
The ability to dole out applications at the pace of business has become essential in today’s digital world. Thankfully, DevOps has made this possible by bringing together business, Dev and Ops teams and applying automated processes to streamline the application development lifecycle.
However, secure application development has become a challenge for enterprises as DevOps and security processes are often disjointed. While organizations are wading through DevOps for a more rigorous application development, security is often ignored.
Moreover, the task of ensuring application security often resides with the security team, and most issues are identified only during the testing phase. This approach can’t keep up with the releases without halting development process. The lag would spawn time-to-market delays, developer underutilization, and vulnerability backlog.
Cognizant of this DevOps-security conundrum, many forward-thinking companies are turning to DevSecOps methodologies that help integrate security into the application development lifecycle.
Also Read: 14 Statistics That Shed Light Upon DevSecOps’ Opportunities and Challenges!
DevSecOps – Fine-tuning Application Security

DevSecOps enables organizations to build a continuous application security process that fuses effectively with DevOps processes. Security would be strategically deployed at every step of the software development lifecycle (SDLC).
DevSecOps methodologies empower enterprises with ‘shift-left’ practices to incorporate security measures early into the SDLC. This helps detect app security defects early in the SDLC, thereby enabling DevOps teams to fix software vulnerabilities swiftly and effectively.
Also Read: What are the best DevSecOps practices for security and balance agility?
Let’s delve into the details on how to weave security into the application development lifecycle:
Boosting Continuous Application Security with DevSecOps
Organizations must incorporate security throughout the application development lifecycle, during development, test, and production. However, the security integration must be seamless enough to avoid undesired friction in DevOps workflow and continuous integration/continuous deployment (CI/CD) processes.
There are a multitude of ways for continuous application security integration. Here’re six key considerations for effectively integrating automated security testing across the development lifecycle:
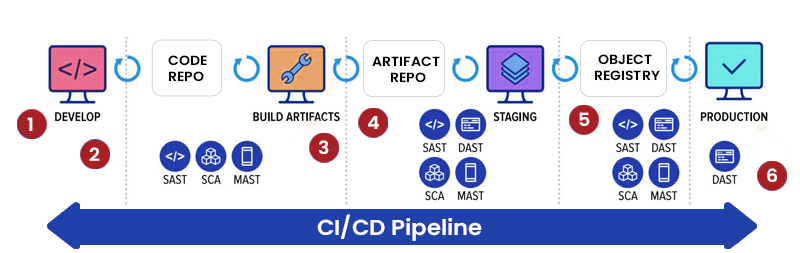
- Design Review: Rope in security when business objectives are being drafted along with backlogs and sprints.
- Code Review: Empower development as well as operations teams on security aspects. Hammer out a secure coding checklist/template to help developers identify common and recurring issues.
- Pre-commit or Pull Requests: Implement Static Application Security Testing (SAST) and Software Composition Analysis (SCA) during the pre-commit or pull requests. This will help discover code issues.
- QA Integration: Implement SAST and SCA processes along with Dynamic Application Security Testing (DAST) during the QA stage. This enables the DevOps team to identify high-certainty and high-severity vulnerabilities.
- Production Acceptance: Deploy DAST at this stage to discover potential production vulnerabilities. There will also be the need for SAST and SCA during this stage.
- Production: Continue the testing process with production-safe DAST even upon release. Production-safe DAST empowers DevOps teams to identify production vulnerabilities without impeding application performance. Moreover, protective technologies such as a web application firewall (WAF) and runtime application self-protection (RASP) must be implemented to secure running applications.
Integrating SAST into the application development lifecycle helps organizations realize potential benefits. According to a WhiteHat survey, enterprises realized a 25 percent reduction in time-to-fix after implementing SAST.
Also Read: DevSecOps – A DevOps Savior to ‘Cybersecurity’ Challenge!
When SAST is integrated along with DAST, organizations witnessed a 50 percent downtick in new production vulnerabilities, compared to implementing DAST alone. To achieve a cost-effective application security program, it is wise to implement all of the above-stated six integration points via automation.
While it’s possible to build DevSecOps capabilities from scratch, a faster and cost-effective approach is to join hands with a third-party DevSecOps service provider like Veritis. Partnering with Veritis helps you establish a holistic security approach by roping in innovations and technology trends.
Veritis DevSecOps framework enables shared responsibility among the development, operations, and security teams. Our DevSecOps strategy integrates security processes and tools that drive visibility, collaboration, automation, and agility into each phase of the DevOps pipeline.
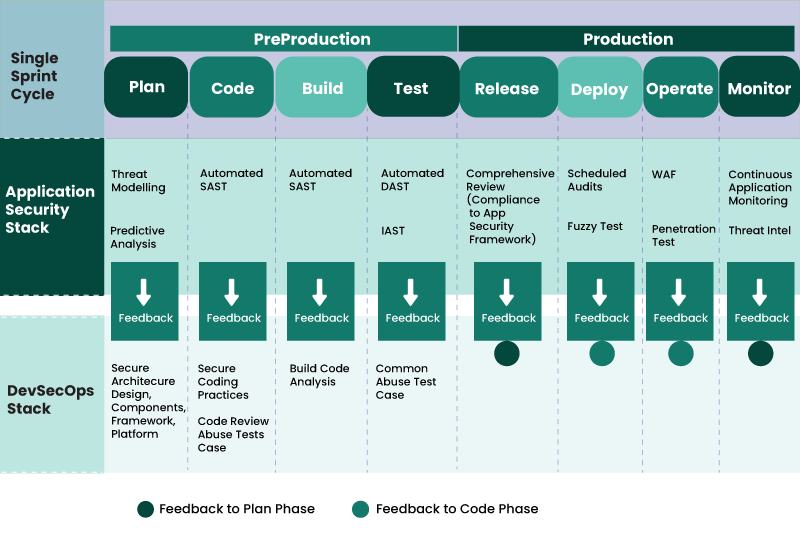
Let’s join forces to build, deploy, and iterate applications securely, everywhere.
More Articles:
