
Table of contents
In the face of a notable surge in security breaches, organizations recognize the importance of prioritizing a security first approach. As experts anticipate an escalation in hacker tactics, adopting a security first mindset becomes indispensable for enterprises spanning various industries.
Organizations possess diverse tools and solutions for integrating security into their Software Development Lifecycle (SDLC). Due to the varying structures, processes, toolsets, and overall maturity levels of different SDLCs, there is no universally applicable blueprint for implementing DevSecOps.
For CIOs aiming to address security vulnerabilities throughout their company’s production stages, DevSecOps proves highly beneficial, simultaneously reducing time to market. According to the latest survey, 90% of companies are progressing through different DevSecOps stages, with 42% indicating plans to implement DevSecOps within the next year fully.
DevSecOps phases extend modern DevOps methodologies by integrating security processes and automation into the development pipeline. This allows development teams to maintain the momentum of rapid and continuous delivery while enhancing the security of software assets. The DevSecOps model pipeline adheres to the well known DevOps “infinity loop” structure, incorporating additional DevSecOps steps to protect code security before, during, and after its deployment to production.
What is DevSecOps Services? The DevSecOps process handles IT security with the mindset that “everyone is accountable for security.” It involves injecting security into a company’s DevOps pipeline. The aim is to integrate security throughout the software development life cycle (SDLC) stages. The DevSecOps phases indicate that you shouldn’t leave security for the final stage of the SDLC, as was the case with traditional development methods.
If your business already uses DevOps, consider upgrading it to DevSecOps integration. DevSecOps phases are primarily built on the DevOps services, which will guide your case for switching. By doing this, you’ll be able to assemble talented specialists from various technical disciplines to enhance your security procedures as they currently stand.
DevSecOps is a way of thinking or a culture that IT operations and developers’ teams follow when creating and deploying software applications. Agile application development incorporates both active and automated security audits, as well as penetration testing.
To implement the DevSecOps process, you need to:
- Reducing vulnerabilities in software programming incorporates the concept of security from the beginning of the SDLC.
- Please make sure everyone, including IT operations teams and developers, shares responsibility for adhering to security procedures in their tasks.
- Ensure DevOps workflow begins with the involvement of security controls, processes, and tools. This will allow for automatic security checks throughout the software delivery process.
DevOps managed services have always been about integrating security into the development and release process, as well as quality assurance (QA), database management, and other aspects. The DevSecOps process, on the other hand, is an extension of that process, where security is always the crucial component.
Useful link: What is DevSecOps Services?
How to Adopt DevSecOps with Your Team?

In software development, DevOps best practices have sparked a revolution. It combines software development, deployment, and management into one process. Operations and development teams would merge into a single team; otherwise, they would collaborate closely. The advantages are faster updates and improved cycle control for software releases.
Likewise, there has been a growing understanding that security must be an essential component of the development process. Writing code takes longer and doesn’t work well until you figure out how to make it secure. The phrase “DevSecOps” was created due to the convergence of these trends.
The core concept of the DevSecOps process is that everyone is responsible for security. Management must consider it when defining requirements and developing schedules. Developers must incorporate it into every facet of code and specifications. QA professionals must test security and functionality. Ultimately, operations teams must closely monitor software behavior and respond promptly to any issues that arise.
Each party must adopt a new mindset for DevSecOps implementation. They must establish a strong line of communication because they each have specific tasks. No issues ought to be overlooked due to a lack of communication. Security teams have frequently been separated from other groups during the development cycle. With the DevSecOps model, they are included in each stage of the DevSecOps process and are available to offer input.
To adapt, software development, maintenance, and upgrading must incorporate security awareness into each stage.
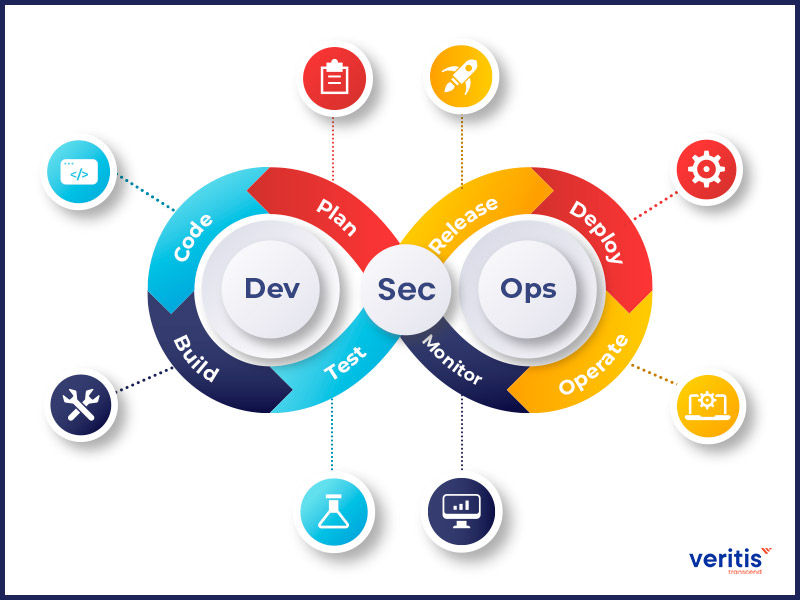
1) Plan
The DevSecOps planning phase is the least automated, yet crucial, for successful integration. It involves collaboration, discussion, review, and a strategy for security analysis. Teams must conduct a thorough security analysis and develop a detailed schedule for security testing, specifying where, when, and how they will carry it out.
IriusRisk, a collaborative threat modeling tool, is a well liked DevSecOps planning tool. Other tools for collaboration and conversation, like Slack, and solutions for managing and tracking issues, like Jira Software, are also available.
2) Code
Using DevSecOps technologies during the code phase can help developers produce more secure code. Code reviews, static code analysis, and pre commit hooks are essential security procedures in the code phase.
When security technologies are directly integrated into developers’ existing Git workflow, every commit and merge automatically starts a security test or review. These technologies support different integrated development environments and many programming languages. Some popular security tools include PMD, Gerrit, SpotBugs, Checkstyle, Phabricator, and FindBugs.
3) Build
The ‘ build ‘ step begins once developers have developed code for the source repository. The primary objective of DevSecOps build tools is to automate the security analysis of the build output artifact. Static application software testing (SAST), unit testing, and software component analysis are crucial security procedures. Tools can be implemented into an existing CI/CD pipeline to automate these tests.
Dependencies on third party code, which may come from an unidentified or unreliable source, are frequently installed and built upon by developers. Additionally, dependencies on external code may unintentionally or maliciously introduce vulnerabilities and exploits. Therefore, reviewing and checking these dependencies for potential security flaws during the development phase is crucial.
The most popular DevSecOps tools for build phase analysis include Checkmarx, SourceClear, Retire.js, SonarQube, OWASP Dependency Check, and Snyk.
4) Test
The test phase is initiated once a build artifact has been successfully built and delivered to staging or testing environments. Execution of a complete test suite requires a significant amount of time. Therefore, this stage should fail quickly to save the more expensive test tasks for the final stage.
Dynamic application security testing (DAST) tools are utilized throughout the testing process to identify application flows, including authorization, user authentication, endpoints connected to APIs, and SQL injection vulnerabilities.
Multiple open source and paid testing tools are available in the current market. Support functionality and language ecosystems include BDD Automated Security Tests, Boofuzz, JBro Fuzz, OWASP ZAP, SecApp suite, GAUNTLET, IBM AppScan, and Arachi.
5) Release
When the DevSecOps cycle is released, the application code should have undergone extensive testing. The stage focuses on protecting the runtime environment architecture by reviewing environment configuration values, including user access control, network firewall access, and personal data management.
One of the main concerns of the release stage is the principle of least privilege (PoLP). PoLP signifies that each program, process, and user needs the minimum access to carry out its task. This combines checking access tokens and API keys to limit access for owners. Without this audit, a hacker can come across a key that grants access to parts of the system that are not intended.
Configuration management solutions are crucial security components in the release phase. This stage enables the review and auditing of the system configuration. As a result, commits to a configuration management repository may be used to change the configuration, which becomes immutable. Some well liked configuration management tools include HashiCorp Terraform, Docker, Ansible, Chef, and Puppet.
6) Deploy
If the earlier process goes well, it’s the proper time to deploy the build artifact to the production phase. During deployment, the security problems affecting the live production system should be addressed. For instance, it is essential to carefully examine any configuration variations between the current production environment and the initial staging and development settings. Additionally, production TLS and DRM certificates should be reviewed and validated in preparation for the upcoming renewal.
The deploy stage is a good time for runtime verification tools such as Osquery, Falco, and Tripwire. It can gather data from an active system to assess if it functions as intended. Organizations can also apply chaos engineering principles by testing a system to increase their confidence in its resilience to turbulence. Replicating real world occurrences, such as hard disk crashes, network connection loss, and server crashes, is possible.
7) Operation
Another critical phase is operation, and operations personnel frequently perform periodic maintenance. Zero day vulnerabilities are terrible, and operations teams should monitor them frequently. DevSecOps integration can use IaC tools to protect the organization’s infrastructure while swiftly and effectively preventing human error from slipping in.
8) Monitor
A breach can be avoided if security is constantly monitored for abnormalities. As a result, it’s crucial to implement a robust continuous monitoring tool that operates in real time to monitor system performance and spot exploits at an early stage.
Useful link: DevSecOps Solution to Cloud Security Challenge
DevSecOps Tools, Activities, and Automation by Phase
Here’s a tactical breakdown of tools, activities, and automated security gates across each phase of the DevSecOps methodology:
| Phase | Key Activities | Tools and Frameworks | Automation Gates |
| Plan | Define threats, business risks | IriusRisk, ThreatModeler | Security goals validated before kickoff |
| Design | Threat modeling, architectural risk analysis | Microsoft SDL, OWASP Threat Dragon | Architecture is approved only if secure |
| Code | SAST, secret scanning, secure coding | SonarQube, GitGuardian, ESLint | Block commits with critical issues |
| Build | SCA, binary validation, SBOM generation | Snyk, OWASP Dependency Check, Syft | Fail build on vulnerable dependencies |
| Test | DAST, IAST, API testing | OWASP ZAP, Burp Suite, Postman Security | Require full coverage and pass on criticals |
| Release | Native mobile testing | Checkov, Terraform Validator, Trivy | Fail pipeline on misconfigurations |
| Deploy | Least privilege enforcement, container hardening | KICS, Polaris, Kube bench | Block deploys without passing security checks |
| Operate | Runtime protection, incident detection | Falco, GuardDuty, Sysdig Secure | Alert and auto remediate runtime threats |
| Monitor | SIEM, anomaly detection, metrics tracking | Datadog, Splunk, New Relic | Trigger investigations on unusual behavior |
| Feedback | Audit, lessons learned, continuous improvement | Jira, Confluence, Retrospective Frameworks | Feed issues into new sprints |
Benefits of DevSecOps
DevOps has transformed the software industry, and integrating security into this paradigm, known as DevSecOps, is elevating software development practices. Embracing DevSecOps services offers various advantages, such as:
1) Rapidly Addressing Security Vulnerabilities
A significant advantage of DevSecOps lies in its prompt handling of newly discovered vulnerabilities. By seamlessly integrating vulnerability scanning and patching into the release cycle, DevSecOps significantly enhances the ability to detect and address common vulnerabilities and exposures promptly. This, in turn, reduces the timeframe during which threat actors can exploit vulnerabilities in public facing production systems.
2) Shared Responsibility Across Teams
DevSecOps aligns development and security teams from the outset of the development cycle, fostering a collaborative cross team approach. Rather than adhering to a siloed and disjointed operational approach that stifles innovation and triggers conflicts, DevSecOps encourages teams to synchronize early, promoting effective cross team collaboration.
3) Improved Application Security
DevSecOps employs a proactive approach to addressing security vulnerabilities in the early stages of the DevSecOps lifecycle. Development teams in the DevSecOps phases utilize automated security tools to test code and conduct seamless security audits, thereby avoiding any hindrance to the development process or the software delivery pipeline.
Throughout the various phases of the development process, the DevSecOps lifecycle involves reviews, audits, tests, scans, and debugging to ensure that the application successfully clears crucial security checkpoints. In the event of security vulnerabilities emerging, collaboration between application security and development teams ensues, involving a joint effort to conduct security analysis and devise solutions at the code level.
4) Swift and Economical Software Delivery
DevSecOps’ quick and secure delivery approach not only saves time but also reduces costs by minimizing the need to revisit processes to address security issues after the fact. Integrating security in this process is efficient and cost effective, eliminating redundant tasks and unnecessary rework and reviews, thereby enhancing overall security measures.
5) Suitable for Automation in a Contemporary Development Team
The DevSecOps phases empower software teams to integrate security and observability seamlessly into DevSecOps automation, accelerating the SDLC and ensuring a more secure software release process.
Automated testing plays a crucial role in verifying that integrated software dependencies, such as libraries, frameworks, and application containers, meet the required security standards, particularly in cases where unknown vulnerabilities exist. DevSecOps automation testing confirms that the software has successfully undergone security unit testing across all levels of the software. This comprehensive approach includes testing and securing code through static, dynamic, and dependency analyses before the final software is deployed to production. Automated tools can scan containers and scrutinize their dependencies to identify and report vulnerable components.
Useful link: Achieving Continuous Application Security with DevSecOps
DevSecOps Best Practices

The three main principles of DevOps automation tools are speed, agility, and collaboration. However, DevOps lifecycle teams frequently have unique security challenges. As a result, the DevOps framework model and the DevSecOps model must be aware of numerous potential security concerns, ranging from protecting production environments to securing the application development process. DevOps has multiple benefits.
We’ve compiled a list of 5 DevOps best practices and security tools issues to help you stay ahead of the curve.
1) Protect Your Production Environment
User applications will eventually be deployed to and utilized by clients in your production environment. As a result, it’s critical to make this environment as secure as possible. Developing different layers in your production environment, each with a different level of access and security constraints, is one method to achieve this.
2) Implement Role Based Access Control (RBAC)
One type of access control is role based access control (RBAC), which limits access to DevOps technologies’ resources based on users’ responsibilities. For instance, you may create roles such as “developer” and “testing” with access to different areas of your staging environment and code repositories. By implementing RBAC, you can reduce the potential damage caused by insider threats.
3) Ensure the Security of the Application Development Process
A safe application development approach is the starting step in securing your DevOps services company’s pipeline. This entails limiting the authorized developers’ access to your code repositories. It also guides you in working with developers you can depend on to complete the task and always follow cybersecurity best practices.
4) Secure Sensitive Information
Any information that could be used to identify or harm an individual should be encrypted during storage and transmission. This involves sensitive information, including health details, credit card numbers, and Social Security numbers.
Using Pretty Good Privacy (PGP) encryption is one process for encrypting data. To secure your data, PGP involves public key cryptography and is symmetric.
5) Implement Two Factor Authentication (2FA)
Access to DevOps consulting services resources can be secured by using two factor authentication (2FA), an additional layer of security. With 2FA, a user must present two unique forms of identification to prove their identity and access.
The first element is something they are aware of, such as a password, and the second element is mainly generated on a device they own, like a mobile phone. Even if a user’s password is hacked, 2FA can prevent unauthorized access to resources and systems.
Useful link: Need to Know About DevSecOps and its Implementation
Implementing DevSecOps Challenges
Implementing DevSecOps automation presents multiple challenges. Let’s review the three critical challenges in adopting DevSecOps.
1) Addressing and Fixing Vulnerabilities
Security Boulevard survey report revealed that in companies without DevSecOps, 50% of apps are always susceptible to attack. Additionally, since security testing often occurs at the end of the development cycle, developers frequently patch or rewrite code late in the process, which adds time and expense.
2) Complexity in the Cloud
The Flexera State of the Cloud report revealed that 92% of enterprises use several public clouds. These multi cloud installations often employ various cloud services and heavily rely on automation, making it challenging for security teams to keep up. Data security, compliance assurance, and ongoing infrastructure security pose significant issues.
3) Compatibility Issues
The DevSecOps strategy team uses multiple open source tools, including a repository of frameworks, scripts, libraries, and templates. While these tools increase productivity, if they are not correctly used or audited, they may also cause security problems.
Useful link: Pros and Cons of DevSecOps
DevSecOps Security Monitoring

Once an application has been deployed and stabilized in a live world production environment, additional security precautions are necessary. Organizations must continuously monitor their live applications for attacks or leaks using security monitoring loops and automated security checks.
Inbound security threats are detected and blocked in real time through runtime application self protection (RASP). RASP monitors incoming attacks and enables the application to autonomously reconfigure itself without user intervention in response to specified conditions. Some DevOps challenges are Test data, manual deployment, and manual testing.
DevSecOps Maturity Model: Measure and Optimize Your Lifecycle
Adopting DevSecOps is a journey. This maturity model helps you benchmark progress and identify areas to improve:
| Maturity Stage | Description |
| Initial | Manual security, isolated tools, inconsistent enforcement |
| Managed | Defined phases, some automation, improved collaboration |
| Optimized | Full integration, automated gates, real time monitoring with AI driven insights |
Key Metrics to Track
- Mean Time to Remediation (MTTR)
- Vulnerability escape rate (production bugs from known CVEs)
- % of code scanned before release
- % of IaC or container configs validated
- Number of releases blocked due to failed security gates
DevSecOps Trends: AI and Automation for the Next Generation
Excitingly, the future of DevSecOps is here. Modern lifecycle models are now integrating AI, runtime intelligence, and policy as code, promising to revolutionize performance and security in ways we’ve never seen before.
Emerging Best Practices
- AI generated security summaries to reduce alert fatigue
- Runtime based vulnerability prioritization
- SBOM enforcement in the build and release phases
- Use of minimal container images for reduced attack surface
- Policy as Code to eliminate “clickOps” and manual errors
Case Study: DevSecOps Implementation for an Energy Services Firm
Veritis, in a strategic partnership with a global energy services provider, demonstrated the power of DevSecOps. They integrated SAST (SonarQube) and automated DAST into every CI/CD phase, enforced secure environments via Ansible driven Infrastructure as Code, unified GitHub, Jira, Artifactory/Nexus, and Docker workflows, and delivered security by design training. This comprehensive approach resulted in 50% faster releases and, importantly, a significant 70% reduction in production incidents, providing reassurance of the system’s robustness and continuous compliance.
Discover the complete story: DevSecOps Implementation: A Game Changer for an Energy Services Firm.
Conclusion
Security must be their primary priority as more development teams modernize their procedures and use new tools. DevSecOps is a cyclical process that requires continuous improvement and application to every deployment of new code. The development of modern software teams is crucial, as attacks and exploits are constantly evolving.
DevSecOps is a new way of security, and technologies designed for it should be widely implemented. DevSecOps principles will help our continuous pipeline reduce the chance of security flaws, boosting customer confidence in the organization.
Veritis, the Stevie Award winner for DevOps solutions, offers the best customized solution for your DevSecOps lifecycle. We offer a range of technological services designed to enhance your business cost effectively. Partner with us to enhance productivity and streamline security across the phases of DevSecOps using the most advanced tools available.