
Over the last few years, DevOps has been empowering IT organizations with a highly collaborative environment and high-speed product delivery.
That agility and ability to ensure short-release cycles made DevOps the favorite technology solution for many IT firms.
Many companies are already enjoying this increased collaborative approach of DevOps in their digital transformation journey.
A few are in the process of making it, and a few others have yet to realize the DevOps potential.
However, all in common have a single concern: ‘how does DevOps deal with security?’ and ‘Is Secure DevOps possible?’.
Let’s deal with these questions: First by understanding ‘Security Challenges in DevOps?’ and Next by ‘Identifying DevOps Security Best Practices’
The Problem: Why Security is a Challenge in DevOps?

Security in DevOps refers to safeguarding the DevOps environment by implementing relevant strategies, policies, processes, tools, and resources.
1) Where is the Problem?
A DevOps model typically includes cross-team collaboration and incorporates different functions, specifications, and models for coding, testing, integration, deployment, infrastructure management, and more.
Moreover, continuous automation and monitoring will be performed across the process chain.
All these mean fast-moving development cycles, release timeframes, and shortened feedback loops.
There is enough scope to say this fast-paced environment can often create gaps between DevOps and Security teams.
DevOps teams’ short timeframes may often outpace the speed of security teams, which will need to check configurations, perform code analysis, and assess vulnerabilities, among other tasks.
These inconsistencies, caused by improper security checks, may result in insecure code, misconfigurations, hardcoded issues, and other issues that can slow down the DevOps cycle as a whole.
2) Cultural resistance
Cultural resistance is often seen as a primary obstacle to addressing security concerns in DevOps, supported by the argument that a special security check will derail the development process. But the fact is that addressing security in the early phases takes less time than doing so at the last.
3) Cloud and Open Source environments
DevOps teams usually rely on cloud deployments and access open-source resources to manage security and server instances. This fast-paced environment may often compromise critical information, cause configuration errors, cause compliance issues, and cause security breaches.
4) Container and other tools
Containerization and container tools have a special role in boosting productivity in a DevOps environment. However, they can often cause security concerns in the process.
Container apps enjoy the flexibility of running on any computing platform or cloud without dependencies, which is their portability advantage. However, this can also be a security challenge in the absence of proper controls, as containers share OS among themselves and are less often scanned for vulnerabilities.
A global survey found more than 90% of organizations citing containers as ‘security threat’. Container Security is key to ‘DevOps Security’!
5) Access Management
DevOps is a highly collaborative, dynamic, and interconnected culture. Teams communicate by exchanging critical information, credentials, SSH Keys, APIs, and tokens. As part of workflows, these critical assets will be required to pass across open source platforms, apps, containers, and cloud instances, among other things.
Considering that these platforms are vulnerable to security attacks, assets passing through them also stand vulnerable to threats. This gives intruders full control of systems and data, resulting in a serious security challenge.
We have seen that security is a serious concern in a DevOps environment. Now, let’s examine the solution to address the concern.
The Solution: DevOps Security Best Practices
The above-discussed factors pose major security risks to a DevOps environment. However, considering their benefits, it’s imperative for organizations to incorporate them into their DevOps model.
So, what’s the solution?
Here are 9 DevOps Security Best Practices that can help you achieve security while balancing agility:
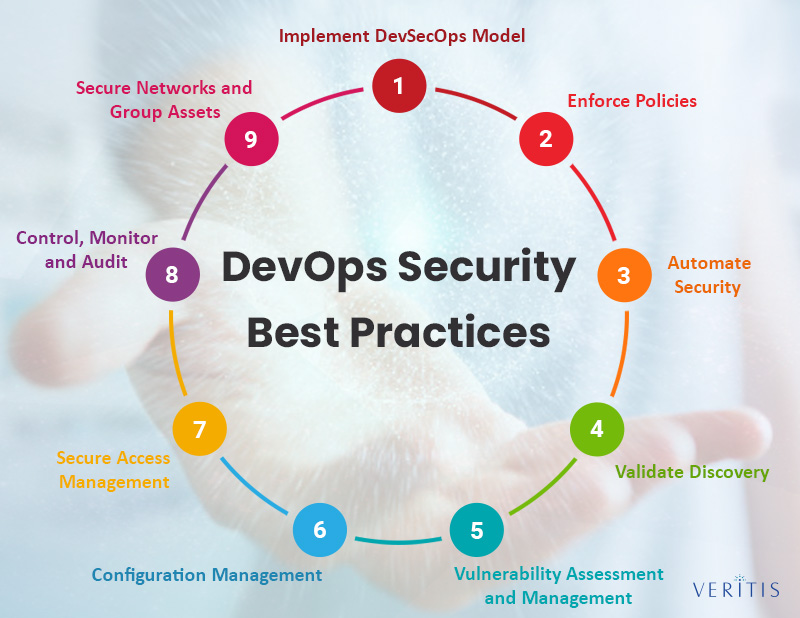
1) Implement DevSecOps Model
This is the first and foremost step to securing your DevOps environment. Successful DevOps security demands security integration across the product development lifecycle (design, development, delivery, operations, and support stages).
The DevSecOps model includes governance and cybersecurity measures such as code review, Identity Access Management, firewalls, configuration, and vulnerability management. With DevSecOps in place, you have ‘secure DevOps’ that will no longer create threats and additional costs and, moreover, give you seamless delivery.
2) Enforce Policies
Communication and strict policy enforcement are key to achieving the goal of secure DevOps. Implement transparent cybersecurity policies that are easily understandable and implementable for the teams. This will help them plan their tasks in line with the set security requirements.
3) Automate Security
While you bring in security tools and resources, automating them to scale security features to your DevOps process is important. Automation also minimizes the risk of errors caused by repeating instances and the associated downtime issues.
That will also help you identify potential threats, vulnerable code, and any issues within processes or infrastructure. Automation breaks cultural resistance and facilitates deeper penetration of security practices into the DevOps process chain.
4) Validate Discovery
While you identify and map issues, it’s equally important to continuously validate all the approved tools, devices, and accounts spotted during discovery. Ensure that they are brought under security management built in line with your internal policies.
5) Vulnerability Assessment and Management
Ensure a strict vulnerability analysis, assessment, and management before the product reaches production. Ensure to have vulnerability scans well in advance and along the development and integration phases. Penetration testing and related attack methods can help you in the process.
DevOps security runs tests and tools against the production environment and infrastructure to address patching-related issues as products enter the operating environment.
6) Configuration Management
Configuration issues are one serious concern that can affect your DevOps workflow. Maintain continuous configuration scans across servers and individual builds for all cloud assets and ensure misconfigurations are addressed by industry best practices.
7) Secure Access Management
Eliminate all credentials embedded in code, files, service accounts, and cloud platforms. Thus, you are keeping the credentials (not required for a specific process) safe at a centralized location.
Don’t worry; they can be accessed through privileged password management solutions that call applications and scripts to access passwords if required. Implementing such API calls gives you additional control over code, scripts, and embedded keys. Automate this process to use passwords in line with the policy demands.
8) Control, Monitor and Audit
Less privileged access rights, fewer potential attacks. It’s recommended to secure privileged account details, eliminate administrator privileges on the end-user side, and have a simple workflow that doesn’t demand privileged access.
On the other hand, continuously monitor the privileged sessions to ensure they are legitimate and adhere to compliance requirements. Even the least privileged model should restrict access to certain development and production systems while giving internal teams appropriate permissions only to build, deploy, configure, and address production issues related to images they created.
Use privileged access management tools and resources to monitor and audit privileged access and credential management.
9) Secure Networks and Group Assets
Categorize networks and combine assets such as applications and resource servers to limit the ‘line of sight’ for intruders. Make them into individual groups that work as logical units.
Trigger a ‘secure jump server’ with multi-factor authentication and other authorization features to tackle access through a trusted zone. Further, segment access-based context by user, application, and data.
More such practices can be implemented per the changing requirements for a secure DevOps environment.
On an EndNote
Securing DevOps lays the path for a full-fledged DevOps implementation with embedded security practices. With security addressed, DevOps is undoubtedly an omnipotent and game-changing technology solution for fast-changing business needs.
Read Also: