
DevSecOps model aims to bring the various aspects, i.e., development, security, and operations, under one umbrella to pursue a singular objective. DevSecOps aims to ensure the same level of development and operations throughout the entire process, from inception to maintenance.
Organizations face numerous obstacles, including staff shortages and gaps between collaborating teams in the DevSecOps process.
According to Gartner (2024), organizations that integrate DevSecOps into their CI/CD pipelines reduce deployment times by 40% while significantly improving their security posture. For executive leadership, this means less business risk and faster innovation without compromise.
Developing and maintaining software is a continuous and complicated process that involves close collaboration between Development (Dev) and Operations (Ops) teams. This collaborative approach, known as DevOps, was coined a decade ago by software engineers John Allspaw and Paul Hammond while discussing their successes at Flickr, where they achieved better alignment between these two teams. However, as the need for increased security in information systems has grown, the term has evolved into DevSecOps principles, which include a specialized security team in the development process.
DevSecOps involves considering security from the outset when developing software and setting up systems. This way, security is automated and works consistently without slowing the development process. You must choose the right tools to easily add security measures. However, remember that incorporating security into DevOps requires a shift in how companies think and work together to meet everyone’s expectations for creating and maintaining products.
Talk to an Expert About DevSecOps Process
How do We Ensure Security Without Compromising Agility?
Executives often fear that adding security to the software delivery pipeline will slow innovation. However, modern DevSecOps strategies enable security-driven innovation by embedding CI/CD security integration early, without delaying time to market.
Do security processes slow down the agility of delivering solutions quickly to the market? Our DevOps engineers debunked the idea of “DevOps versus security” and confirmed that security is now an essential part of DevOps practices. The DevOps culture is evolving into DevSecOps automation. Let’s examine the factors that facilitate the seamless DevOps security integration, without creating tensions between the two teams.
1) Automating DevOps Security Tools and Processes
Automating tasks helps prevent security mistakes and reduces downtime and vulnerabilities. Automated tools help you quickly spot potential threats, infrastructure issues, and vulnerable code. Prioritizing automation makes it simpler to identify and fix problems.
To enhance security in DevOps, automate the management of configurations, vulnerabilities, privileged credentials, patching, and code analysis using DevOps best practices. This will allow security to integrate effectively into the entire DevOps process.
If security practices are much slower than the DevOps process, there might be resistance to adopting them. To overcome this, automated security testing and compliance should be included early to enhance software quality.
Automation also helps address regulatory compliance automation needs by ensuring that all security checks and audits are consistently enforced across environments.
2) Establishing Shared Responsibility
For a C-level executive, fostering cross-functional alignment between security and development teams is not just a cultural shift. It’s a business imperative. Collaboration is essential in DevOps, and it means everyone shares responsibility. Developers and security teams must work closely to integrate security into the DevOps process, adhering to best security practices.
Continuous knowledge and information sharing between security and development teams is crucial for maintaining shared goals. As a custom software development company, we utilize automated solutions to effectively secure our applications and services.
3) Enforcing Policy and Governance
Developing easy-to-understand cybersecurity policies for developers is vital for the security of DevOps processes. These policies help teams meet security requirements while coding and ensure security and compliance throughout the development process.
In DevSecOps automation, the security team establishes security and compliance policies, and the development team implements them at each stage of the CI/CD pipeline. This way, you can match the speed of application development in a DevOps environment while maintaining security.
Governance that aligns with board-level cybersecurity strategy not only mitigates threats but ensures your organization meets its DevSecOps risk management and compliance goals.
Useful link: Data Security in the Cloud Solutions Every Modern Business Needs
What Are the Key Principles and Goals of DevSecOps?
According to Forrester, DevSecOps adoption leads to a 35% reduction in remediation costs, delivering a measurable security ROI across software development lifecycles. DevSecOps means prioritizing security from the start of the development process rather than treating it as an afterthought. Integrating security practices into DevOps encourages collaboration between developers, operations, and security teams to ensure secure and reliable software.
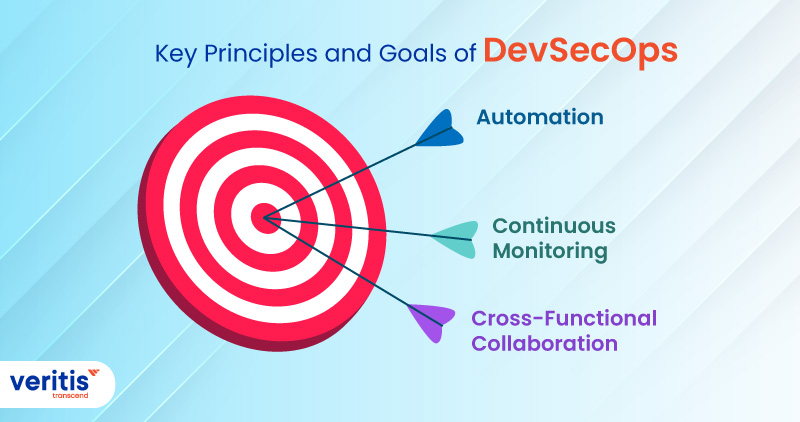
DevSecOps principles center on three core concepts: automation, continuous monitoring, and collaboration across various teams.
1) Automation
Automation in DevSecOps ensures consistency and repeatability in security practices. It includes automated testing, vulnerability scanning, and configuration management.
2) Continuous Monitoring
Continuous monitoring in DevSecOps means regularly assessing and adjusting security controls as necessary.
3) Cross-Functional Collaboration
Cross-functional collaboration in DevSecOps encourages teams to communicate and share knowledge, breaking down group barriers. This approach enables a holistic approach to security.
Addressing security early and consistently reduces the risk of vulnerabilities and breaches, while also improving the speed and efficiency of the software development process. Integrating security into DevOps security best practices allows organizations to balance speed, agility, and strong security, resulting in safer and more reliable software applications.
Useful link: All You Need to Know About DevSecOps and its Implementation
What Are the Benefits of DevSecOps Implemention?
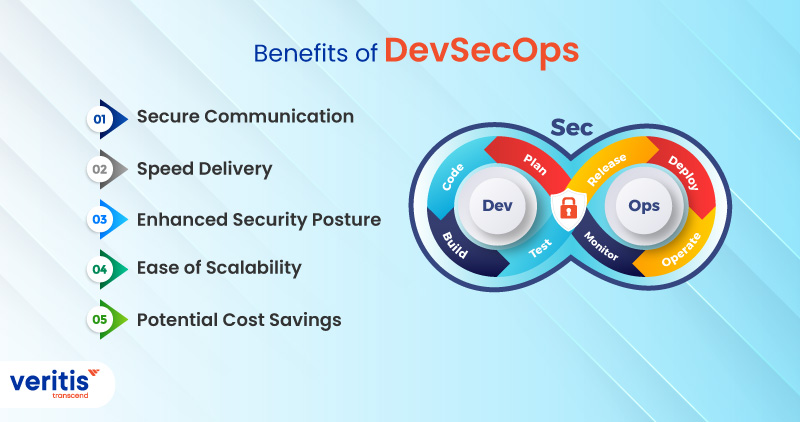
Benefits of DevSecOps offers numerous benefits, including the following:
1) Secure Communication
DevSecOps is valuable because it breaks down barriers between development teams. It enables operational and development teams to work together, share expertise, and enhance each other’s processes and practices.
DevSecOps specialists communicate with various teams and educate them on the principles of DevOps and security. They utilize cloud-native technologies, such as encryption and secure VPN services, to maintain security while collaborating with others.
DevSecOps helps clarify and resolve issues, such as finding the right person or team to fix a problem and ensuring all team members can effectively meet security targets.
2) Speed Delivery
Integrating security into the CI/CD pipeline detects bugs and vulnerabilities early, ensuring prompt resolution. It boosts developers’ confidence in code reliability, enabling them to focus on delivering new features. This approach enhances overall security and accelerates the development process, leading to faster software delivery.
3) Enhanced Security Posture
DevSecOps services offer the primary advantage of creating a secure environment for development teams. It ensures security throughout the entire software development lifecycle, from pre-production stages to production, testing, and software delivery.
In this strategy, security is an essential part of software development, not an afterthought. It begins by implementing basic security techniques, including integrating enterprise firewalls, monitoring server logs, securing production workloads, and requiring employees to use VPNs.
4) Ease of Scalability
Manual replication is no longer necessary once DevSecOps framework processes and tools are established and tested. This is particularly helpful when frameworks are needed in different locations or when additional computing resources are required.
DevSecOps ensures security is consistently implemented as the environment adapts to new demands. With the aid of DevSecOps automation, scaling these security processes and systems up or down becomes simple with just a few clicks.
5) Potential Cost Savings
DevSecOps principles accelerate the development and software delivery process by detecting and resolving real-time security issues. This results in DevOps teams requiring fewer working hours to complete projects, leading to cost savings for organizations.
IBM’s 2024 Cost of a Data Breach Report revealed that every $1 invested in DevSecOps yields an average of $6 in avoided breach and downtime costs.
Moreover, the reduced likelihood of security issues can also decrease the number of people required in the operation teams to carry out a secure software development lifecycle process.
To mitigate this, a smooth transition from conventional practices to a sophisticated DevOps pipeline is necessary. Organizations should leverage a range of DevSecOps best practices to implement DevSecOps security.
Useful link: Pros and Cons of DevSecOps
What Are the Top 6 DevSecOps Best Practices to Follow?
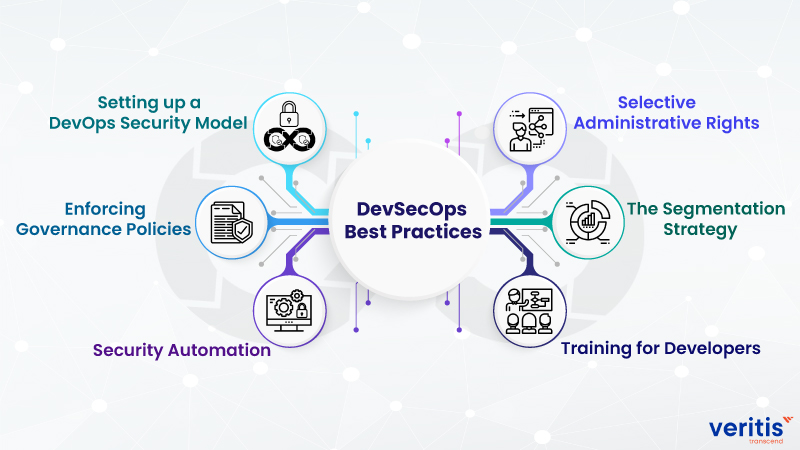
Here are the Top 6 DevSecOps Best Practices:
1) Setting up a DevOps Security Model
Perhaps the primary step in adopting the DevSecOps model is to incorporate Identity and Access Management (IAM), cybersecurity measures, code review, configuration, and governance through the DevOps security tools.
Assigning security to the various stages of the DevOps security best practices pipeline makes it easy to ensure the secure release of products and reduce the likelihood of glitches, bug fixes, and recalls after product release through the DevSecOps process.
2) Enforcing Governance Policies
One key aspect of the DevSecOps model is setting up governance policies and IT protocols that ensure data protection throughout the DevSecOps pipeline. Since operations vary within an organization, the roles and responsibilities of the board, committee, and officers will be affected in some way.
Hence, it is essential to adhere to regulations and procedures to safeguard the DevSecOps framework and maintain transparency within the organization. Setting transparency will also help combat suspicious internal threat behavior and negate any damage.
3) Security Automation
Security teams must be fast and agile during the development of DevOps to ensure high security. This requires automation to reduce errors and maximize the efficiency of the DevSecOps pipeline. Additionally, through vulnerability testing and privilege management, organizations can save resources and reduce work hours and costs with DevSecOps tools.
4) Training for Developers
When adopting the DevSecOps framework, one of the biggest challenges is obtaining 100% cooperation from your stakeholders. Various teams, such as development, operations, and security, operate in their silos, promote their agendas, and align tasks.
It is a significant challenge to determine the optimal investment amount and allocate sufficient time for the development team to understand secure coding for DevSecOps.
5) The Segmentation Strategy
Another way to implement DevSecOps best practices is to avoid hackers and attackers through segmentation. This is a great way to employ the divide-and-conquer strategy. Access to the application resource server becomes limited, addressing issues from a continuous workflow.
Hence, dividing the network into segments makes it extremely difficult for hackers to access the data illegally in one go. This is a powerful technique in DevSecOps security as it reduces hackers’ threats and makes errors negligible.
6) Selective administrative rights
One of the most effective ways to mitigate internal threats on the DevSecOps security automation is to maintain minimal privileges. This helps keep the amount of data accessible by a single party to a minimum. It is one of the DevSecOps best practices as it helps local machines store essential data for regulating access.
Here are additional 5 DevSecOps Best Practices
1) Shift-Left Security Practices
Traditionally, security was introduced late in the software development lifecycle. Today, CIOs and CISOs demand proactive “shift-left” security. By embedding vulnerability scans and threat modeling during design and coding, enterprises reduce remediation costs by up to 30–40% compared to post-release fixes.
Executive Insight: Treat security issues like financial debt; the longer they remain unresolved, the higher the cost of repayment.
2) Automate Security in CI/CD Pipelines
Agility thrives on automation. By integrating automated security tests, static analysis, dynamic testing, and dependency scanning directly into pipelines, we ensure that every build is not only fast but also robust and secure, providing you with peace of mind.
- Automated code scans flag risks instantly.
- Compliance checks run in the background.
- Penetration testing bots simulate attacks pre-release.
Outcome: Security becomes continuous, not a bottleneck.
3) Adopt Cloud-Native DevSecOps
As enterprises migrate to cloud, Kubernetes, and containers, cloud-native DevSecOps safeguards workloads at scale. Best practices include:
- Policy-as-Code to enforce standards automatically.
- Runtime monitoring to detect abnormal activity.
- Infrastructure-as-Code (IaC) scanning to prevent misconfigurations.
Result: Enterprises reduce cloud misconfigurations, the cause of 27% of breaches, while maintaining scalability.
4) Continuous Compliance and Governance
Regulatory requirements from HIPAA to SOC 2 demand continuous assurance. DevSecOps best practices embed compliance frameworks into pipelines, ensuring audit-readiness is a daily outcome, not a quarterly scramble.
Example: Automated controls, such as automated library approval processes, ensure only approved libraries are deployed, instantly aligning with ISO 27001 and PCI DSS.
5) Integrate Threat Intelligence and Monitoring
Executives increasingly expect real-time visibility into evolving risks. DevSecOps pipelines can integrate threat intelligence feeds, anomaly detection, which identifies unusual patterns that could indicate a security threat, and AI-driven monitoring to pre-empt attacks.
C-Suite Metric: Time to detect and respond to incidents is cut from 258 days (industry avg.) to near real-time with automated threat detection.
Case Study: DevOps Approach Quickens Software Development Time
Veritis partnered with a leading U.S. e-commerce provider to accelerate the rollout of its Entitlement Management System (EMS) and migrate critical infrastructure.
Challenge
- Unreliable, slow builds with no centralized CI server
- Over 300 on-premises Linux servers need AWS migration and consistent management
- Manual processes create bottlenecks and collaboration gaps
Solution
- Secure CI/CD pipelines and adopted Infrastructure as Code for repeatable builds and provisioning
- Migrated 300+ servers to AWS with automated environment setup
- Delivered 24/7 support and integrated automated compliance DevSecOps audits
Outcomes
- Doubled release speed with stable, predictable deployments
- Eliminated manual tasks, boosting developer productivity
- Strengthened system reliability and regulatory compliance
Read the complete case study: DevOps Approach Quickens Software Development Time.
How Does Veritis Help You Implement DevSecOps Successfully?
Veritis, the Stevie Award winner, offers DevSecOps security through an approach that incorporates security as an essential aspect of DevOps best practices. We believe in glitch-free building systems, with all loopholes addressed at the beginning stages of development.
Veritis has been the trusted DevSecOps transformation partner for Fortune 500 companies aiming to modernize legacy environments while ensuring secure cloud adoption. Our enterprise-ready solutions ensure scalability, compliance, and faster innovation without sacrificing security. Our excellence in DevOps has surpassed that of our competitors, earning us the Stevie Award. With our expertise, we will modernize your legacy infrastructure. So, reach out to us and embrace a cloud solution that suits you best.