IAM, or identity and access management, is a framework of corporate procedures, laws, and technological advancements that makes managing digital or electronic identities easier.
Building a solid information security program requires using the many protective features provided by identity management solutions. Although the phrases identity management solutions, authentication, and access management are sometimes used interchangeably, each function as a separate level in the service access management realm.
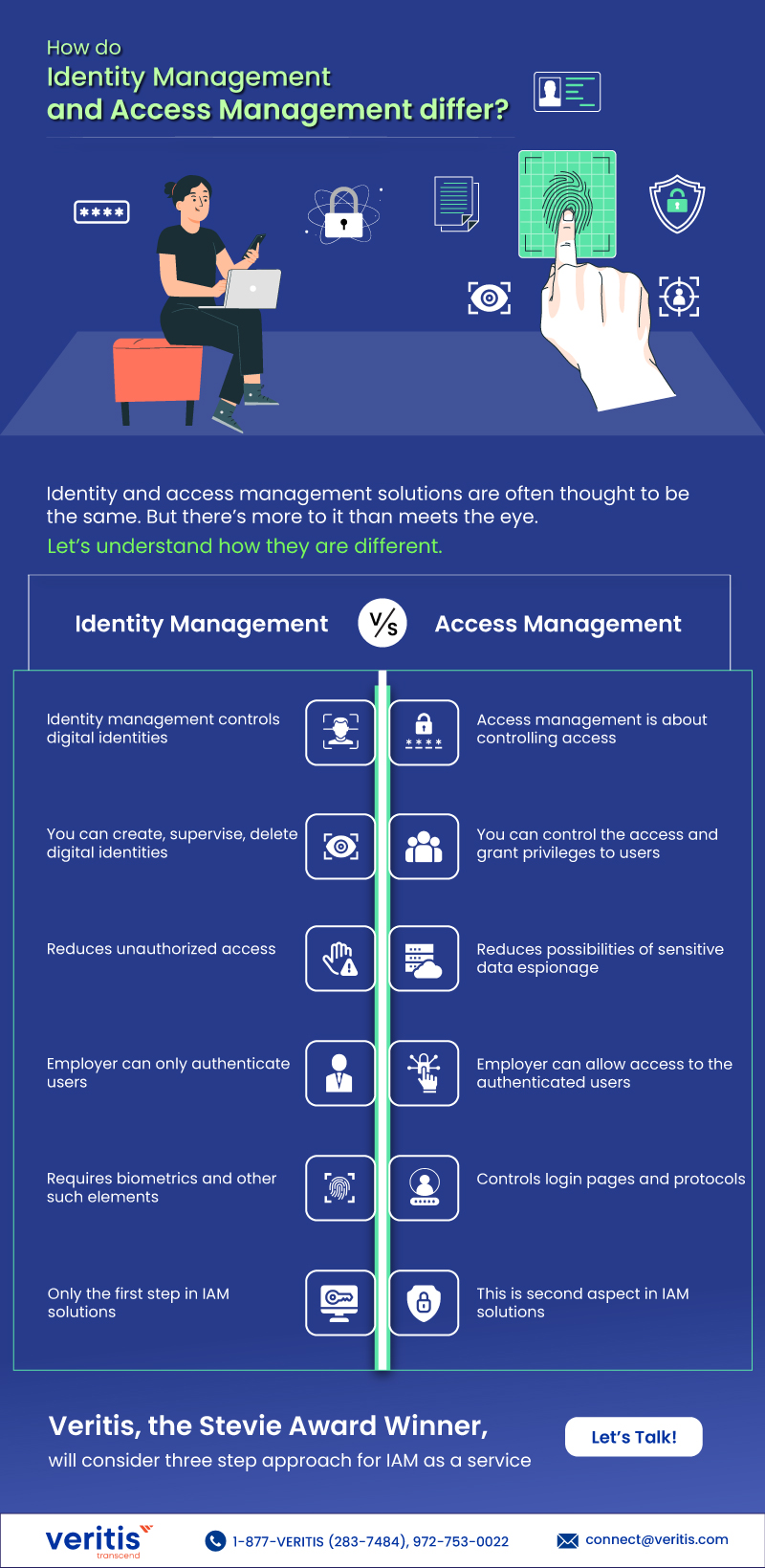
Identity and access management solutions are often thought to be the same. But there more to it than meets the eye. Let’s understand how Identity Management vs. Access Management Differ.
How do Identity Management and Access Management Differ?
Email-us: connect@veritis.com; Call: 972-753-0022
Identity Management Vs. Access Management
| Identity Management | Access Management |
| Identity management controls digital identities | Access management is about controlling access |
| You can create, supervise, delete digital identities | You can control the access and grant privileges to users |
| Reduces unauthorized access | Reduces possibilities of sensitive data espionage |
| Employer can only authenticate users | Employer can allow access to the authenticated users |
| Requires biometrics and other such elements | Controls login pages and protocols |
| Only the first step in IAM solutions | This is second aspect in IAM solutions |
You should never neglect security as a factor, and IAM policies must be set up. Stevie Award winner Veritis is the go-to partner for most businesses because of its IT solutions and cyber security expertise. We have provided tailored solutions to organizations, whether they are Fortune 500 firms or new businesses, and ensured our IAM solutions don’t reduce productivity. So get in touch with us, and we’ll incorporate reliable security solutions into your system.
Additional Resources:

