
With the introduction of the cloud, there is no aspect of your IT infrastructure that other people or businesses cannot handle for you. Many companies rely on Amazon AWS to provide the computing and storage resources required to run their websites and applications. Others purchase a complete platform from a third-party vendor that includes servers, databases, middleware, operating systems, and other components. They use hypervisors and other tools to access high-level APIs from online services.
Others, however, rely on software and application providers from outside sources. Now, rather than investing in developing their infrastructure or building, maintaining, and creating these resources, companies can more easily, quickly, and affordably meet their IT requirements. In addition, it has become possible to access almost everything as a service over time, including storage, logging, disaster recovery, and backends. Even services like security are now possible.
Security as a Service, or SECaaS, is what you offer when outsourcing your security to a cloud business. Of course, you must continue to pay the vendor for their services after they have been integrated into your infrastructure. However, you will receive the assistance you require. You won’t need to invest in personal, software, or other resources.
What is Security as a Service (SECaaS)?
Security as a Service (SECaaS) enables companies to outsource their cyber security management as a service requirement. Outsourced data security solutions include anti-virus protection, intrusion detection, and data loss prevention. In addition, businesses can benefit from the expertise and innovation of committed cyber security as a service team. Which specializes in breach prevention in security as a service in a cloud computing environment by working with a SECaaS vendor.
Security as a Service eliminates the need for local delivery of data security solutions. Wherein your IT department installs anti-virus software, spam filtering software, and other data security solutions on each computer. Or else keeping the program up-to-date or instructing them to use it on the network security protection or server in your place of business.
The traditional method is also pricey. You must pay upfront expenditures for the hardware and ongoing license fees to use the program. However, using the same technologies with just a web browser is now easy and affordable thanks to security as a service.
In the same way, that software as a service (SaaS) companies do, security as a service provider frequently charges a monthly subscription fee to pay for the expenses of outsourcing services. However, they offer security for your cloud-based apps, data, and operations rather than granting you access to a tool or platform.
Useful link: Things CTO Needs to Consider Selecting a Cloud Network Security Solution
Benefits of Security as a Service (SECaaS)
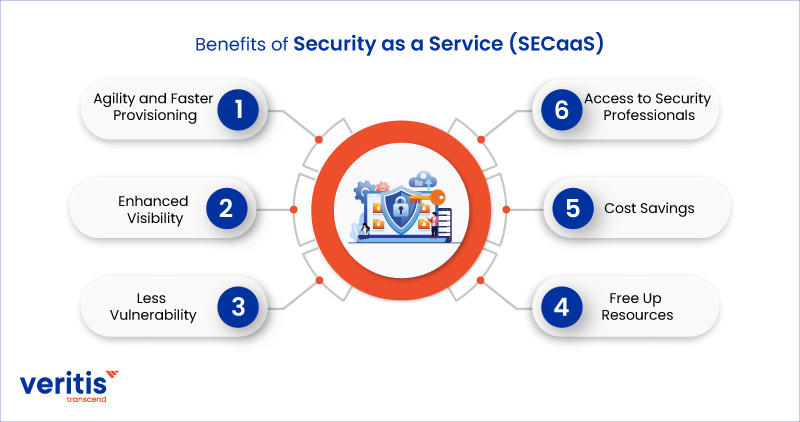
1) Agility and Faster Provisioning
The ability to immediately grant your users access to these tools is one of the best aspects of as-a-service solutions. In addition, SECaaS solutions are available on demand where and when you need them and may be scaled up or down as needed. That means there is no longer any ambiguity regarding deployment or upgrades because your SECaaS supplier will handle both for you and make it all apparent through a web-based dashboard.
2) Enhanced Visibility
Your business can see all its traffic, applications being used, and any hacked IoT devices, threats, and policy violations being stopped. And much more in real-time, thanks to cloud security as a service. An integrated cloud solution offers a centralized view of all activities across cyber security services, including firewall, sandbox, secure web gateway, advanced threat protection, data loss prevention, bandwidth control, and more. This resembles a security information and event management (SIEM) system.
3) Less Vulnerability
Attackers increasingly focus on mobile users and exploit mobile devices as a beachhead to assault business systems. Since bad actors today are aware that legacy security in the data center cannot protect these users.
If you can’t secure every link, your network security protection is exposed to risk. Enterprise security holes brought up by off-net users and people connecting directly to cloud apps and the public internet are filled by network security as a service.
4) Free Up Resources
Your IT teams may concentrate on what is critical to your company when security provisions are managed externally. SECaaS frees up resources and provides complete visibility through management dashboards. A group of outsourced security experts skillfully manages your IT security, assuring you of its effective management.
You can also decide to delegate management of security procedures to your IT staff. You can empower your IT teams to take control of security processes and manage all policy and system changes through a web interface.
5) Cost Savings
The ability of a firm to save money is among the main advantages of a security as a service approach. A cloud-delivered service is frequently offered in subscription tiers with various upgrade possibilities. It allows a firm to pay for what it requires at the time. Additionally, expertise is optional.
6) Access to Security Professionals
When you utilize SECaaS, you get seasoned, qualified security experts instead of your in-house team, which may need more specialized knowledge or be overburdened with other tasks and unable to devote the necessary attention to cybersecurity.
Useful link: 9 Data Security Best Practices for Your Business
Challenges of Security as a Service (SECaaS)
Cloud security challenges exist for all security solutions. With an outsourced security solution, there are several issues to consider, such as the following:
1) Eliminating Legacy Hardware Through a Migration
It is impossible to overestimate the advantages of cloud security as a service. Still, your company may be left susceptible during the transitional period between dumping legacy security and using the cloud.
2) Misconfiguration Risk
This relates to accountability, but it’s important to note that configuration errors are the leading source of cloud data breaches. In addition, there may be issues if your team or a cloud provider makes a provisioning error.
3) Accountability
According to a shared responsibility model, the managed security service provider and the client share some blame for a cloud service incident. However, no matter who is at fault, the consequences are the same if security problems occur during network security as a service deployment. Companies can reduce the risks of outsourced security solutions by implementing and enforcing rules that address vulnerabilities to cloud security.
Gartner predicts that until 2025, customers would be held liable for 99% of cloud security failures rather than cybersecurity service providers.
How to Select the Best Security as a Service (SECaaS) Provider

1) Service Availability
Make sure the SECaaS provider you select delivers the best uptime for cloud applications, security dashboards, and network security protection resources. A technically competent customer service team should also be available to assist you immediately with unforeseen problems.
2) Partners as Vendors
Research the vendor partners of the security service you are considering. Make sure the security as a service supplier utilizes cutting-edge technology and customary cloud services.
3) Service Level Agreement (SLA) and Response Time
Discuss the vendor’s response time when you receive a demo of their services. Before signing the agreement, you can also include a condition in the contract specifying a specific SLA and response time.
4) Disaster Recovery Planning
A disaster recovery plan is crucial to business continuity and can help you avoid losing thousands of dollars during a disruption. Therefore, your SECaaS solution must offer disaster recovery alternatives that can specifically adapt to your company’s requirements.
5) Vendor Lock-in
Avoid signing up for subscriptions with vendor lock-in. Instead, always select subscriptions with flexible terms and simple cancellation procedures.
6) Reporting
Your managed security service provider should grant you access to a simple security tool where you can keep track of the overall security strategy.
Features of Security as a Service (SECaaS)
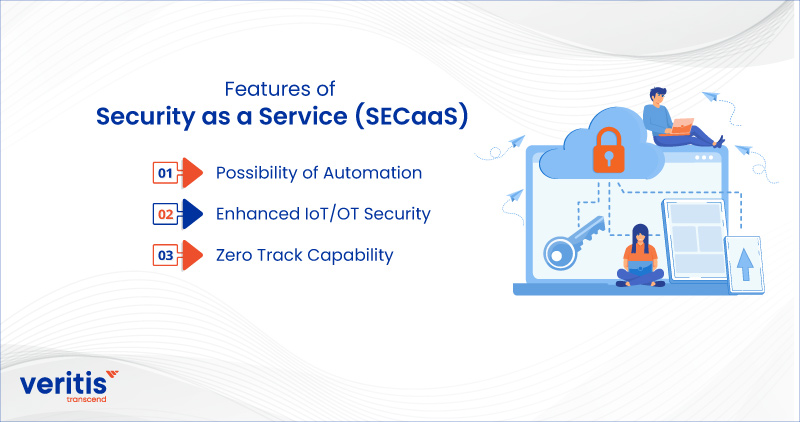
Service-based security on-premises solutions need more special capabilities that technology offers.
1) Possibility of Automation
Cloud security architects can design logic and schema to automate specific operations because the cloud isn’t constrained by hardware and can be continuously improved. As a result, they are making life easier for administrators, threat hunters, SecOps teams, and so on.
2) Enhanced IoT/OT Security
When securing the data that enters and leaves IoT and OT-connected machines, devices, and other objects, legacy security cannot scale to meet modern data protection standards. As your organization generates more data, SECaaS scales to secure it.
3) Zero Track Capability
Cloud-delivered architecture is the only way to achieve zero trust security. No matter what devices users sign in from, security policy is always followed by zero trust. This cannot be done using legacy architectures.
Final Thoughts
Enterprises and SMBs are increasingly choosing security as a service solution. However, the growing use of SECaaS is being fuelled by the lack of security resources, such as qualified professionals and tools and skills in general, as well as the constantly evolving threat landscape.
Today, outsourcing the management, application, and control of the intricate security field makes sense for many businesses, and it’s proving to be a financially wise investment for those who take advantage of it. Veritis, the Stevie Award winner, offers cloud-delivered endpoint security and workload protection for your SECaaS requirements.
Got Questions? Schedule A Call
Also Read:
- What is Cloud Security Posture Management?
- What is Cloud Computing Security?
- How to Enhance Security in the Multi-Cloud Era
- What is Operational Security (OPSEC) and How Does it Protect Critical Data?
- Security Breaches Rising Exponentially; Weak Authentications Exploited
- Debunking Myths Around Zero Trust Security!