What is the Difference Between Identity Management and Access Management?

Table of contents
Introduction
IAM, or identity and access management, is a framework of corporate procedures, laws, and technological advancements that makes managing digital or electronic identities easier. Information technology (IT) administrators can restrict user access to sensitive data within their businesses by putting a privileged identity management architecture in place. Access management methods for IAM include single sign-on, two-factor, multi-factor, and privileged access management. Additionally, these identity management solutions offer the capability of safely storing identification and profile data and data governance features to guarantee that only information that is required and pertinent is shared.
The discipline of controlling access to corporate resources to safeguard systems and data is known as identity management and access control. It can assist in confirming your users’ identities before allowing them the appropriate access to workplace systems and information as a crucial part of your security architecture. Although the phrases identity management solutions, authentication, and access management are sometimes used interchangeably, each function as a separate level in the service access management realm.
Access management systems may be set up on-site, made available by access asset managers under a cloud identity subscription model, or in a hybrid approach.
IAM fundamentally consists of the following elements:
- Identification of personnel
- Demarcation of roles to restrict unwarranted access
- Granting access permissions as & when required
- Management of permissions on an individual and group basis
- Ensuring protection for all the data and overall infrastructure
Useful link: Key Business Benefits of Identity and Access Management
What is Identity Management?

Everybody has an identity. Our identities are represented as characteristics or database entries in the digital world. Cloud identity management services often gather these features to serve us better or develop a distinctive user experience based on the information gathered about the organization’s static and dynamic attributes.
Cloud users are different from regular internet users. Regular internet users don’t have to indulge in much information divulgence. A phone number or two will see the regular users off. But, the identities of the cloud users are much more different as an employer would typically provide his employees with qualities in the form of titles, affiliation with a particular business unit, project roles, and organizational structures which would define his business role and allow the employer to assign the identity.
Biometrics (thumbprints and retinal scans) and tokens are used in cloud identity management tools to protect users’ information from being copied by unauthorized parties. In addition, devices are increasingly used to identify a specific user as they become more portable and secure.
The identity management system will cross-check the supplied information against a lengthy list of all potential users. As a result, a system or business may experience exponential growth in the problem. Identity management solutions have evolved to issue identities based on groups and assign responsibilities for those groups instead of continuously going through a long list of users. As a result, fewer names and pieces of data need to be examined during the process.
How Cloud Identity Management Works?
For an organization, creating and maintaining user roles and access rights is the main focus of identity and access management. Identity and access solutions should provide a user repository, role definition and authorization engine, single sign-on authentication system, password management, account provisioning, de-provisioning, audit, and other features. An identity store or repository is the foundation of all IAM frameworks and solutions. The identity and access management solutions user repository might be a subsystem of a system like Active Directory, or it can exist independently as the only reliable source of information for all organization personnel. Then, roles and privileges will be assigned to users in the repository using the configuration of the role definition engine.
A federated identity service called single sign-on allows users to enter into numerous systems and apps with one set of login information. Users won’t have to enter their credentials while switching between platforms. Instead, once a user logs in to the identity and access management system are only granted the appropriate access based on their profile and role definition. For instance, the identity management solution requires users first to authenticate themselves before it allows them to search for patient information. The identity management software then confirms that the user’s information is up to date by checking the information it was given.
Why IAM?

An identity management solution can offer ensures and assists in monitoring employee behavior. For example, an organization’s identity lifecycle management will be strengthened if it can be known that only certain workers may examine identity access management tools and apps. Additionally, the system’s parameters may be customized to look for any questionable user behavior, communications, or other problems that could go unnoticed.
Without an effective cloud identity management system, tracking user information, such as email addresses, may soon become a complicated problem. Identity management solutions help guard against security problems by enabling administrators to automate various user account-related operations. This involves automated identity lifecycle management to allow workers access to the systems and apps they have been granted access to during the onboarding process.
By reducing the time spent resolving user account-related issues, cloud identity management assists enterprises in complying with regulatory standards specific to their sector and helps them save money. Moreover, when it comes to managing IDs, authentication, and authorization, identity and access management standardizes and even automates critical processes, saving time and money while lowering business risk.
Building a solid information security program requires using the many protective features provided by identity management solutions. These are just a few factors that security experts must consider when designing effective identification and access control systems to safeguard their enterprises. In addition, operationally sustaining and protecting an environment depends on your organization’s capacity to regulate and audit who enters and exits its network.
Identity and access management systems make it easier to monitor employee behavior. For example, it will be difficult for someone who is not permitted to acquire access since it will be known that only specific personnel may examine programs and apps. Additionally, you may configure the system’s settings to identify any erroneous activities, interactions, or transactions that could otherwise go unnoticed.
Identity and access management systems for managing identities and access are popular with businesses that want to hire more employees. As recruits go up the corporate ladder and acquire new titles and credentials, gradually offer them authorization which comes with underprivileged identity management.
Useful link: Identity and Access Management – The Increasing Concern on Cloud Security
Understanding Access
Decisions about access are binary: yes or no. When an online user seeks to access or utilize a resource, the access control will be responsible for deciding whether to allow it. Multiple access control points can be found inside an online service, and they frequently are.
An access control point on the top level attempts to identify whether user is even permitted to enter the site. The individual files are placed on the hard drive when the access control point descends to the lowest level. The end user can see access control points and call for action. Authentication would be the most straightforward illustration of the access management architecture.
The authentication process by identity access management tools involves determining the user’s identity. The user may verify in different ways. For instance, the user might prove his identity at the basic level by answering the query “Who are you?” with his name. On the other hand, the user might log in to the service using his electronic identification (eID) sanctioned by the government. The techniques and technology for authentication range widely between these two instances.
Explore IAM Consulting Services
What is Access Management?

Can an employee access the service after the user identification is established? Wrong. Authorization and authentication are two different things. A choice on access control must be made following authentication. The choice is made considering the user-related data at hand. The qualities are utilized in this situation. The access control decision point can analyze the characteristics and decide Yes or No if the authentication procedure can give the necessary set of attributes to it.
If a member of the accounting group logs into a system, they will have access to the company’s finances because they are part of that group. A person in engineering who gains access to the system will be permitted to view engineering plans, charts, drawings, and documents that the accountant cannot see. Still, they will not be able to see the financial data.
Access management establishes a user’s identity and characteristics to ascertain their authorization. Although it does not maintain such data, it analyses the identity and allows the user to access the infrastructure through the mechanisms established by the access asset managers.
What is the Difference Between Identity Management and Access Management?
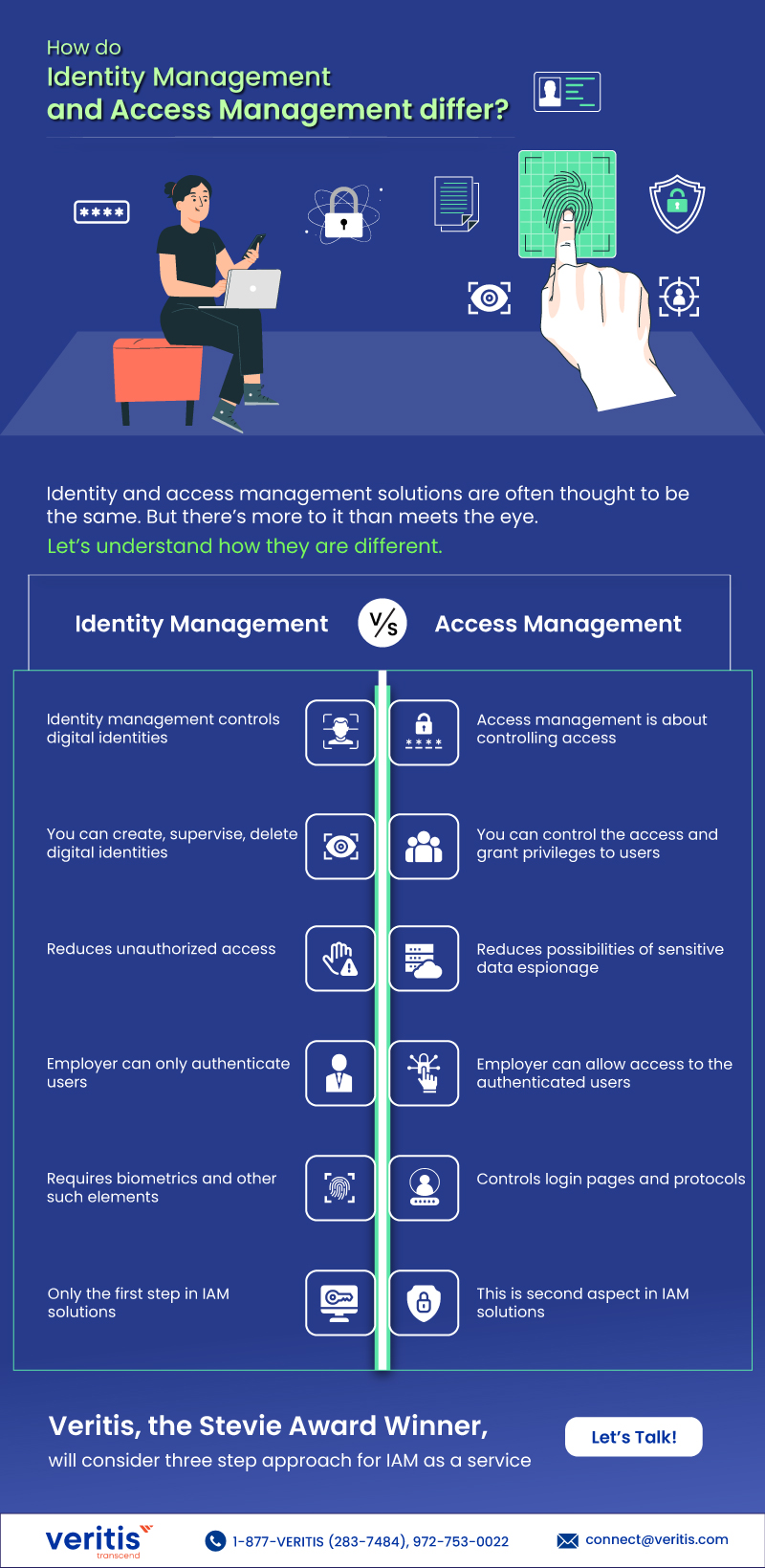
These two ideas are mixed since a user obtaining information must go through these two crucial phases. How access control works are based on the data that identity management provides. Users do not know that there is a whole distinct management system to establish their access since they provide identifying information. It might be challenging to recall that identity and access are distinct concepts because they are closely related.
Identity management solutions, to put it simply, controls digital identities. Digital qualities and database information are combined to form identities, which give each user a unique identity. Its administration entails creating, upkeep, supervising, and deleting such identities as they function within the corporate network. Businesses must ensure users have the necessary rights to do their tasks and minimize unauthorized access. Additionally, identity access management tools also manage authentication.
Access management, however, decides whether to let or deny people access to a resource, database, and various others. Additionally, it controls the login pages and protocols for the access portals and confirms that the user requesting access genuinely belongs. Since authentication can identify a user but cannot assess if they are deserving of access, this indeed differs from authentication. It controls authorization instead.
This is the central argument being made. Both authorization and authentication do not equate to one another. The former, a function of identity management, establishes the user’s identity, whether in light of groups, roles, or other characteristics. After authentication, authorization assesses the user to decide what they can see and access. The user is directed by one while the other unlocks the door. Managing identities and access rights combine the best of both worlds, which makes them identity and access solutions.
Capping it Off
Security is an aspect that you should never ignore, and IAM policies have to be initiated. Experts in IT solutions and cyber security, Stevie Award Winner Veritis is the preferred partner for most companies. Be it Fortune 500 companies or emerging enterprises, we have doled out customized solutions to organizations and ensured our IAM solutions don’t hamper productivity. So, reach out to us, and we shall integrate your infrastructure with robust security solutions.
Additional Resources: