
In a shocking turn of events, threat intelligence firm Cisco Talos discovered that malicious actors are increasingly exploiting public cloud technologies to deliver remote access trojans (RATs). They are achieving their notorious objectives without going through the endeavor of hosting their own infrastructure.
According to Cisco Talos, the threat actors are exploiting cloud services like AWS and Azure to develop their infrastructure and connect to the internet with minimal time and cost.
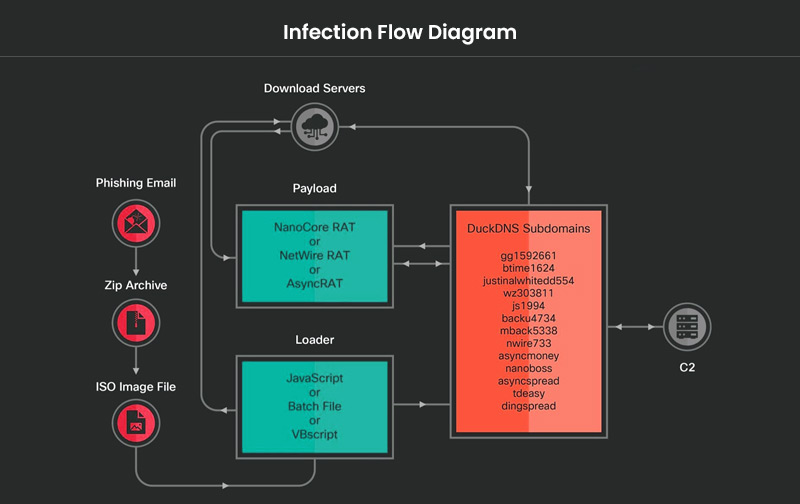
The cybercriminal, in this case, leveraged cloud platforms to deploy and deliver variants of commodity RATs, including Nanocore, Netwire and AsyncRAT, starting from October 2021. These malware variants are ingrained with malicious features capable of taking control over the victim’s system to remotely execute arbitrary commands and pilfer the victim’s data.
Also Read: AWS Vs Azure Vs GCP – The Cloud Platform of Your Choice?
How threat actors organized the savvy malicious campaign?
In the observed malicious campaign, the infection chain was started with phishing emails that contained malicious ZIP attachments.
“These ZIP archive files contain an ISO image with a malicious loader in the form of JavaScript, a Windows batch file, or Visual Basic script. When the initial script is executed on the victim’s machine, it connects to a download server to download the next stage, which can be hosted on an Azure Cloud-based Windows server or an AWS EC2 instance,” explained Cisco Talos.
Some of the malicious ZIP file names observed in the campaign are:
- WROOT_Invoice_Copy.zip
- YUEOP_Invoice_Copy.zip
- HOO8M_Invoice_Copy.zip
- TROOS_Invoice_Copy.zip
- TBROO1_Invoice_Copy.zip
The researchers discovered that the perpetrator registered several dubious subdomains using DuckDNS to deliver the malware payload. DuckDNS is an open-source dynamic DNS service that offers public DNS server services.
“Some of the actor-controlled malicious subdomains resolve to the download server on Azure Cloud while others resolve to the servers operated as C2 for the remote access trojan payloads,” said the researchers.
Some of the malicious subdomains identified by Cisco Talos are:
- gg1592661[.]duckdns[.]org
- btime1624[.]duckdns[.]org
- justinalwhitedd554[.]duckdns[.]org
- wz303811[.]duckdns[.]org
- js1994[.]duckdns[.]org
- backu4734[.]duckdns[.]org
- www[.]backu4734[.]duckdns[.]org
- mback5338[.]duckdns[.]org
- nwire733[.]duckdns[.]org
- asyncmoney[.]duckdns[.]org
- nanoboss[.]duckdns[.]org
- asyncspread[.]duckdns[.]org
- tdeasy[.]duckdns[.]org
- dingspread[.]duckdns[.]org
- asyncpcc[.]duckdns[.]org
- duckdns[.]org
- duckdns[.]org
- duckdns[.]org
“The fact that the hackers are constantly modifying their C2 centers with DuckDNS just shows how ‘by any means necessary’ the hackers are willing to operate,” said Garret Grajek, CEO at YouAttest. “The attacks like this one show a team effort in scanning, exploiting, obfuscation, and then finally exfiltration.”
Moreover, the downloader JavaScript used in the phishing campaign leveraged four layers of obfuscation.
“Each stage of the de-obfuscation process results with the decryption methods for the subsequent stages to finally arrive at the actual malicious downloader method. The de-obfuscation process is performed at each stage with every next stage generated as the result of the previous stage de-obfuscation function.”
In addition to the JavaScript loader trojan, the campaign also used a batch file downloader trojan and a VBScript downloader trojan and PowerShell dropper scripts.
The researchers also discovered another alarming fact that the malicious actor maintained a distributed infrastructure featuring download servers, command and control servers, and malicious subdomains. Furthermore, they hosted the downloading servers on AWS and Azure cloud services.
Also Read: How Google Cloud’s Digital Twin Shall End Your Supply Chain Crisis
Hackers at an advantage
The Cisco researchers noted that exploiting cloud services to host the payloads is a sophisticated effort to avoid the radar while cutting down costs as they don’t need to deploy their own infrastructure. “It also makes it more difficult for defenders to track down the attackers’ operations,” mentioned Cisco Talos.
“Threat actors use well-known cloud services in their campaigns because the public passively trusts big companies to be secure,” said Davis McCarthy, a security researcher at Valtix. “Network defenders may think communications to an IP address owned by Amazon or Microsoft is benign because those communications occur so frequently across a myriad of services.”
Also Read: Microsoft’s Cloud Services Rocked by Azure AD Outage
How can businesses prevent these attacks?
As the cybercriminals behind the said campaign are using dynamic DNS that doesn’t have a static IP address, developing an inventory of known cloud services and their network communication behaviors is imperative to fend off these campaigns. Businesses must set up comprehensive multi-layered security controls to identify and defend similar threats.
They must monitor their organizational traffic and set stringent rules around the script execution policies on their network endpoints. Moreover, organizations must double down on their email security to identify and prevent malicious emails and ax the infection at the early stage.
More Articles:
