
Meeting compliance and regulatory requirements is one major challenge to every organization globally. Given today’s cybersecurity challenges, organizations are under the constant pressure of penalties for failing to meet compliance requirements. So, every business must secure its assets and data from intruder attacks.
Thanks to the measures aimed at ensuring organizational IT security and data safety. Moreover, a robust Identity and Access Management (IAM) system offers your organization’s first line of defense. For that to deliver results, you need to have a checklist.
Identity and Access Management is a fundamental security framework that facilitates associating authenticated users with the appropriate resources when they require access. An effective IAM solutions configuration mitigates the likelihood of data breaches and significantly raises the barriers for cyber adversaries. As such, IAM assumes a pivotal role as an indispensable cybersecurity tool for contemporary enterprises.
Some of the stats related to IAM
- 92% of IT decision-makers recognize IAM as essential to their organization’s security posture. (Source: RightScale’s 2023 State of the Cloud Report)
- 78% of organizations are investing in IAM to improve their security posture. (Source: Gartner’s 2023 Identity and Access Management Magic Quadrant)
- 65% of organizations are using IAM to accelerate their digital transformation initiatives. (Source: Flexera’s 2023 State of Cloud Computing Report)
- 58% of organizations are using IAM to optimize their cloud costs. (Source: Cloudability’s 2023 Cloud Migration Report)
- The global IAM market is expected to reach USD 37.48 billion by 2028, up from USD 23.86 billion in 2023. (Source: Fortune Business Insights)
What is the IAM strategy?
IAM strategies encompass a comprehensive framework of policies, procedures, and technologies designed to administer digital identities and regulate resource access.
The attainment of network, system, and data security hinges on the meticulous governance of resource access, determining which individuals are granted access to specific resources under specified circumstances. This control can manifest as a primary password or PIN code mechanism or as a robust multifactor authentication solution, which may include biometric authentication for enhanced security.
Why Audit and Report IAM?
The process of auditing and reporting on IAM (Identity and Access Management) serves several crucial purposes:
- It aids IT professionals in enhancing both IAM security and compliance measures.
- It contributes to the improvement of overall efficiency and performance within an organization.
- It enhances visibility and accountability across IAM assessment
- It supports informed decision-making and strategic planning.
Auditing and reporting in IAM solutions have practical benefits, including detecting unauthorized access or identity theft. It also helps optimize access provisioning, de-provisioning, authentication, authorization, and role management. Furthermore, organizations can generate valuable evidence for audits or investigations by tracking and documenting who has access to specific resources, when, how, and why.
Analyzing and evaluating IAM data, trends, issues, and opportunities can provide valuable insights and recommendations for continuous improvement. This holistic approach to auditing and reporting safeguards an organization’s IAM security and compliance and contributes to its overall operational excellence and strategic growth.
What Skills Are Required for IAM Audit and Reporting?
Professionals engaged in identity and access management audit and reporting require a diverse skill set encompassing IAM proficiency, data analysis and visualization, effective communication and collaboration, and critical thinking and problem-solving abilities. These skills are vital for ensuring the effectiveness of IAM assessment processes.
Firstly, they should comprehensively understand IAM principles, standards, IAM best practices, and challenges. This includes familiarity with the specific IAM policies and procedures for their organization and industry.
Secondly, they need the capability to collect, process, interpret, and present IAM data clearly and comprehensively. This involves data analysis and visualization skills, which enable them to extract meaningful insights from complex information.
Furthermore, effective communication and collaboration skills are crucial as they must interact with various stakeholders, sharing and explaining identity and access management audit findings. This facilitates understanding and cooperation across the organization.
Finally, identifying, analyzing, and resolving issues or gaps in identity and access management audit and reporting is essential. Professionals should be adept at proposing and implementing solutions or enhancements to ensure the ongoing effectiveness of IAM best practices.
What Tools Are Required for IAM Audit and Reporting?
IT professionals have many tools when considering identity and access management audit and reporting tasks, offering flexibility based on their needs, preferences, and budget constraints. They can opt for comprehensive software or cloud-based systems like Microsoft Azure Active Directory, Okta, or IBM Security Verify, which offer integrated functionalities for managing various aspects of IAM solutions. These platforms also feature specific components or functions dedicated to auditing or reporting IAM activities and outcomes.
Alternatively, there are standalone software or cloud-based tools and applications with a specialized focus on auditing or reporting IAM data and information. Examples include Varonis Data Privilege, SailPoint Identity Now, and Splunk Enterprise Security. These IAM tools provide tailored solutions to address specific IAM auditing and reporting requirements.
What to Consider Before Implementing IAM Strategy?
A significant portion of the preparatory effort in constructing an identity and access management solution strategy occurs before the implementation phase commences. Thorough planning is paramount to strike a harmonious equilibrium between user-friendliness and robust user access IAM security. Here are several factors to contemplate during the project’s inception:
1) Network Architecture Mapping
The initial step in IAM assessment implementation involves comprehending the existing network resource structure. This entails mapping out on-premises router and server configurations and locally utilized critical applications. Additionally, create a schematic representation of remote work connections and any cloud-based services users access. Document the current IAM procedures and scrutinize how users access and share data. This information is the foundation for transitioning from outdated IAM best practices to an adequate and pertinent deployment.
2) User Community and Privilege Assessment
Planners must comprehensively understand the individuals utilizing resources safeguarded by IAM tools. Establish a directory encompassing all active users and associate them with their access levels and business requirements. It is prudent in IAM projects to identify privileged users with extensive network access and are a primary target for external attackers.
3) Data and Application Risk Evaluation
Conduct a thorough risk assessment for each application. Ascertain the locations of confidential data within the network environment and identify individuals accessing this sensitive information. Employ sound risk management principles to tailor the IAM strategy towards safeguarding these high-value assets. The objective is to balance user convenience and security, potentially employing more robust IAM assessment controls for high-value applications.
4) Data Governance Enhancement
Optimizing existing data storage practices is beneficial before implementing an access management strategy. Standardize data formats to align with IAM technologies and organize data for improved visibility by security managers. Evaluate IAM security policies to ensure they incorporate robust data security regulations, including repercussions for data misuse.
5) Selection of Appropriate IAM Tools
Delve into IAM solutions and explore various technologies. Most contemporary organizations find value in cloud-based IAM solutions, though legacy-focused IAM options exist. Seek out products that provide essential IAM functionalities such as authentication, authorization, single sign-on, auditing systems, and identity federation. Look for providers that facilitate the migration of identities from existing IAM tools, facilitating seamless transitions from legacy solutions to multi-cloud hybrid environments.
How to Create an IAM Strategy?
The planning phase acts as the cornerstone for establishing organizational knowledge. The first step entails consolidating this knowledge and formulating a pragmatic IAM (Identity and Access Management) strategy. While IAM strategies may differ based on the particular business context, they generally include fundamental IAM elements:
1) User Management
IAM systems should facilitate the establishment of user profiles or identities that authorize access to relevant resources and establish connections with resources via federation systems. Identity management strategies should comprehensively cover provisioning and de-provisioning processes as essential components of identity lifecycle management.
2) Authentication
Access control systems are required to verify the identity of every user upon entry. Utilizing multifactor authentication, with a preference for hardware tokens, is regarded as a best practice. Password policies should be designed to mandate the utilization of robust passwords that are updated regularly.
3) Authorization
Authorization ensures that users’ access privileges align with their designated role within the organization. Users should exclusively access business data pertinent to their responsibilities, while all other resources remain restricted. Moreover, implementing Privileged Access Management (PAM) oversees administrative accounts with substantial access to sensitive data.
Additionally, authorization can involve setting time limits granting restricted access to resources throughout a user’s session. Alternatively, broader privileges can be established based on predefined roles. The automation of privilege management serves the dual purpose of time efficiency and minimizing the potential for human error in access allocation.
4) Single Sign-On (SSO)
Single Sign-On (SSO) is a valuable enhancement to IAM systems, bringing cloud-based and on-premises resources together into a unified access portal. Users input a single set of credentials, and the SSO system utilizes privileged databases to grant authorization to users across the entirety of the network environment.
5) User Directories
IAM requires an up-to-date and organized directory of network users, which serves as a central reference point linking to Privileged Access Management (PAM) and IAM tools. Although Microsoft Active Directory is a common choice for many networks, hybrid cloud configurations may utilize various directory formats. The IAM strategy should focus on consolidating these directories to simplify access management, potentially involving a phased migration of existing identities to cloud-based directory systems.
6) Identity Federation
Federated identities empower users to access third-party Software as a Service (SaaS) applications and cloud platforms. Although cloud service providers commonly provide federation capabilities, network administrators are responsible for incorporating identity federation into their overall IAM (Identity and Access Management) strategy.
7) IAM Auditing
Effective governance and risk management practices emphasize the importance of routinely auditing identity and access management solutions. The chosen strategy should support recording access requests and user activities, along with comprehensive documentation of security alerts. Strategists must establish connections between audit data and compliance plans about relevant data regulations. Furthermore, the IAM solution should align seamlessly with compliance objectives, including but not limited to GDPR or HIPAA, across its various components.
Useful Link: 8 Best Practices for Robust Identity and Access Management (IAM) Strategy
Here are 8 checklist points that can make the IAM system work the desired way in line with the IAM Audit requirements.
The 8-Point IAM Audit Checklist includes:
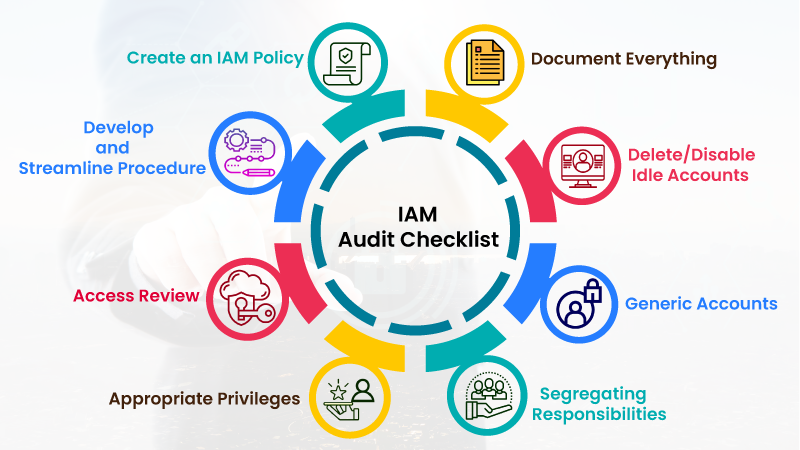
1) Create an IAM Policy
Ensure the IAM process is clearly defined and crucial to your organizational security policy. Creating an IAM policy document is strongly recommended for the following reasons:
- Meet compliance requirements
- Manage user access and authorization
- Define access to stakeholders who can help make a robust IAM policy
- Robust incident response
Moreover, reviewing the policy document regularly is more important to ensure that the proper IAM best practices are updated and followed on time.
2) Develop and Streamline Procedure
It’s not done with creating a policy; you see desired results only if implemented properly. For that, you need to develop a procedure involving all stakeholders in the IAM assessment process and define roles.
The streamlined procedure should have a list of stakeholders with assigned responsibilities and actions they are accountable for.
3) Access Review
In any organization, users, roles, and responsibilities keep changing. In such a scenario, reviewing access and authorizations given to different users is essential. Formulate a user access review process to ensure the proper access is given.
Keep reviewing that at different intervals to avoid discrepancies. Policy-Based Access Control (PBAC) is one means to execute the user access review process.
4) Appropriate Privileges
This is the crucial point that defines the robustness of an IAM system. Despite being known, this is often ignored. It’s essential to see that user access remains limited to ‘particular’ job requirements and not further. Following the Least Privileged Account principle is recommended, which calls for setting maximum resource limitations.
If you grant special privileges, revoke them immediately after the designated temporary usage period ends.
5) Segregating Responsibilities
This is one crucial aspect that can avoid possible risks in the first step. Segregating duties among people keeps them limited to their respective functions, and none gets complete access. In the case of critical tasks, break them into smaller ones and assign them to multiple people. This keeps every process and its associated IAM security functions independent from others.
In case of any breach of a process, the threat scope remains limited to that particular process, leaving the rest of the system.
6) Generic Accounts
Generic accounts are required in every organization to execute regular and common activities like training and testing. However, keeping them idle can lead to IAM security risks. Never assign admin rights to generic accounts, and delete the unused ones.
It’s important to see strong passwords bind them to avoid breaches through default settings. Privileged Access Management (PAM) and PBAC can completely control generic accounts.
7) Delete/Disable Idle Accounts
Keeping your IAM system clean, secure, and updated is essential. Delete any unused user accounts (generic or important ones) lying idle. Leaving them is like allowing them to grow further and welcome threats through them.
Delete inactive users lying individually and in groups. Make sure users are only present in their relevant groups. Conduct a regular review of group policies and delete exposed login details.
8) Document Everything
Back to where we started. We started with documenting policy for its effective implementation. But it’s important to document everything in implementation too. This forms as a trial for future implementations and helps comply with rules every time.
Documentation is vital to the identity and access management audit process, where you need to share administration activities, policies, and usage documented. Moreover, the documentation process gives a better understanding of the entire IAM system, helping you find ways to improve it further.
Useful Link: IAM Best Practices for Optimal Cloud Security
What Makes an IAM Strategy?
Based on the above checklist, we can list down what a robust IAM strategy consists of:

- Automated Provisioning and De-provisioning activity
- Single Sign-on, Multi-factor authentication, and PAM methods
- Centralized Management
- Manage by Groups
- Compatibility with multiple platforms or OS
- Extensibility and scalability to SaaS Apps
- Automatic and Customizable Password Management
- Use of standard core protocols
Based on these points, you can easily measure the robustness of your organization’s IAM system by scores. Measured out of 10:
- A score of 0-4 indicates your current IAM program is causing a risk to your organizational IAM security and needs a makeover.
- A score of 4-7 indicates your IAM program is not at risk but is not adding to your progress. That could be rising incompatibility issues or lagging in some areas.
- A score of 7-8 indicates your IAM program is serving you well but can be improved further to fight future challenges.
- A score of 9-10 indicates your IAM program is performing well and ahead of the curve.
Conclusion
Identity and Access Management solution is indispensable in contemporary cybersecurity efforts, serving as a vital defense against evolving threats and stringent compliance requirements. Organizations should adhere to an 8-point Identity and access management audit checklist to fortify their IAM security postures and craft a comprehensive IAM strategy. This checklist encompasses crucial steps such as policy creation, streamlined procedures, privilege assignment, and access reviews, all aimed at maintaining robust security and regulatory compliance.
With a perfect IAM strategy, you can fight identity and related risks such as identity vulnerabilities and sprawls, challenges with unused/legacy systems, and vendor lock-in. Looking for IAM Solutions and Services support?
Veritis, an organization acclaimed for its excellence in the industry, boasting accolades like the Stevie and Globee Business Awards, offers specialized IAM services. With Veritis as a trusted partner, organizations can enhance their IAM systems, ensuring robust security and seamless compliance with regulatory standards. By harnessing Veritis’ expertise, businesses can navigate the complex landscape of IAM effectively, safeguarding their valuable assets and data in an ever-evolving digital world.
Looking for Support? Schedule A Call
[WPSM_AC id=13723]
Additional Resources:
- 5 Reasons Why Financial Sector Needs Identity and Access Management (IAM)
- Top Tools and Security Protocols That Make IAM Successful!
- Robust Identity Management With ‘8-Point IAM Audit Checklist’ and ‘IAM Strategy’
- Regulatory Compliance Made ‘Easier’ With IAM Solutions
- Identity and Access Management (IAM) Market Forecast: USD 25 Billion by 2026