
Table of contents
- Understanding the Risks: Why Do Data Breaches Occur?
- 12 Essential Cybersecurity Best Practices for Business Leaders
- Recognize Sensitive Data and Categorize It
- Establish a Comprehensive Data Governance Policy
- Implement Zero Trust Architecture
- Deploy AI Powered Security Solutions
- Prepare for Quantum Computing Threats
- Control and Monitor Access to Sensitive Data
- Secure Physical Infrastructure and Devices
- Implement Comprehensive Endpoint Security
- Document Your Security Policies and Procedures
- Adopt a Risk Based Security Approach
- Invest in Continuous Security Awareness Training
- Implement Multifactor Authentication and Passwordless Solutions
- The Business Impact of Cybersecurity
- Case Study: Cybersecurity Transformation for a Fitness and Wellness Platform
- Conclusion
In the digital era, cybersecurity is a critical concern for businesses of all sizes. A single data breach can lead to financial losses, reputational damage, and legal consequences. As cyber threats continue to evolve, it is crucial for organizations, especially those led by C-suite executives, to adopt a proactive approach to cybersecurity best practices for business that strengthen long term resilience.
Every employee plays a role in protecting the organization from cyber threats. However, executive leadership must spearhead cybersecurity strategies and best practices to ensure company wide compliance and improved readiness. This guide outlines key best practices for cybersecurity market analysis to protect your business from data breaches and strengthen your overall security posture. Managed security services experts help organizations reduce exposure to cyber risks through advanced cybersecurity services and integrated cybersecurity solutions
Talk To Our Cybersecurity Expert
Understanding the Risks: Why Do Data Breaches Occur?
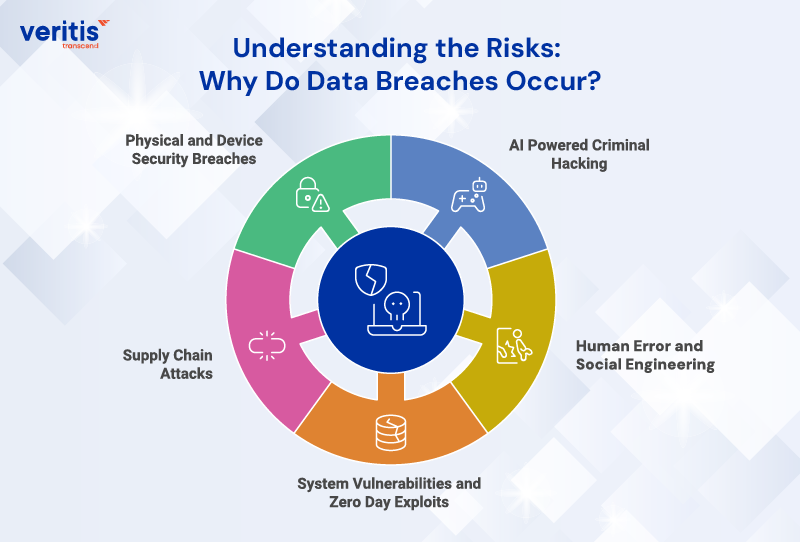
A data breach occurs when protected or confidential data is accessed, exposed, lost, or stolen without authorization. As cybercriminals become more sophisticated, understanding these risks is fundamental to implementing effective cybersecurity best practices and Risk Mitigation Strategies.
Data breaches can occur through various means, but the primary causes typically include:
1) AI Powered Criminal Hacking
In 2026, cybercriminals are leveraging agentic AI and autonomous systems to exploit vulnerabilities at unprecedented speed and scale. Attackers use AI generated deepfakes, synthetic media, and adaptive malware to bypass traditional security measures. Protecting your business requires robust security frameworks, continuous monitoring, and adherence to cybersecurity best practices for business that specifically address AI driven threats.
2) Human Error and Social Engineering
Employees often unintentionally expose sensitive data by clicking on AI generated phishing emails, misconfiguring security settings, or mishandling company devices. With AI making phishing attacks 1,265% more sophisticated, regular cybersecurity training programs are essential to mitigate these risks. Implementing best practices for cybersecurity includes comprehensive employee education on recognizing AI enhanced social engineering attacks.
3) System Vulnerabilities and Zero Day Exploits
Software vulnerabilities, cloud misconfigurations, and errors in data processing procedures can expose sensitive information and lead to catastrophic breaches. Adopting cybersecurity best practices for business ensures that systems are regularly updated, patched, and monitored using AI powered detection tools to prevent such vulnerabilities.
4) Supply Chain Attacks
In 2026, attackers increasingly target third party providers and supply chains, exploiting vulnerabilities in build systems, container registries, and trusted suppliers to gain access to multiple downstream organizations. To counter these threats, comprehensive cybersecurity strategies and Container Security Best Practices must be adopted alongside rigorous third party risk management to ensure end to end protection across the software supply chain.
5) Physical and Device Security Breaches
Data breaches can occur due to the physical theft of data carrying devices such as laptops, hard drives, or USB drives. Implementing strict best cybersecurity practices for device security, including encryption and Zero Trust access controls, helps reduce such risks.
Useful link: Security Breaches Rising Exponentially; Weak Authentications Exploited
Where Does Your Data End Up, and Who Has Access to It?
To effectively protect something, you must first understand its existence and sensitivity. That’s why it’s essential to know what data you have, where it resides, and how it moves across your organization. Staying aligned with evolving Cybersecurity Trends and following cybersecurity best practices helps build this clarity and ensures the right safeguards are applied.
You need a complete view of how your data is used, who has access to it, and where it is being shared. Collect information from all sources, including devices, applications, and online services, and categorize it based on sensitivity and access levels. This approach aligns with cybersecurity best practices for business and helps prevent unnecessary exposure that can lead to breaches.
Once this visibility is established, you can design and implement the right cybersecurity practices, policies, and control frameworks to protect your data. This strengthens your ability to secure sensitive information, reduce vulnerabilities, and lower the overall risk of cybersecurity breaches.
12 Essential Cybersecurity Best Practices for Business Leaders in 2026
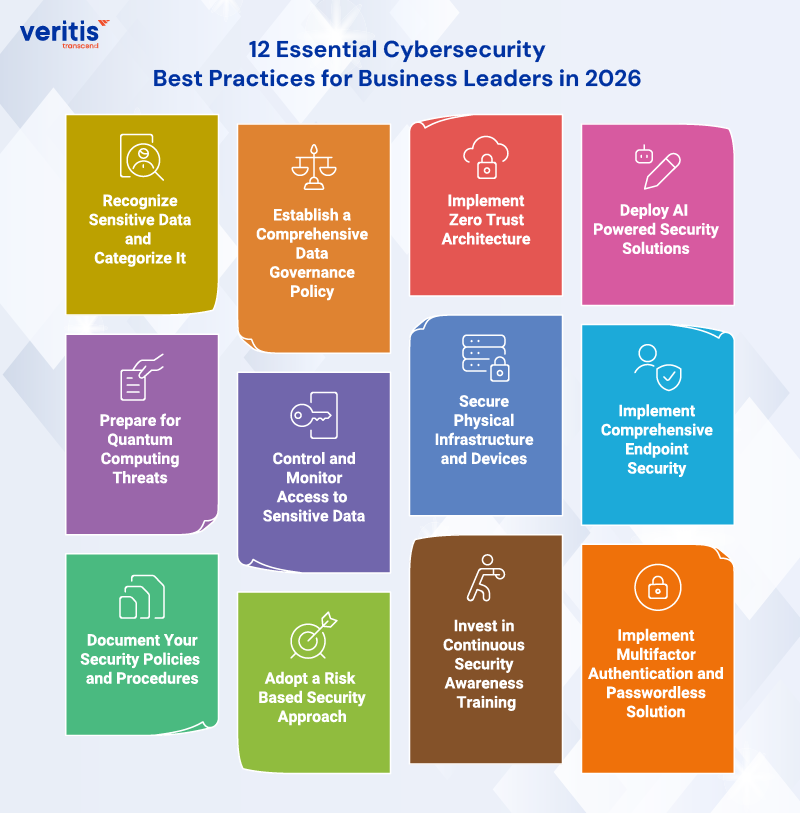
1) Recognize Sensitive Data and Categorize It
To protect your data effectively, you must clearly understand the types of information your organization possesses. Deploy AI powered data discovery tools that can automatically scan your data storage areas across cloud, on premises, and hybrid environments, generating comprehensive reports on data classification.
Organize data into different categories based on its value, sensitivity, and regulatory requirements. Keep the categorization dynamically updated as data changes or is shared with AI systems and third parties. Establish automated policies that prevent unauthorized users from altering data classifications. Only authorized personnel should be able to upgrade or downgrade data classification levels. These steps are integral to implementing best cybersecurity practices in 2026 and strengthening cybersecurity best practices for business.
2) Establish a Comprehensive Data Governance Policy
Simply classifying data is insufficient. CEOs must champion the creation of enterprise wide policies that outline how data should be accessed, who can access it based on its classification, and guidelines for proper use across all systems, including AI platforms. This policy should implement dynamic access controls that automatically deactivate access when it is no longer needed and prevent data exfiltration through unauthorized channels.
Enforce strict, transparent consequences for policy violations to strengthen your cybersecurity best practices for business and create a culture of accountability aligned with best practices for cybersecurity.
3) Implement Zero Trust Architecture
Zero Trust Architecture signifies a fundamental shift in how organizations approach security in 2026. Unlike traditional perimeter based security, Zero Trust works on the principle of “never trust, always verify.” This is one of the most critical cybersecurity strategies and best practices in the modern threat landscape.
Zero Trust implementation includes:
A) Continuous Verification: Every user, device, and application must be authenticated and authorized for each access request, regardless of location or network.
B) Micro Segmentation: Divide your network into small, isolated zones to stop lateral movement by attackers.
C) Least Privilege Access: Grant users only the minimum permissions required to perform their specific tasks.
D) Device Health Validation: Continuously assess the security posture of every device attempting to access your resources.
E) Dynamic Policy Enforcement: Adjust access based on contextual factors like user risk scores, geolocation, device health, and behavioral analytics.
Organizations implementing comprehensive Zero Trust frameworks have demonstrated the ability to identify and contain breaches an average of 28 days faster than those using traditional security models. This makes Zero Trust one of the most effective best practices for cybersecurity market analysis in 2026.
4) Deploy AI Powered Security Solutions
In 2026, AI became the central battlefield in cybersecurity. While attackers leverage AI for sophisticated attacks, defenders must deploy equally advanced AI powered cybersecurity solutions to protect their organizations.
A) Automated Threat Detection: Implement AI systems that provide continuous, real time monitoring, quickly detecting anomalous behaviors and identifying threats before they cause damage.
B) Predictive Threat Intelligence: Use AI to analyze historical attack patterns and real time data to forecast potential attacks and proactively identify vulnerabilities.
C) AI Security Operations Centers: Operationalize AI across your entire SOC, enabling AI agents to summarize alerts, surface root causes, and propose remediation actions, dramatically reducing alert fatigue.
D) Behavioral Analytics for Insider Threats: Deploy machine learning models that establish baseline behaviors and flag deviations that may indicate compromised accounts or malicious insiders.
E) Anti AI Defense Systems: Implement specialized cybersecurity services that protect against AI generated deepfakes, synthetic media attacks, and prompt injection risks targeting your enterprise AI systems.
Adopting AI powered cybersecurity solutions, including Cloud Security Posture Management, is no longer optional but essential for maintaining a competitive security posture in 2026.
5) Prepare for Quantum Computing Threats
Quantum computing represents both an incredible opportunity and an existential threat to current encryption standards. Leading cybersecurity experts warn of “Harvest Now, Decrypt Later” attacks, in which adversaries steal encrypted data today with the intention of decrypting it when quantum computers become powerful enough.
CEOs must prioritize quantum readiness as a critical component of cybersecurity best practices:
A) Crypto Inventory Assessment: Conduct a comprehensive inventory of all encryption methods currently in use across your organization.
B) Post Quantum Cryptography (PQC) Migration: Begin transitioning to quantum resistant encryption algorithms that can withstand quantum computing attacks.
C) Hybrid Cryptographic Solutions: Implement hybrid systems that combine traditional and quantum resistant encryption during the transition period.
D) Crypto Agility: Develop the organizational capability to adapt to new cryptographic standards as they evolve quickly.
By 2026, 20% of leading organizations have allocated dedicated budgets to counter quantum related threats, recognizing this as one of the most forward looking best cybersecurity practices.
Useful link: 8 SaaS Security Best Practices to Secure Applications
6) Control and Monitor Access to Sensitive Data
Implementing granular access controls is fundamental to best practices for cybersecurity. Follow the principle of least privilege, which means granting users only the necessary permissions required to perform their specific tasks. In 2026, this extends to AI agents and automated systems, which must be treated as distinct digital actors with managed identities.
Essential permission levels to consider:
A) Full Control
B) Modify
C) Read Only Access
D) Conditional Access
Controlling and monitoring access through these layered approaches significantly minimizes the risk of unauthorized individuals accessing sensitive data while supporting cybersecurity best practices for business.
7) Secure Physical Infrastructure and Devices
Physical security remains a critical element of comprehensive cybersecurity strategies and best practices. Lock all workstations when not in use to prevent unauthorized access or device theft. Implement biometric authentication combined with behavioral analytics to prevent unauthorized physical access.
Set up BIOS level passwords and firmware security on all devices to prevent attackers from bypassing operating system security. Extend security controls to all edge devices, including USB flash drives, Bluetooth devices, smartphones, tablets, laptops, and IoT sensors. Use hardware based encryption and secure boot mechanisms to ensure device integrity.
8) Implement Comprehensive Endpoint Security
The endpoints in your network remain prime targets for sophisticated attacks. Establishing a robust endpoint security infrastructure is critical to minimizing breach risks and implementing best cybersecurity practices.
A) Next Generation Antivirus
B) Endpoint Detection and Response (EDR)
C) Advanced Anti Spyware
D) Next Generation Firewalls
E) Browser Security
These endpoint security measures represent essential cybersecurity solutions for modern enterprises.
9) Document Your Security Policies and Procedures
Relying on verbal communication or assumptions regarding cybersecurity services is wholly insufficient for enterprise risk management. CEOs must ensure that all cybersecurity best practices, policies, and protocols are meticulously documented, version controlled, and accessible.
This documentation facilitates training, provides operational checklists, and ensures the transfer of critical knowledge across your organization, supporting enterprise wide cybersecurity best practices for business.
10) Adopt a Risk Based Security Approach
Modern cybersecurity strategies and best practices require a sophisticated understanding of your unique risk profile.
Conduct assessments that:
A) Identify and Classify Critical Assets
B) Assess Current Risk Exposure
C) Evaluate Third Party Risks
D) Analyze Business Impact
Prioritize investments based on risk adjusted ROI
A risk based approach enhances compliance, strengthens your resilience, and reinforces your broader best practices for cybersecurity.
11) Invest in Continuous Security Awareness Training
Human error remains one of the most important vulnerabilities in any security program. With AI enabling more advanced social engineering attacks, continuous training has become an essential part of cybersecurity best practices.
Effective cybersecurity best practices for business include simulated phishing, role based training, executive briefings, and behavior monitoring programs that strengthen awareness and reduce risk.
12) Implement Multifactor Authentication and Passwordless Solutions
Multifactor authentication remains a cornerstone of best cybersecurity practices, adding essential layers of protection during account login.
In 2026, organizations are moving toward passwordless systems supported by passkeys, hardware tokens, and biometric tools. These are now considered among the most effective cybersecurity solutions for preventing credential based attacks.
The Business Impact of Cybersecurity
Rising cyberattacks continue to strain enterprises. With the average data breach costing $4.88M in 2024 and global cybercrime projected to hit $10.5T by 2025, cybersecurity is no longer optional. Executives who invest in cybersecurity best practices and modern defense frameworks protect revenue, customer trust, and long term business continuity.
1) Why Cybersecurity is a Strategic Imperative?
Strong security goes beyond compliance. Adopting best practices for cybersecurity market analysis reduces risk exposure, ensures operational resilience, and strengthens competitive positioning. Organizations that modernize their security posture face fewer disruptions and earn higher stakeholder confidence.
2) Why Enterprises Choose Veritis?
Veritis brings 21+ years of experience, multicloud expertise across AWS, Azure, and GCP, and a proven record of delivering cybersecurity solutions that scale. As a Stevie Award winning team with 100% project success, we help enterprises embed cybersecurity best practices for business across people, processes, and technology.
3) What Veritis Delivers?
Our certified experts provide end to end cybersecurity services, including:
- Risk assessments and security posture reviews
- Security policy design and compliance alignment
- Advanced threat detection and response
- Incident response and disaster recovery planning
Each engagement is tailored to your risk profile and industry demands.
4) Your Partner for Secure, Future Ready Growth
Partnering with Veritis gives your organization the depth, precision, and leadership required to stay ahead of evolving threats. With the right cybersecurity strategies and best practices, enterprises can protect sensitive data, enhance resilience, and build lasting customer trust.
Case Study: Cybersecurity Transformation for a Fitness and Wellness Platform
Veritis partnered with a leading fitness and wellness platform to strengthen its security posture at a time when digital threats and data breaches were rapidly increasing. The client faced several challenges, including inadequate threat detection, limited user data protection, and security vulnerabilities across their digital services. These issues highlighted the need for structured cybersecurity best practices and modern cybersecurity solutions.
Veritis implemented a comprehensive cybersecurity framework involving secure application development, advanced data encryption, continuous monitoring, and role based user access controls. This approach aligned with best practices for cybersecurity market analysis and significantly enhanced the platform’s ability to detect threats early, protect sensitive customer information, and meet compliance requirements.
The engagement demonstrated how applying cybersecurity best practices for business can reduce breach risks, improve operational resilience, and build long term digital trust. It also underscored the value of partnering with experts who deliver tailored cybersecurity services backed by proven experience.
Read the complete case study: Cybersecurity Transformation for a Fitness and Wellness Platform.
Conclusion
Cybersecurity best practices extend beyond technical controls. Regular data backups, strong encryption, and disciplined password hygiene all help reduce risk. While no organization can eliminate every threat, applying the right cybersecurity best practices for business significantly lowers the likelihood of cybersecurity breaches and strengthens overall resilience.
Real protection requires continuous employee education, clear policies, controlled access, strong endpoint security, and structured risk assessments. These best practices for cybersecurity market analysis form the foundation of a secure, compliant, and future ready enterprise.
Secure Your Business Today
Cybersecurity is now a board level priority that demands consistent leadership and strategic action. This is where Veritis becomes a trusted partner. With two decades of experience, award winning expertise, and proven cybersecurity solutions, Veritis helps organizations build, modernize, and scale their security programs with confidence.
Don’t wait for an incident to take action. Partner with Veritis and protect your business with a tailored strategy designed for the threat era.
Talk to our experts at Veritis to develop a tailored cybersecurity strategy for your organization.
Got Questions? Schedule A Call for Cybersecurity Services
Also Read: