
Over the past decade, enterprise software vendors have changed the way how they deploy their solutions. The default offering was implementing a Commercial Off-the-Shelf (COTS) software package using the client’s on-premise hardware infrastructure. However, no one is doing that any longer because it needs to be updated. Nowadays, the preferred method is to keep your data and software “in the cloud.” Software as a Service, or SaaS, refers to this creative strategy.
SaaS may lower operating costs, promote quicker innovation, and reduce spending on outmoded technologies, but it could be better. In any case, it still needs to. The issue is that powerful cloud services providers such as Google Cloud, Microsoft Azure, and Amazon Web Services must emphasize security adequately in their deliverables.
Three billion USD in financial damages are happening yearly due to cyberattacks. The US giant IBM estimated the average loss per breach to be 4.24 million USD. Furthermore, experts predict that cyber-attacks like these will result in 10.5 trillion USD in damages by 2025.
Although SaaS is unquestionably the most straightforward and convenient option for companies to profit from the cloud, these services are also supplied online. As a result, it may be simple for threat actors to access sensitive data or for data leaks to occur. A SaaS misconfiguration led to one or more security incidents for 43% of organizations.
What is SaaS Security?

SaaS security is about maintaining, monitoring, and protecting sensitive data from cyber threats. Organizations are more exposed as cloud-based IT infrastructures gain in effectiveness and scalability.
SaaS security, or Software as a Service security, describes the protection measures taken to protect data in SaaS applications that run in the cloud. It includes procedures companies use to secure private consumer and sensitive corporate data in the cloud. Service providers and their clients share responsibilities for SaaS security risks.
SaaS application security is essential to efficient SaaS company administration, addressing goals such as decreasing wasted licenses, getting rid of shadow IT, and gaining high visibility to reduce security concerns.
Most enterprises use cloud environments, and many of them have multi-cloud deployments. The typical business uses services from five different cloud providers. Although it makes sense that cloud computing is popular, it also presents several security risks, such as compliance issues, contract violations, insecure APIs, and misconfigurations.
Software-as-a-Service (SaaS) settings are a desirable target for hackers. Because they frequently hold a significant variety and quantity of sensitive data, including payment cards and personally-identifying information. Therefore, firms need to give SaaS data security a top priority.
Useful link: 8 Best Business Continuity Management Software Solutions
Why is SaaS Security Important?
The adaptability, efficiency, and scalability of Software as a Service (SaaS) have contributed to its growing popularity in recent years. However, SaaS companies and their customers encounter significant security obstacles due to this increased demand. As a result, protecting SaaS security is critical.
- It assists in maintaining compliance with security standards and requirements.
- It reduces the chances of cyber-attacks and data breaches by ensuring the security and protection of hosted applications and data.
- Encourages clients to have more faith in the SaaS provider
- Sensitive information would be well-secured and protected from cyber threats, including hackers, malicious insiders, and other hazards.
- SaaS security aids in avoiding serious repercussions like legal liabilities, reputational harm, and client loss.
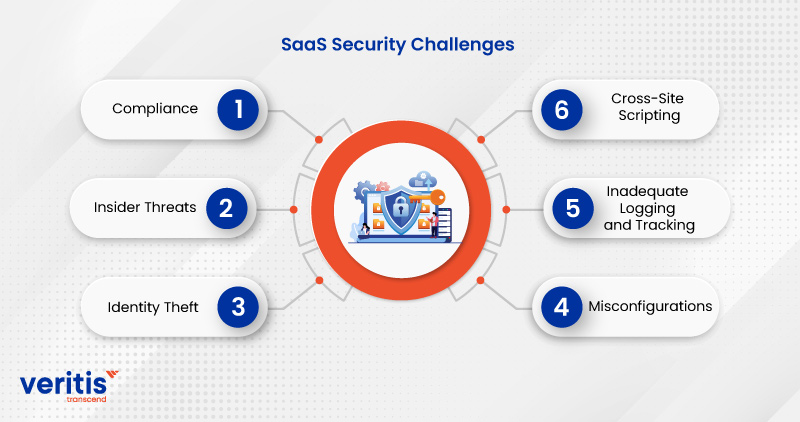
SaaS Security Challenges
Vulnerabilities and concerns of data breaches are among the SaaS security risks that cost companies millions annually. Threats to cloud services are multiplying at an accelerated rate. Organizations that use cloud storage rely on a third-party supplier for security and make their data accessible through the Internet.
1) Compliance
Every industry has specific security and auditing requirements, and noncompliance can result in financial or legal consequences. In addition, depending on their sector and the kind of data they retain and process, many organizations are subject to laws like GDPR, PCI-DSS, HIPAA, and SOX.
These standards include specifications for undertaking security testing, performing routine audits, and protecting data in the cloud. Protecting sensitive data is a top issue, and you must keep an eye on your SaaS apps and offer the necessary logs and audit trails.
2) Insider Threats
SaaS apps and the companies employing them may be exposed by careless staff members and nefarious insiders who intentionally or unintentionally leak data. Any data stored in the cloud is at risk for security breaches, primarily if you use weak passwords and shared login information. In addition, SaaS application development security problems frequently result from sharing data externally or making it open to access from all platforms.
3) Identity Theft
SaaS products regularly use online payment techniques that increase identity theft risk. Lightweight Directory Access Protocol (LDAP), firewalls, and data encryption in transit and at rest are just a few security measures needed to secure payment card information and user identity.
4) Misconfigurations
Inadequate security settings can leave computing resources open to hostile activities. In accordance with the Open Web Application Security Project (OWASP), misconfigurations are the most frequent security vulnerability. Therefore, to protect SaaS applications, one should ensure to configure all cloud-based tools properly and update them on schedule.
5) Inadequate Logging and Tracking
Electronic audit logs are crucial for identifying fraudulent or unauthorized activities, yet many companies neglect to implement or monitor them in time to detect risks. To locate and stop breaches, you should establish enough monitoring across your apps and frequently review the logs.
6) Cross-Site Scripting
In an XSS attack, malicious code is injected into web pages that end users view. It impacts the majority of apps and is the second most frequent security vulnerability. With the most recent versions of Ruby on Rails or React JS, XSS can be automatically blocked.
Useful link: 12 Best Features for Work Management Software That Matter Most
Best Practices for SaaS Applications to Secure Data

1) Monitoring and Logging
It’s vital to record all successful and unsuccessful access attempts into the SaaS company system. Any changes to data have the same effect. This action is crucial for preventing data breaches and setting up future security plan arrangements.
2) Data Encryption
Cloud apps must rely on data encryption and key management because they cannot be secured using conventional techniques like firewalls. Many clients prefer to manage their keys through a nearby hardware facility because they are uncomfortable leaving this crucial task in the hands of data vendors.
Transport Data Encryption (TDE) allows for the protection of data “in motion.” However, other data transfer over HTTP or FTP may be risky, so it should be secure with tools like Transport Layer Security (TLS).
3) Identify and Map Your SaaS Data
The secure discovery, tagging-based classification, mapping, and monitoring of all data in use, transit, or at rest are the top goals for SaaS security professionals. SaaS developers must know, monitor, and secure their unmanaged and SaaS cloud security shadow data. Understanding where your data is at all times and ensuring the highest protection level depends on the data navigation process.
The polar security solution makes identifying and tracking your sensitive known and shadow data simple before automating data labeling to highlight sensitive and essential data repositories consistently and broadly.
4) Better Authentication
Deciding how users should be granted access to SaaS services is challenging because SaaS cloud security providers can handle authentication in multiple ways. Vendors do not universally support integration with customer-managed identity providers such as Active Directory (AD) with Security Assertion Markup Language, Open Authorization, and OpenID Connect.
Similarly, some vendors enable multi-factor authentication while others do not. The security team must comprehend which services are being used and the supported alternatives for each service to navigate the many Software as a Service (SaaS) implementation solutions offered.
Depending on the organization’s requirements, this context enables administrators to select the best authentication techniques. If the SaaS provider offers it, using single sign-on (SSO) linked to AD is a wise choice as it ensures that the account and password policies correspond to the services used for the SaaS application development.
5) Effective Identity and Access Management Controls
IAM (identity and access management) technologies substantiate the identity of users. Having the ability to integrate with IAM tools is essential for SaaS consumers. Business users do not want to use a different password when logging into a different area of an enterprise-wide platform. Therefore, any IAM system must include sophisticated access control to identify who accessed what and when.
6) Maintain Visibility
Track all SaaS usage, evaluate security logs from the service provider, and analyze information from security tools like CASBs. A high level of security is required for SaaS implementation solutions, just as for any corporate program. Therefore, ensure your security and IT staff are aware of this. In addition, incorporate monitoring into your risk management plan to ensure users handle SaaS applications safely.
7) SaaS Security Posture Management (SSPM)
SaaS Security Posture Management SSPM aims to prevent accidental vulnerabilities that develop during the SDLC. SSPM offers a consistent level of transparency throughout the entire cloud environment.
It eliminates the requirement to examine numerous distinct endpoints from various providers. While speeding up delivery, this process decreases misconfigurations. SaaS data security is regulated and automated by SSPM.
8) Implement a Security First Software Development Life Cycle
A security focus is added to the software development process by employing a safe security-prioritized software development life cycle (SDLC). Further enhancing the SDLC’s security profile is threat modeling and penetration testing.
Conclusion
Incorporating the best security practices into your SaaS application is more critical than ever for SaaS development teams. Therefore, it is essential to maintain its significance to maintain user security and the organization’s operation.
Veritis, the Stevie Award winner, has extensive expertise in creating safe SaaS applications for Fortune 500 companies and startups. We have assisted numerous companies and individual entrepreneurs in making their SaaS concepts become digital realities.
Got Questions? Schedule A Call
Also Read:
- What’s SaaS, and What are the SaaS Tools You Should Use?
- What is Cloud Computing Security?
- How to Enhance Security in the Multi-Cloud Era
- What is Operational Security (OPSEC) and How Does it Protect Critical Data?
- Security Breaches Rising Exponentially; Weak Authentications Exploited
- What is Security as a Service (SECaaS)?