
Continuous technological evolution is presenting severe challenges to organizations across the world. With intelligent solutions on one side, technological advancements also indirectly provide room for cybersecurity threats.
These threats are fast-emerging and growing wise. So, you cannot rely on traditional solutions to manage and safeguard your organizational data and assets from these risks.
Moreover, the rate of cyberattacks is rising yearly, causing trillions of dollars in financial losses to organizations. This is where you would require the Identity and Access Management solutions and services.
Here in this blog, we will look into different IAM Tools by use-cases, how these tools help your business, and the protocols that decide the success factor:
Different Identity and Access Management (IAM) Tools, By Use-Cases
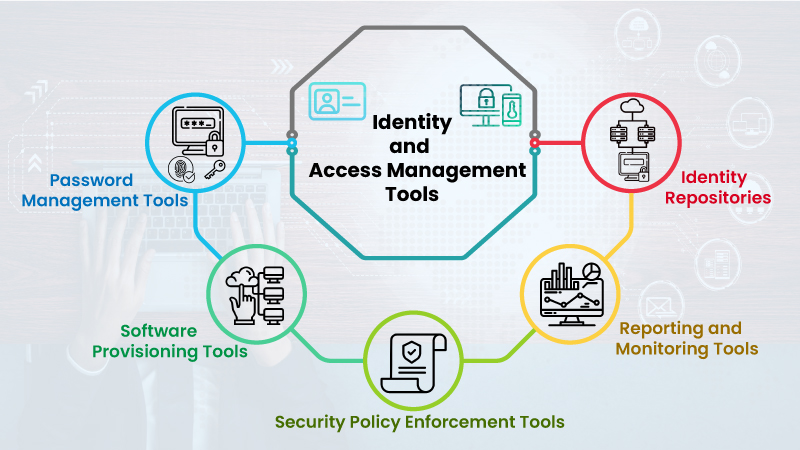
There is a wide range of IAM tools for different business use cases:
1) Password Management Tools – These tools help manage all passwords easily without memorizing them every time.
2) Software Provisioning Tools – These tools help manage user information across systems and applications.
3) Security Policy Enforcement Tools – These tools ensure timely detection of improper behavior, trace real-time access, and effectively enforce business policies.
4) Reporting and Monitoring Tools – These tools monitor accounts vulnerable to risks and apps with granted permissions.
5) Identity Repositories – This is where all the information about users and groups is stored.
Schedule a Consultation Session With Our IAM Expert
How Identity Access Management (IAM) Tools Help Your Business?

IAM Tools support your business majorly in the following areas:
1) Enhanced Security
Compromised user credentials are the first entry points for any intruder attack. IAM Tools ensure your credentials and networks are secured under different security layers.
2) Business Productivity
Managing and controlling access in a large enterprise is tedious and will eventually hit productivity. IAM tools help you in access management and control, saving related costs.
3) Employee Productivity
A fully IAM system alleviates the maintenance burden on your IT teams. IAM tools help your teams efficiently manage identities and access across various networks distributed across locations. Thus, employee productivity is a significant advantage. Centralized control in the IAM system naturally reduces the number of reports to core security teams.
4) Improved Collaboration
IAM tools contribute to the collaboration among internal and external teams. These include employees, partners, suppliers, and contractors, among others, with the help of modern applications in a more secure way.
5) Centralized Control
IAM tools facilitate centralized control for storage, access, and control of your data and assets. This reduces the threat from internal and external factors. Options like Single sign-on allows single-time authentication for access across multiple platforms.
Beyond Tools, Security Protocols Matter!

While tools can help you get the desired output, the effective implementation of IAM requires adhering to three major Security Protocols:
- Multi-factor Authentication System involves multiple authentication methods from different credential categories to verify user identity or authenticate a transaction.
- Identity Management Assessment is crucial to protect critical identities through an access control mechanism. It’s crucial to monitor who gains access to your organizational data.
- Implementation and Integration demand advanced integrations like machine intelligence, AI, biometrics, and risk-based assessment across all platforms and devices to remain safe from external and internal threats.
Effective IAM implementation of all these processes requires subject-matter expertise and a deep understanding of real-time scenarios. Looking for Support?
Also Read:
- Identity and Access Management Best Practices
- What to Expect: Trends in Identity and Access Management
- 5 Reasons Why Financial Sector Needs IAM
- Healthcare IAM Solutions: Five Steps to Transformation
- Top Tools and Security Protocols That Make IAM Successful!
- ‘8-Point IAM Audit Checklist’ and ‘IAM Strategy’
- Regulatory Compliance Made ‘Easier’ With IAM Solutions