Cloud Security Automation emerges as a critical imperative in the tech era of cloud computing, where data and applications are hosted remotely. As firms migrate their operations to the cloud, ensuring the safety of sensitive information and systems becomes paramount.
Cloud Security Automation, driven by advanced technologies and intelligent protocols, offers a proactive and efficient approach to protecting against many cyber threats in real-time. In this blog, we delve into the significance of Cloud Security Automation and explore how it empowers businesses to fortify their digital fortresses while maintaining agility and resilience in the cloud automation era.
Businesses across all industry verticals have leveraged the cloud’s efficiency, elasticity, and innovation. Yet, a recent survey revealed that only 35% of organizations have fully achieved their expected outcomes from the cloud, and 65% identified ‘security and compliance risks’ as a significant barrier.
Though the cloud offers new opportunities to transform, modernize, and innovate, security workflow automation remains the most significant hurdle to cloud adoption. Moreover, the complexity of hybrid and multi-cloud environments further complicates the journey to cloud automation.
While security workflow automation is often seen as the biggest hindrance to cloud adoption – in reality – it can be its most significant accelerator – when automated. Automating the cloud security infrastructure process enables organizations to gather the information they need to secure their cloud environments and redirect their efforts to innovation and growth.
In 2023, the global expenditure on public cloud services is projected to witness a significant uptick, with a growth rate of 20.7%, propelling it to a remarkable USD 591.8 billion, as forecasted by Gartner. However, this surge in cloud adoption has brought to light a critical concern, as reported by Pingsafe: a striking 80% of companies witnessed at least one cloud security infrastructure incident in the past year, underscoring the growing importance of robust security measures in the cloud environment.
In response to this challenge, 54% of organizations have turned to cloud security automation tools and services, as revealed by StrongDM, to fortify their cloud defenses. Cloud security automation has become increasingly pervasive, with configuration management emerging as the top use case at 75%, followed closely by vulnerability scanning at 70%, patch management at 65%, and identity and access management at 60%, according to Forrester’s research.
Log monitoring and analysis at 55% also play a significant role in securing cloud infrastructures. The benefits of cloud security automation, as highlighted by Accenture, are substantial, with 80% of users reporting an improved security posture. Additionally, cloud security automation is known to yield cost reductions (75%), enhanced operational efficiency (70%), reduced human errors (65%), and improved compliance (60%). These statistics underscore the growing significance of cloud security automation in the security of burgeoning cloud adoption and the increasing importance of securing cloud-based assets in the face of cyber threats.
Automating the security processes that are conventionally created and deployed manually brings a new evolution to cloud security operations automation. However, many enterprises struggle to implement the best cloud security automation.
What is Security Automation?
Security automation uses technology to streamline and enhance an organization’s security operations. It uses software and automated processes to handle tasks like threat detection, incident response, and vulnerability management. By automating routine security tasks, organizations can respond to threats more efficiently and reduce the risk of human error.
5 Steps for Successful Cloud Security Automation
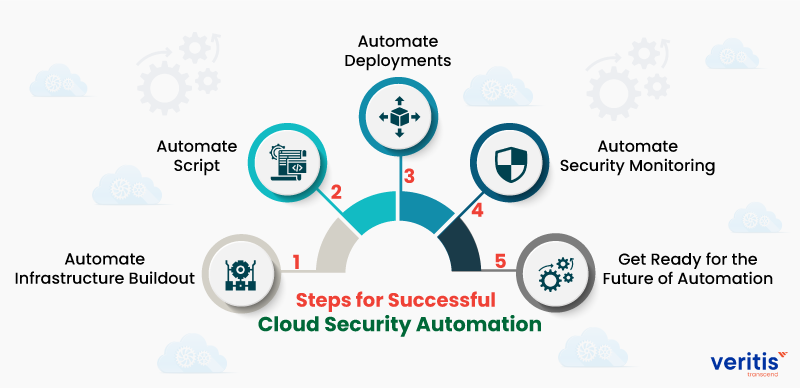
Here are five best practices for the successful implementation of cloud security automation:
1) Automate Infrastructure Buildout
By automating infrastructure buildout, engineers are relieved from manually configuring security groups, networks, user access, firewalls, DNS names, and log shipping, among others. This significantly reduces the scope for engineers to make security mistakes.
Moreover, automation in security team need not worry about the best practices every time they spin up a new instance, as they only have to touch the scripts, not the instances, to make the changes.
2) Automate Script
In traditional IT, a zero-day vulnerability or any other major security workflow automation issue requires an organization’s system engineers to work rigorously to patch every server manually. However, automating scripts requires only a single line change in the manifests to ensure the newly released version is running instead.
These automation script resources are declarative management tools that automatically configure instances, virtualized servers, or even bare metal servers.
Whenever a new instance is launched, these scripts get the instance ready for production, including the security configuration tasks like ensuring central authentication, installing intrusion detection agents, and enabling multi-factor authentication.
3) Automate Deployments
Though automating deployments is one of the best practices in DevOps implementation, it can also improve an organization’s security posture. In a zero-day vulnerability, deployment automation ensures that changes made to the DevOps tool script get automatically deployed across every instance or server. This makes it possible for a single system engineer to respond to threats quickly.
4) Automate Security Monitoring
In the growing trend of hybrid and multi-cloud environments that support individual applications, monitoring the entire infrastructure in a single interface is imperative. During automating security attacks and downtime, it can be resource-draining and time-consuming to identify and fix the problem.
Automated security monitoring aids engineers with the proper intelligence to address threats and secure critical assets.
5) Get Ready for the Future of Automation
Data balloons and hybrid environments will become mainstream within the next few years, making the manual security approach incompetent. Hence, now is the best time to develop or outsource an internal automation team. Although achieving end-to-end process automation across hybrid environments may take months or even years, it will prove infinitely more valuable than training employees to reduce human error.
Useful Link: AIOPS Solutions: Enhancing DevOps with Intelligent Automation for Optimized IT Operations
5 Stages of Cloud Security Automation Framework
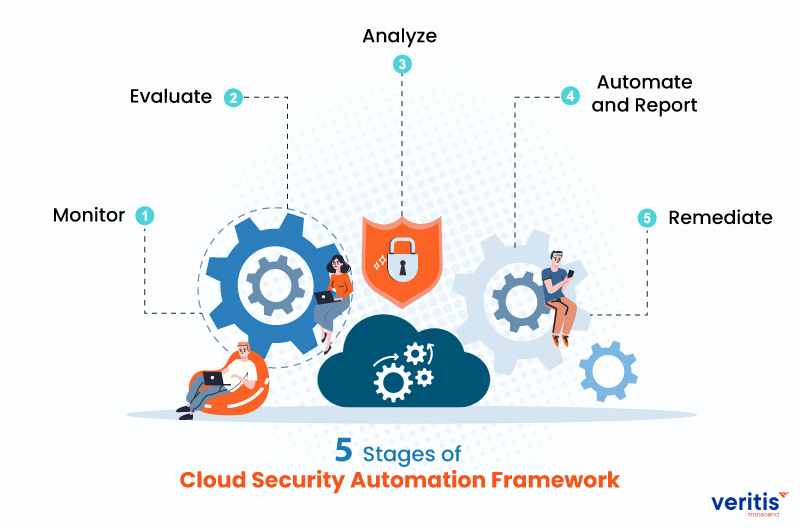
Automation of cloud security involves a 5-step strategy as follows:
1) Monitor
Your cloud capacity will always scale to meet all the operational needs. So, monitoring the workflow of all the tasks in your cloud security operations automation is imperative. This enables you to understand how each workflow is carried out.
2) Evaluate
In automating cloud security infrastructure, knowing and prioritizing the tasks to automate is the first critical step. Closely monitoring the workflows helps to evaluate tasks that should be automated, like repeated tasks, automated cloud deployments, resource provisioning, and creating automation security rules.
3) Analyze
Do an in-depth analysis of the collected information based on low, medium, or high-risk severity. Then, automate low-risk processes first, followed by medium and high. The in-depth analysis also helps you do controlled automation and study the impact on infrastructure.
4) Automate and Report
The resulting analysis can now be pushed to integrated systems to automate the workflows. Then, configure the automation processes to generate the reports that give the overview of the changes before or after.
5) Remediate
By now, you will get a clear picture of cloud automation, irrespective of whether you started automating simple or complex workflows. This enables you to implement remediation and enhance the overall automation security posture.
Useful Link: What is Security as a Service (SECaaS)?
Benefits of Cloud Security Automation
Apart from the reduction of manual security tasks, let’s explore how cloud security benefits can further enhance and propel your best cloud security strategy services:
1) Accuracy
The primary origin of misconfigurations often stems from human errors. Implementing a consistent hardening process that maintains uniform configurations across development, quality assurance, and production settings not only simplifies the deployment of secure environments but also significantly reduces the likelihood of guesswork or human mistakes.
2) Speed
The rapid pace of infrastructure provisioning and the automated cloud deployment of cloud native applications can pose challenges. Often, the availability of resources within engineering and automating security teams becomes a bottleneck for ensuring automating security. This can lead to the automation of security tasks, causing delays or deferring subsequent releases. Automation comes to the rescue by enabling enterprises to automate configurations and manual processes. It also facilitates the integration of scans and testing right from the initial stages of development through automated cloud deployment.
3) Enhanced Security
Security automation is vital in safeguarding infrastructure and applications by identifying and promptly responding to threats, diminishing reliance on human intervention for monitoring and addressing vulnerabilities.
4) Compliance
Streamlining the automation of checks and reports empowers you to demonstrate compliance without hindering the development process or consuming significant engineering resources. This approach ensures compliance verification becomes an efficient and integrated part of the development lifecycle, allowing teams to concentrate on their core tasks and innovation rather than being bogged down by compliance-related bottlenecks.
5) Scalability
When a process is automated, it gains the capability to operate autonomously in various locations and at any time, requiring minimal additional intervention. This enhanced level of flexibility and independence in automated processes can significantly contribute to efficiency and reduce the dependency on manual oversight, making operations more agile and responsive to dynamic demands.
A continuous, automated security protects your enterprise’s critical cloud automation assets from evolving threats, as well as helps your business reap the following more benefits:
- Consistency in security operations automation
- Reduced manual errors
- Advanced security measures
- Robust security posture
- Rapidly identify and address security gaps
Conclusion
The automation of cloud security undeniably presents a multitude of valuable business benefits. Nevertheless, it’s essential to acknowledge that it can be a more complex and costly endeavor when compared to non-automated security measures. The technology requirements have a price tag and entail a significant implementation timeframe. Furthermore, the effective setup and maintenance of security automation demand high expertise.
Considering these challenges, whether you’re transitioning to the cloud or already operating within it, partnering with a trusted Cloud solutions provider like Veritis is a strategic move to fortify your cloud-based systems with cutting-edge security. Veritis, a distinguished recipient of accolades such as the Stevie and Globee Business Awards, offers a wide range of services to enhance organizations’ security, efficiency, and agility in an ever-evolving market landscape. With Veritis as your cloud consulting services provider, you can be assured of highly effective and reliable cloud computing solutions that empower your business to thrive in the cloud era.
Looking for Support? Schedule A Call
Read More Cloud Stories:
- What is Cloud Infrastructure Automation?
- AWS vs Azure vs GCP: Breakdown of Cloud Migration Services
- 5 Reasons for successful On-Premises to the Cloud Migration
- Things CTO Needs to Consider Selecting a Cloud Network Security Solution
- Cloud Cost Optimization and Management
- 9 Data Security Best Practices for Your Business