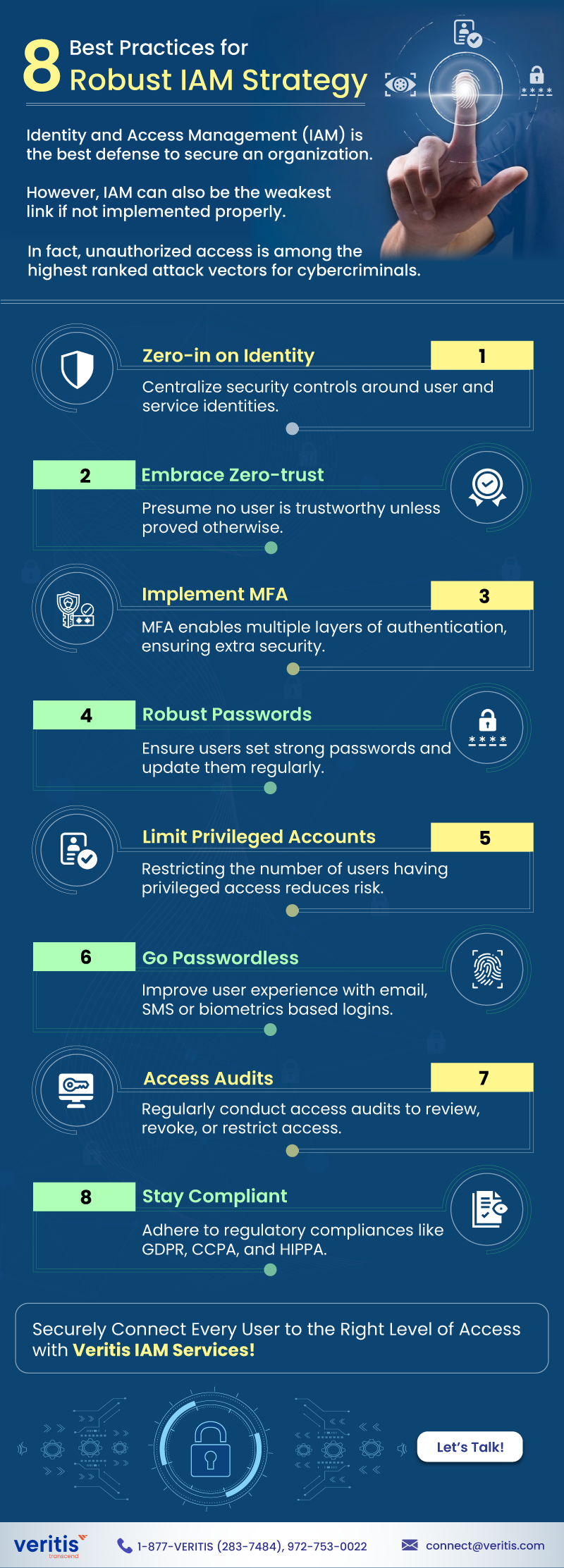
Identity and Access Management (IAM) is the best defense to secure an organization. However, IAM can also be the weakest link if not implemented properly.
In fact, unauthorized access is among the highest ranked attack vectors for cybercriminals.
8 Best Practices for Robust IAM Strategy
1) Zero-in on Identity
Centralize security controls around user and service identities
2) Embrace Zero-trust
Presume no user is trustworthy unless proved otherwise.
3) Implement MFA
MFA enables multiple layers of authentication, ensuring extra security
4) Robust Passwords
Ensure users set strong passwords and update them regularly
5) Limit Privileged Accounts
Restricting the no. of users having privileged access reduces risk
6) Go Passwordless
Improve user experience with email-, SMS-, or biometrics-based logins
7) Access Audits
Regularly conduct access audits to review, revoke, or restrict access
8) Stay Compliant
Adhere to regulatory compliances like GDPR, CCPA, and HIPPA
Securely Connect Every User to the Right Level of Access with Veritis IAM Services!
Let’s Talk!
More Articles:
- Robust Identity Management With ‘8-Point IAM Audit Checklist’ and ‘IAM Strategy’
- 5 Key IAM Predictions to Watch in 2021 and Beyond!
- IAM Best Practices for Optimal Cloud Security
- Healthcare Identity and Access Management (IAM): Five Steps to Transformation
- Top Tools and Security Protocols That Make IAM Successful!

