Why are Identity and Access Management Essential in Healthcare?
Globally, there has been an increasing focus on the healthcare sector, with regulatory laws being enforced stronger than before. In the wake of data breaches and increased security threats, Identity and Access Management (IAM) has arrived as a significant game-changer for establishing security, data protection, and automating processes.
Hence, employee training is an essential aspect of healthcare administration; it is mandatory to train staff members in relevant tools and help them become efficient in managing patient data and sensitive information.
Healthcare Identity and Access Management (IAM) has emerged as a great way to ensure data security is not jeopardized during daily operations. Hospital authorities have adapted IAM to ensure controlled and secure access to patient records, administrative information, medical reports, and various files.
Five steps to establish Healthcare Identity and Access Management (IAM)
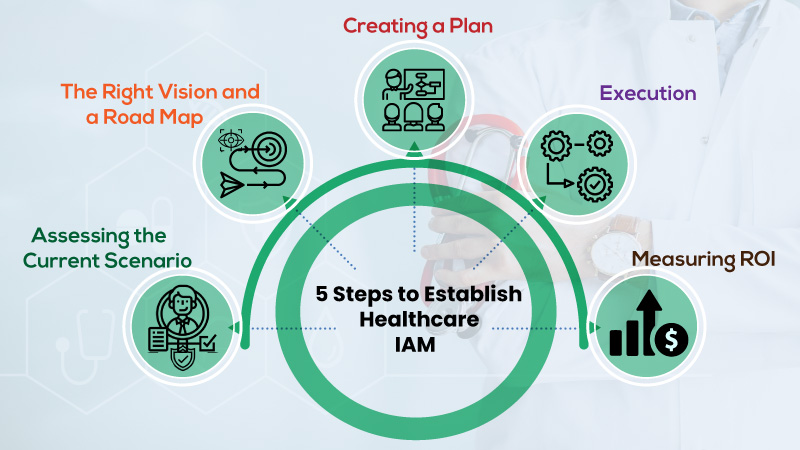
While IAM has numerous facets across various healthcare processes, a healthcare organization needs to create an initial strategy via planning, operational function, and implementation method.
By envisioning a roadmap for enhancing the IAM methodology, organizations can ensure lower cybersecurity breaches, minimal maintenance, and smooth functioning of the program.
First, IAM should be implemented in small phases rather than aiming to launch a full-fledged plan overnight. IAM is a continually evolving journey – to initiate this process, here are five steps we bring forward:
Step 1: Assessing the current scenario
The first step should be to assess and analyze the current data, system, procedures, people, process flows, applications, and roles. It will help create a clear picture and determine where your organization stands concerning IAM.
The next step would be to focus on different aspects of IAM, i.e., federation, Multi-Factor Authentication (MFA), Single Sign-On (SSO), and delegated administration, and understand where does the organization stand at and which aspect should be given priority.
Another critical move would be to increase organizational Identity Lifecycle Management (ILM) maturity, primarily about automating identity processes across the organization – creating and managing user identities, removing identities, and ending user access. Since most healthcare organizations falter at providing third-party vendors and contractors access via firewalls.
Step 2: The right vision and a road map
After identifying and analyzing the various systems and processes, the next step would be to build a strategy for implementation and put in milestones for measuring the plan’s effectiveness.
It is essential to build touchpoints with the team, connect with the key stakeholders, and measure progress via KPIs and relevant data.
ALSO READ: Identity and Access Management Best Practices for Enterprises
Step 3: Creating a plan
This stage involves taking an inventory of all the resources available, business impact, financial plans, and technologies. This step involves fleshing out the roadmap, incorporating timeline and milestones, and carving out the scope for adjustments if required.
It is also an excellent phase to understand how much investment would be required for implementation and different priorities to be taken into consideration.
Step 4: Execution
This stage involves the execution of various phases for the IAM program and understanding the integration across the new system or technology ties with other systems. Before IAM implementation, specific steps need to be taken or could pose to be challenging in the future.
Hence, execution and measuring the ROI and understanding the full impact are essential for ensuring the IAM program’s efficiency.
Step 5: Measuring ROI
This step is crucial to understand if the level of the IAM maturity level planned for this phase of the program is achieved or not. An assessment would involve addressing any issue, stepping back to check the implementation and make adjustments accordingly.
On accomplishing the vision, the next step would be to identify the next level of IAM maturity and pool in the required resources to complete it.
Veritis IT Managed Service Provider: PowerPoint PPT
How, at Veritis, do we help you
Through Veritis’ IAM approach, achieve your organizational goal towards digital transformation, enable secure access for end-users and enhance your identity management program.
Also Read:

