
Tools and resources have a crucial role in any process. They are very important for the successful execution of any environment, especially in IT.
While DevOps has gained popularity over the years as a technology solution, it’s the DevOps tools and resources that are behind the DevOps success!
Many organizations have realized this fact and are already using the DevOps toolchains for automated development, deployment, delivery and management of software applications, resulting in efficient product delivery.
While, some other organizations continue to face constraints due to the very collaborative nature of these tools and resources, which is more likely to cause security issues.
So, addressing this security risk and securing these tools and resources is now the challenge before for such firms.
Here are 5 measures you can prioritize to safeguard DevOps tools and resources:
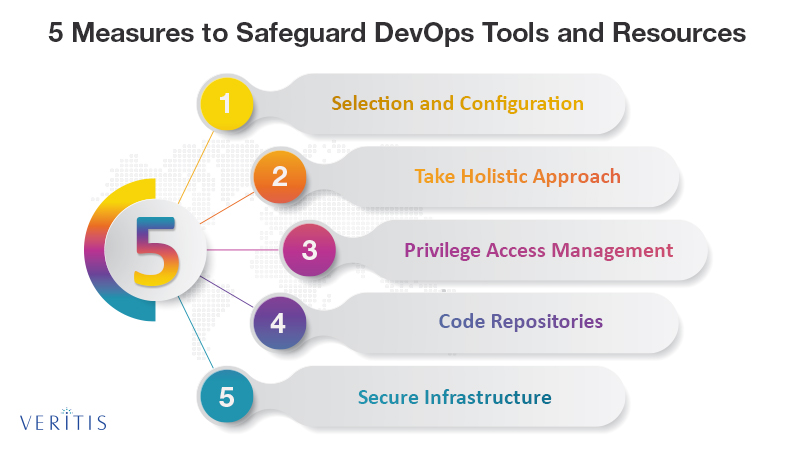
1) Selection and Configuration
This is a very crucial step in securing DevOps toolchain. This should ideally involve gathering detailed information about inventory used by teams. Then comes the evaluation process, where teams will need to identify the defective ones and take necessary measures to address them.
This typically involves checking default configurations and keeping them updated. Security teams will have to work with teams that finalize on the tools and resources and make sure they meet enterprise security policies.
2) Take a Holistic Approach
It’s important to take a holistic approach to security DevOps tools, as vulnerability at a single point can spread across the chain of tools and resources. First and foremost, ensure to have your sensitive information like credentials associated with DevOps and cloud management tools encrypted with tight authentication procedures.
Next comes the ‘access privilege’ to users such as ‘just in time’ access to users, access to high-risk commands and high-level access even to internal teams restricted for their respective tasks.
This whole process should be backed by a monitoring mechanism. Above all, it’s important to have in place a strong cybersecurity best practices, which might implementation of access controls that categorize DevOps pipelines. This prevents intruders from taking control of the rest through a single route.
3) Privilege Access Management
Least privilege access is one important factor for securing DevOps. Implementing that limits the user access to critical DevOps functions and tools, making them available only for specified tasks. But this should always be backed by strong authentication methods such as second person review before any approval, among others.
Moreover, tools like Jenkins often retain permissions to perform all duties without any restriction. Dealing with tools requires the separation of duties as a safety measure. By separating duties, you create multiple nodes, with each possessing a unique identity and limited privileges.
4) Code Repositories
Building secure code repositories for developers to place their code is another important measure that IT organizations should implement. It’s the security teams who should ideally pitch for risk-based policies that secure such repositories.
Next, every code that goes from an organization might often contain information about the organization’s internal network. To ensure the safety of such instances, its preferable to use on-premise systems instead of cloud-based code repository. Then, it’s important to make sure these on-premise code repositories don’t have access to outsiders. If using cloud-based repositories, it’s recommendable to keep them private.
Above everything, it should be a default that every code is automatically scanned for critical information about the organization on every release.
5) Secure Infrastructure
For all the aforementioned measures to work out well, it’s important to ensure the IT infrastructure and its assets are in a safe and secure state. Risks can arrive out of spam emails, outdated workstations and server patches, irregular vulnerability scans and lack of monitoring mechanism, among others.
Besides hardware, the cloud environment may also serious security risks. Monitor your cloud infrastructure for critical information and configuration issues. Also, make sure, VMs and container images used in development and production phases are from approved sources and are up-to-date.
Automate VM and container configurations to ensure security remains with secured configurations and access controls, even when a new container comes into play.
In Conclusion
These five measures are critical to securing your DevOps tools and resources. They not only secure your tools but also contribute to the success of overall DevOps implementation.
Related Stories