
Table of contents
- What is the IAM strategy?
- Key Components of an Effective IAM Strategy
- Why Audit and Report IAM?
- Metrics to Measure IAM Effectiveness
- What Tools Are Required for IAM Audit and Reporting?
- What to Consider Before Implementing IAM Strategy?
- How to Create an IAM Strategy?
- 8 Point IAM Audit Checklist
- Common IAM Pitfalls to Avoid
- IAM Trends and Future Directions
- Conclusion
Meeting compliance and regulatory requirements is a major challenge for organizations worldwide. Given today’s cybersecurity challenges, organizations are constantly under the pressure of penalties for failing to meet compliance requirements. Every business must secure its assets and data against cyberattacks.
A robust Identity and Access Management (IAM) system provides your organization’s first line of defense by ensuring IT security and data protection. For that to deliver results, you need a checklist.
Identity and Access Management is a fundamental security framework that enables authentic users to access the appropriate resources when needed. An effective IAM solutions configuration mitigates the likelihood of data breaches and significantly raises the barriers for cyber adversaries. As such, IAM assumes a pivotal role as an indispensable cybersecurity tool for contemporary enterprises.
The Importance of Identity Management in Cybersecurity
Cyber threats advance daily, making identity and access management (IAM) a non negotiable pillar of cybersecurity. As a top executive, you cannot afford to overlook IAM. A weak IAM strategy exposes your business to security threats, compliance penalties, and diminished customer confidence. Identity management strategies define how companies safeguard sensitive data, ensuring only the right people access critical systems.
IAM in Cloud and Hybrid Environments
Cloud and hybrid environments demand a robust IAM strategy to prevent unauthorized access across multiple platforms. Traditional security approaches fail to address dynamic, distributed cloud infrastructures. Businesses must deploy identity management strategies that provide centralized authentication and adaptive access controls.
IAM assessment plays a critical role in securing cloud and hybrid ecosystems. Organizations must evaluate cloud specific access risks and enforce granular permissions through identity and access management testing. Without these assessments, enterprises risk misconfigurations that expose sensitive assets to cyber threats.
IAM risk management ensures compliance across cloud and on premise resources. A hybrid IAM approach integrates identity federation, single sign on (SSO), and real time monitoring to reduce breach risk while maintaining a seamless user experience. Executives must prioritize identity management strategies that align with evolving cloud security requirements.
Regulatory Compliance and IAM
Regulatory compliance goes beyond avoiding fines—it involves securing trust and business continuity. A robust IAM strategy ensures compliance with GDPR, CCPA, HIPAA, and SOX, while a thorough IAM assessment identifies security gaps before auditors do. Organizations risk audit failures, financial penalties, and reputational damage without testing their identity and access management.
A proactive IAM risk management approach enforces strict access controls, reducing insider threats. Regular IAM assessments and identity management strategies help organizations meet compliance mandates while fortifying security. Integrating identity and access management testing into compliance frameworks ensures resilience, legal protection, and operational efficiency.
Ensure compliance without compromise. Build a secure, future ready IAM strategy today.
What is the IAM strategy?
IAM strategies encompass a comprehensive framework of policies, procedures, and technologies for managing digital identities and governing resource access.
The attainment of network, system, and data security hinges on the meticulous governance of resource access, determining which individuals are granted access to specific resources under specified circumstances. This control can manifest as a primary password or PIN mechanism or as a robust multifactor authentication solution that may include biometric authentication for enhanced security.
Key Components of an Effective IAM Strategy
1) IAM Assessment for Risk Identification
A proactive IAM assessment uncovers security gaps before attackers exploit them. Assessments evaluate user roles, access privileges, and security loopholes. Conducting periodic identity and access management testing ensures that security protocols remain effective.
2) Identity and Access Management Testing to Prevent Breaches
IAM solutions must be continuously stress tested. Organizations that skip identity and access management testing leave themselves vulnerable to insider threats and unauthorized access. Continuous IAM assessment identifies weak authentication methods, enabling swift security enhancements.
3) IAM Risk Management for Regulatory Compliance
Industries handling sensitive data, such as finance, healthcare, and government, must enforce strict IAM risk management protocols. Non compliance with regulations such as GDPR, CCPA, and HIPAA can result in hefty penalties. IAM controls help organizations align with legal frameworks, mitigate security risks, and ensure seamless operations.
Why Audit and Report IAM?
The process of auditing and reporting on IAM (Identity and Access Management) serves several crucial purposes:
- It aids IT professionals in enhancing both IAM security and compliance measures.
- It contributes to the improvement of overall efficiency and performance within an organization.
- It enhances visibility and accountability across the IAM strategy
- It supports informed decision making and strategic planning.
Auditing and reporting in IAM solutions have practical benefits, including detecting unauthorized access or identity theft. It also helps optimize access provisioning, de provisioning, authentication, authorization, and role management. Furthermore, organizations can generate valuable evidence for audits or investigations by tracking and documenting who has access to specific resources, when, how, and why.
Analyzing and evaluating IAM data, trends, issues, and opportunities can yield valuable insights and recommendations to drive continuous improvement. This holistic approach to auditing and reporting safeguards an organization’s IAM security and compliance, contributing to its overall operational excellence and strategic growth.
Useful link: What is Identity and Access Management?
Metrics to Measure IAM Effectiveness
Executives need data driven insights to evaluate the performance of their IAM framework. The proper IAM assessment provides a clear picture of security posture, user access control efficiency, and risk exposure. Here are the key metrics every CEO, CTO, and CIO must track to ensure a robust IAM framework:
1) Authentication Success and Failure Rates
A strong IAM strategy ensures that authorized users can access systems securely without friction. Identity and access management testing must measure authentication efficiency tracking:
- Login success rates: High success rates indicate a seamless user experience.
- Failed login attempts: Repeated failures may signal compromised accounts or credential misuse.
- Multi factor authentication (MFA) adoption: A key IAM metric that ensures security while reducing unauthorized access risks.
2) Access Request Approval and Denial Trends
Executives need a real time view of how access is granted and denied across the enterprise. IAM assessment should track:
- Approval timeframes: How long does it take to process access requests? Slow approvals disrupt productivity.
- Denial reasons: Frequent denials may indicate flawed identity management strategies or excessive access requests.
- Access privilege escalation: Monitoring privilege escalation prevents insider threats and policy violations.
3) Privileged Access Monitoring and Risk Exposure
One of the most significant IAM risks stems from privileged administrator and executive accounts with high level system access. IAM risk management should measure:
- Number of privileged accounts: Excessive admin privileges increase the attack surface.
- Frequency of privilege escalations: Regular reviews ensure compliance with identity management strategies.
- Session monitoring: Tracking privileged access sessions helps detect suspicious activity before a breach occurs.
4) Orphaned Accounts and Dormant User Analysis
Inactive or orphaned accounts pose a severe security threat. IAM risk management should include:
- Orphaned accounts percentage: A high percentage of abandoned accounts is a red flag for unauthorized access risk.
- Dormant user accounts: Inactive accounts must be reviewed or removed for extended periods.
- Identity and access management: Testing must enforce automatic deprovisioning policies.
5) Compliance and Audit Readiness
Regulatory non compliance leads to hefty fines, reputational damage, and business disruption. A strong IAM strategy measures:
- Time to pass audits: Faster audit clearance means a well managed IAM framework.
- Access certification frequency: Regular IAM assessments ensure compliance with security policies.
- Identity and access management testing results: Routine security testing identifies and mitigates vulnerabilities before compliance checks.
6) Role Based Access Control (RBAC) Efficiency
IAM strategy effectiveness depends on how healthy roles are defined and managed. Track:
- Percentage of role based access: High RBAC adoption ensures minimal manual provisioning.
- Policy violations in access provisioning: if users bypass RBAC, IAM policies need refinement.
- IAM risk management effectiveness: Frequent role misuse indicates weak governance and security gaps.
The 6 Phase IAM Audit Framework
An IAM audit is most effective when conducted in a structured, phased approach with clearly defined stakeholder responsibilities. Below is a professional 6 phase IAM audit lifecycle to ensure enterprise readiness and compliance:
1) Planning and Scoping
- Define the scope of systems, applications, users, and regulatory requirements.
- Identify which environments (cloud, on premises, hybrid) are included.
2) Policy and Role Review
- Assess the currency and completeness of identity and access policies.
- Validate role definitions, RBAC, and separation of duties (SoD).
3) Credential and Access Verification
- Audit provisioning and deprovisioning processes for accuracy.
- Identify orphaned accounts, inactive users, and unnecessary privileges.
4) Configuration and Security Controls Check
- Verify MFA, SSO, and federation settings.
- Ensure the principle of least privilege is enforced across all systems.
5) Activity & Log Monitoring
- Review privileged user activity, anomaly detection, and audit logs.
- Identify policy violations and risky access patterns.
6) Reporting and Remediation
- Document audit findings and create a remediation roadmap.
- Update policies, decommission unused accounts, and close identified gaps.
Stakeholder Responsibilities:
- IT / IAM Teams: Execute lifecycle and tool based checks.
- Audit & Compliance Teams: Validate logs, policy adherence, and regulatory alignment.
- Risk / GRC: Provide governance, approve remediation, and oversee risk mitigation.
- Business Owners / HR: Support user lifecycle processes and custodial accounts.
This framework ensures clarity, accountability, and audit repeatability, making it easier to demonstrate compliance readiness and instilling a sense of responsibility in the team.
What Tools Are Required for IAM Audit and Reporting?
IT professionals have many tools when considering identity and access management audit and reporting tasks, offering flexibility based on their needs, preferences, and budget constraints. They can opt for comprehensive software or cloud based systems such as Microsoft Azure Active Directory, Okta, or IBM Security Verify, which offer integrated capabilities for managing various aspects of IAM. These platforms also include components or functions dedicated to auditing or reporting on IAM activities and outcomes.
Alternatively, there are standalone software and cloud based tools that specialize in auditing or reporting on IAM data. Examples include Varonis Data Privilege, SailPoint Identity Now, and Splunk Enterprise Security. These IAM tools provide tailored solutions to address specific IAM auditing and reporting requirements.
What to Consider Before Implementing an IAM Strategy?
A significant portion of the preparatory effort for constructing an identity and access management solutions strategy occurs before the implementation phase commences. Thorough planning is paramount to strike a harmonious balance between user friendliness and robust IAM security for user access.
Here are several factors to contemplate during the project’s inception:
1) Network Architecture Mapping
The initial implementation of an IAM strategy involves comprehending the existing network resource structure. This entails mapping out on premises router and server configurations and locally utilized critical applications. Additionally, create a schematic representation of remote work connections and any cloud based services users access. Document the current IAM procedures and scrutinize how users access and share data. This information is the foundation for transitioning from outdated IAM best practices to a practical, relevant deployment.
2) User Community and Privilege Assessment
Planners must fully understand the individuals who use resources protected by IAM tools. Establish a directory that includes all active users and associates them with their access levels and business requirements. In IAM projects, it is prudent to identify privileged users with extensive network access who are a primary target for external attackers.
3) Data and Application Risk Evaluation
Conduct a thorough risk assessment for each application. Locate confidential data within the network and identify individuals accessing it. Apply sound risk management principles to tailor the IAM strategy to safeguard these high value assets. The objective is to balance user convenience and security, potentially employing more robust IAM controls for high value applications.
4) Data Governance Enhancement
Optimizing existing data storage practices is beneficial before implementing an access management strategy. Standardize data formats to align with IAM technologies and organize data for improved visibility by security managers. Evaluate IAM security policies to ensure they incorporate robust data security regulations, including repercussions for data misuse.
5) Selection of Appropriate IAM Tools
Delve into IAM solutions and explore various technologies. Most contemporary organizations find value in cloud based IAM solutions, though legacy focused IAM options exist. Seek out products that provide essential IAM capabilities, including authentication, authorization, single sign on, auditing, and identity federation. Look for providers that support identity migrations from existing IAM tools, enabling seamless transitions from legacy solutions to multi cloud hybrid environments.
How to Create an IAM Strategy?
The planning phase is the cornerstone of establishing organizational knowledge. The first step is to consolidate this knowledge and formulate a pragmatic IAM (Identity and Access Management) strategy. While IAM strategies may differ based on the particular business context, they generally include fundamental IAM elements:
1) User Management
IAM systems should facilitate the creation of user profiles or identities that authorize access to relevant resources and enable connections to those resources via federation systems. Identity management strategies should comprehensively cover provisioning and de provisioning processes as essential components of identity lifecycle management.
2) Authentication
Access control systems are required to verify every user’s identity upon entry. Multifactor authentication, with a preference for hardware tokens, is considered a best practice. Password policies should require the use of strong passwords and regular updates.
3) Authorization
Authorization ensures that users’ access privileges align with their designated role within the organization. Users should exclusively access business data pertinent to their responsibilities, while all other resources remain restricted. Moreover, implementing Privileged Access Management (PAM) oversees administrative accounts with substantial access to sensitive data.
Additionally, authorization can involve setting time limits and granting restricted access to resources throughout a user’s session. Alternatively, broader privileges can be established based on predefined roles. Automating privilege management serves the dual purpose of time efficiency and minimizing the potential for human error in access allocation.
4) Single Sign On (SSO)
Single Sign On (SSO) is a valuable enhancement to IAM systems. It brings cloud based and on premises resources together into a unified access portal. Users input a single set of credentials, and the SSO system utilizes privileged databases to grant authorization to users across the entire network environment.
5) User Directories
IAM requires an up to date and organized directory of network users, which serves as a central reference point linking to Privileged Access Management (PAM) and IAM tools. Although Microsoft Active Directory is a common choice for many networks, hybrid cloud configurations may utilize various directory formats. The IAM strategy should focus on consolidating these directories to simplify access management, potentially involving a phased migration of existing identities to cloud based directory systems.
6) Identity Federation
Federated identities empower users to access third party Software as a Service (SaaS) applications and cloud platforms. Although cloud service providers commonly provide federation capabilities, network administrators are responsible for incorporating identity federation into their overall IAM (Identity and Access Management) strategy.
7) IAM Auditing
Effective governance and risk management practices emphasize the importance of routinely auditing identity and access management solutions. The chosen strategy should support recording access requests and user activities, along with comprehensive documentation of security alerts. Strategists must establish connections between audit data and compliance plans about relevant data regulations. Furthermore, the IAM solution should align seamlessly with compliance objectives, including, but not limited to, GDPR and HIPAA, across its components.
Useful Link: 8 Best Practices for Robust Identity and Access Management (IAM) Strategy
The 8 Point IAM Audit Checklist Includes
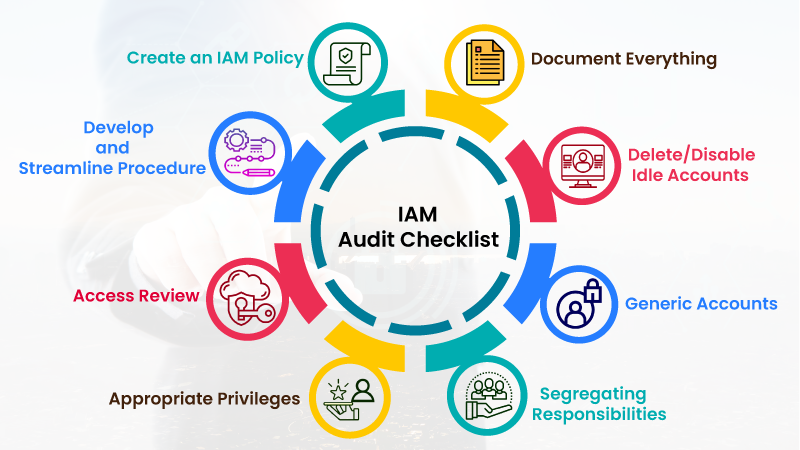
Here are 8 checklist points that can make the IAM system work as desired by the IAM Audit requirements.
1) Create an IAM Policy
Ensure the IAM process is clearly defined and crucial to your organizational security policy. Creating an IAM policy document is strongly recommended for the following reasons:
- Meet compliance requirements
- Manage user access and authorization
- Define access to stakeholders who can help make a robust IAM policy
- Robust incident response
Moreover, regularly reviewing the policy document is essential to ensure that the proper IAM best practices are updated and followed on time.
2) Develop and Streamline Procedure
It’s not enough to create a policy; you see desired results only if it’s implemented correctly. You must develop a procedure that involves all stakeholders in the IAM strategy process and defines roles.
The streamlined procedure should have a list of stakeholders with assigned responsibilities and actions for which they are accountable.
3) Access Review
In any organization, users, roles, and responsibilities change constantly. Therefore, it is essential to review access and authorizations given to different users and formulate a user access review process to ensure the proper access is given.
To avoid discrepancies, keep reviewing it at different intervals. Policy Based Access Control (PBAC) is one way to execute the user access review process.
4) Appropriate Privileges
This is the key factor that determines the robustness of an IAM system. Despite being known, this is often ignored. It’s essential to see that user access remains limited to ‘particular’ job requirements and not further. Following the Least Privileged Account principle is recommended, which calls for setting maximum resource limitations.
If you grant special privileges, revoke them immediately after the designated temporary usage period ends.
5) Segregating Responsibilities
This is a crucial aspect that can help avoid risks in the first step. Segregating duties among people keeps them limited to their respective functions, and none gets complete access. In the case of critical tasks, break them into smaller ones and assign them to multiple people. This keeps every process and its associated IAM security functions independent from others.
If a process is breached, the threat scope remains limited to that particular process, leaving the rest of the system untouched.
6) Generic Accounts
Every organization requires generic accounts to execute regular and everyday activities like training and testing. However, keeping them idle can lead to IAM security risks. Never assign admin rights to generic accounts, and delete the unused ones.
It’s important to see strong passwords bind them to avoid breaches through default settings. Privileged Access Management (PAM) and PBAC can completely control generic accounts.
7) Delete/Disable Idle Accounts
Keeping your IAM system clean, secure, and updated is essential. Delete any unused user accounts (generic or important ones) lying idle. Leaving them is like allowing them to grow further and welcome threats through them.
Delete inactive users individually and in groups. Ensure users are only present in their relevant groups. Conduct a regular review of group policies and delete exposed login details.
8) Document Everything
Let’s return to where we started. We started by documenting the policy for its effective implementation. But it’s important to document everything in implementation, too. This will serve as a trial for future implementations and help ensure compliance with the rules.
Documentation is vital to the identity and access management audit process, where you need to share administration activities, policies, and usage documented. Moreover, the documentation process gives a better understanding of the entire IAM system, helping you find ways to improve it further.
Useful Link: IAM Best Practices for Optimal Cloud Security
Common IAM Pitfalls to Avoid
A well structured IAM strategy enhances security, streamlines compliance, and improves operational efficiency. However, poor execution of identity management strategies leads to security risks, compliance failures, and operational inefficiencies. As a company executive, your digital security blueprint must be airtight. The biggest IAM failures often stem from avoidable mistakes. Let’s break down the most critical IAM pitfalls and how to avoid them.
1) Lack of a Well: Defined IAM Strategy
A strong IAM strategy is the foundation of identity security, yet many organizations either lack one or treat it as an afterthought. This results in inconsistent access controls, weak authentication processes, and security gaps that cybercriminals exploit.
Common Mistakes:
- Implementing IAM tools without aligning them with business objectives.
- Failing to integrate IAM into broader IAM risk management frameworks.
- Overlooking identity and access management testing, leading to unnoticed vulnerabilities.
How to Fix It:
- Conduct a comprehensive IAM assessment to define clear identity management strategies tailored to your business needs.
- Align IAM with regulatory compliance (e.g., GDPR, CCPA, and NIST) to reduce legal exposure.
- Build an adaptive IAM strategy that evolves with your organization’s growth and security needs.
2) Weak IAM Risk Management and Assessment Practices
Without regular IAM assessment, businesses operate blindly, exposing themselves to insider threats, credential theft, and privilege misuse. CEOs who fail to prioritize IAM risk management leave their organizations wide open to security breaches.
Common Mistakes:
- Not performing regular IAM assessments to identify risks.
- Lack of real time monitoring of identity related threats.
- Failure to implement role based access control (RBAC) leads to excessive user privileges.
How to Fix It:
- Perform frequent IAM risk management reviews to identify gaps before attackers do.
- Leverage identity and access management testing to simulate cyberattacks and stress test IAM defenses.
- Deploy risk based authentication (RBA) to adjust dynamic security requirements based on user behavior.
3) Overlooking Identity and Access Management Testing
Many organizations deploy IAM solutions but fail to test their effectiveness. Unstress tested IAM solutions often result in misconfigurations, privilege escalation risks, and authentication failures.
Common Mistakes:
- Assuming IAM tools will work “out of the box” without thorough identity and access management testing.
- Failing to test multi factor authentication (MFA) enforcement.
- Ignoring load testing IAM systems under heavy user demand.
How to Fix It:
- Regularly conduct identity and access management testing to expose vulnerabilities.
- Test IAM workflows across different user roles to identify security loopholes.
- Automate IAM assessment reports to maintain compliance and security alignment.
4) Granting Excessive Privileges Without Proper Oversight
A one size fits all approach to user access puts businesses at risk. Employees, contractors, and vendors should only have the necessary access—nothing more. Granting excessive privileges creates insider threats and weakens IAM risk management efforts.
Common Mistakes:
- Providing permanent admin access instead of Just in Time (JIT) provisioning.
- Allowing employees to accumulate permissions over time without reviewing them.
- Not enforcing the Principle of Least Privilege (PoLP).
How to Fix It:
- Conduct periodic IAM assessment reviews to revoke unnecessary privileges.
- Implement role based or attribute based access controls (RBAC/ABAC) for granular security policies.
- Automate privilege de escalation when users change roles or leave the company.
5) Ignoring Identity Lifecycle Management
Many IAM failures stem from poorly managed identity lifecycles. Organizations often fail to revoke access for former employees or delay access provisioning for new hires; both scenarios jeopardize security and productivity.
Common Mistakes:
- Onboarding delays lead to productivity loss.
- Failure to de provision accounts after employees leave.
- Not monitoring dormant or unused accounts, which become attack entry points.
How to Fix It:
- Automate identity lifecycle management with real time IAM provisioning and de provisioning.
- Conduct quarterly IAM assessments to clean up outdated user accounts.
- Enforce automated offboarding policies to prevent orphaned accounts.
IAM Trends and Future Directions
The emerging IAM trends and future directions that are reshaping identity security are:
1) Machine Identity Management: Expanding Beyond Human Access Controls
With the rise of IoT, cloud computing, and automated workflows, organizations are witnessing an explosion of non human identities, including applications, devices, and AI driven systems. These machine identities often outnumber human users, making them a prime target for cyber threats.
Future Direction:
- Automated identity governance solutions will evolve to more efficiently manage machine identities.
- Advanced cryptographic techniques, such as PKI (Public Key Infrastructure) and certificate based authentication, will be widely adopted.
- Organizations will implement continuous authentication to verify machine identities in real time, reducing the risk of credential misuse.
2) Advanced Zero Trust Architectures: From Static to Adaptive Security
Zero Trust is no longer a security principle—it’s a necessity. Organizations are shifting from static, perimeter based security models to adaptive zero trust frameworks, in which every access request is treated as a potential risk. Continuous verification, least privilege access, and identity segmentation are becoming standard IAM practices.
Future Direction:
- AI driven analytics will enhance risk based authentication and real time anomaly detection.
- Passwordless authentication methods (e.g., biometrics and hardware security keys) will replace traditional login credentials.
- Just in time (JIT) access provisioning minimizes overprovisioning risk by granting temporary access rather than permanent privileges.
3) AI Enabled Identity Governance: The Rise of Predictive and Generative AI
IAM solutions integrate Artificial Intelligence (AI) and Generative AI to automate identity management and enhance decision making. AI driven IAM systems can more accurately predict security threats, detect behavioral anomalies, and automate access provisioning.
Future Direction:
- Generative AI will personalize identity verification processes, reducing friction while improving security.
- AI driven risk scoring will dynamically adjust user access permissions based on behavior patterns.
- Autonomous IAM systems will be capable of self healing, identifying security gaps, and mitigating risks proactively.
4) Identity Threat Detection and Response (ITDR): Strengthening IAM Security Postures
As identity based attacks (such as phishing, credential stuffing, and privilege escalation) increase, Identity Threat Detection and Response (ITDR) is becoming an essential security component. ITDR integrates advanced analytics, threat intelligence, and behavioral monitoring to identify anomalous identity activities before they escalate into breaches.
Future Direction:
- Security teams will deploy automated identity forensics tools to analyze login patterns and detect compromised accounts.
- IAM and Security Operations Centers (SOCs) will collaborate to create adaptive access control mechanisms that respond dynamically to security threats.
- Continuous identity risk assessment will replace periodic compliance audits, providing real time threat visibility.
5) Decentralized Identity Solutions: The Shift Toward Self Sovereign Identity
As concerns around privacy, data ownership, and centralized authentication risks grow, decentralized identity solutions are gaining traction. Blockchain based IAM frameworks enable users to own and control their digital identities without depending on a central authority.
Future Direction:
- Organizations will adopt self sovereign identity (SSI) models that allow users to verify credentials without exposing sensitive data.
- Decentralized Identifiers (DIDs) and Verifiable Credentials (VCs) will enable enterprise privacy first authentication.
- Governments and enterprises will explore digital identity wallets for secure and frictionless identity verification.
IAM Audit Maturity, KPIs, and Decision Framework
By incorporating maturity models and measurable KPIs into your IAM strategy, you can elevate it beyond a single audit cycle, enabling you to track progress, optimize controls, and reduce access related risks over time.
By using this approach, you can track progress, optimize controls, and reduce access related risks over time, giving you the confidence that your IAM strategy is on the right track.
IAM Audit Maturity Levels
1) Basic / Manual Reviews: Spreadsheets and ad hoc checks
2) Policy Enforced: Documented IAM policies and approvals
3) Automated Provisioning: Lifecycle automation with alerts
4) Risk Aware Auditing: Prioritizes high risk users and privileged Access
5) Continuous Monitoring: Real time anomaly detection and remediation
Key Audit KPIs
- Orphan/Inactive Account Removal Rate (%)
- Mean Time to Revoke Access after employee departure
- Privileged Account Audit Coverage (%)
- Audit Findings Closure Cycle Time
- Policy Violation & Exception Rate (%)
Case Study: Manufacturing Firm Secured by Robust IAM Solution
A leading manufacturing company partnered with Veritis to address growing concerns around fragmented user access and compliance gaps. Veritis conducted a comprehensive IAM audit and implemented a centralized identity management solution featuring multi factor authentication, role based access controls, and automated user provisioning. This initiative aligned with key audit checkpoints, significantly reducing security vulnerabilities and ensuring regulatory compliance. The success of this engagement underscores not only the importance of a structured IAM strategy but also the necessity of regular audits, which are critical to building a secure and scalable identity framework.
The complete case study is available here: Manufacturing Firm Secured by Robust IAM Solution.
Conclusion
Identity and Access Management solutions are indispensable in contemporary cybersecurity efforts, serving as a defense against evolving threats and stringent compliance requirements. Organizations should adhere to an 8 point Identity and access management audit checklist to fortify their IAM security postures and craft a comprehensive IAM strategy. This checklist covers key steps, including policy creation, streamlined procedures, privilege assignment, and access reviews, to maintain robust security and IAM regulatory compliance.
With a perfect IAM strategy, you can mitigate identity and related risks, including identity vulnerabilities and sprawl, challenges with unused/legacy systems, and vendor lock in. Looking for support for IAM Solutions and Services?
Veritis, an organization recognized for industry excellence, with accolades including the Stevie and Globee Business Awards, offers specialized identity and access management services. With Veritis as a trusted partner, organizations can enhance their IAM systems, ensuring robust security and seamless regulatory compliance. By leveraging Veritas’ expertise, businesses can navigate the complex IAM landscape, safeguarding their valuable assets and data in an ever evolving digital world.