
Imagine this scenario – If you are the CEO of a mid-sized organization with branches in different continents and three thousand employees, how efficiently could you monitor logins?
Perhaps, on a bad day, an employee would have lost their Smartphone or lost the paper in which they wrote the password.
In such a case, would you identify that one illegal or criminal login from all the 3000 logins that day?
This is why Identity and Access Management (IAM) solutions are gaining increasing prominence in 2020 for businesses to protect their interests and sensitive data from theft and violation.
While decentralized identity is yet to become a full-blown practice, passwords are still the prime source for protecting data, and IoT devices are continuously being hacked. In this scenario, we are yet to find a universal solution to manage online identities in both the government and the private sector.
Since the IAM space is continuously evolving, organizations identify new trends in Identity and Access Management to minimize data-breaches, meet regulatory requirements, and manage user identities to the utmost extent.
In this rapidly changing business scenario, here are upcoming trends that promise to revolutionize the IAM sector:
1) Adapting Biometrics
As per Global Market Insights, the global biometric market would reach an estimated value of USD 50 billion by the end of 2024. Perhaps one of the rapidly emerging trends in the IAM sector, biometrics like retinal scans, facial recognition systems, and fingerprints, is highly preferred for ensuring authorized users in networked systems. While this might come across as a fool-proof strategy, there is a security risk involved with this technology.
With various types of cyber-attacks possible, biometric information can be stolen and used for fraudulent operations. While a regular password can be changed if compromised, a user’s biometrics can’t be changed and permanent.
To counterbalance this threat, the future trend would involve IAM, which relies on biometric data, to get an additional layer of security for protecting the biometric information.
2) Blockchain
An ideal solution to protect biometric data is that Blockchain has come a long way from being valued at USD 706 million to an estimated USD 60 million by 2024. Blockchain offers features like transparency, reliability, and integrity, making it a popular choice for ensuring data protection with both public and private sectors.
While talking about Blockchain in the context of IAM, the two aspects, the come into play are – Audit trail and self-sovereign identity. Self-sovereign identity is the concept of an individual protecting their entire identity as their personal property rather than let an organization or third-party provider manage it. By keeping the individual’s information protected by encryption in a permanent blockchain across a distributed network system, this concept offers complete individual control over their identity data.
Through the Self-sovereign identity system, the idea is to replace centralized identity providers and instead let each individual take control and decrypt the data only when required.
Audit trail, a user’s entire login history, access request, permission grants, changes performed, or engagement is recorded. This is helpful for an organization in monitoring activities, detecting fraud, and also meets compliance requirements.
3) Single Sign-On Systems and MFA
While MFA is one of the most popular IAM practices, there is still plenty of scope for its improvement as data breaches still occur and cause substantial revenue losses. Adaptive Authentication is the advanced version of MFA, which relies on machine learning capabilities to detect malicious user behavior or illegal entry.
Adaptive Authentication pulls in all the details of user login in terms of login time, device, location, browser, and other data, which helps analyze a login attempt’s authenticity. Based on the analysis, if a login attempt turns out to be fishy, the system will ask the user to fill in an MFA to be authenticated.
Another popular IAM industry trend is Single Sign-on (SSO System) usage with MFA that helps users leverage a unified, singular set of credentials to gain access to networks, data, applications, web, and the cloud.
4) IAM and the Internet of Things (IoT)
With the arrival of the Internet of Things (IoT), there is a massive requirement for Identity Access Management service. Whenever an IoT based device is added to a network, there increases the need to mitigate security risk. Based on a report developed by Microsoft, IoT is increasingly being used across all major sectors, and by 20201, 94% of businesses will use IoT.
Hence, the current priority is to ensure secure identity access management on these IoT devices for restricting the entry of hackers into the network. Devices that can pose a threat could feature smart TVs, security cameras, and smart bulbs.
Another technology that could prove to be a breakthrough is working on IAM systems, which require the system to authenticate a user’s access through numerous devices.
Also, in numerous cases, securing IoT devices would be achieved by embedding the device identities in the processing chip and being an integral part of the hardware.
5) Artificial Intelligence in IAM
An aspect of Identity Management, Context-based identity, is responsible for comparing data about a user who needs to be vetted to authenticate an identity. This data includes numerous behavioral patterns like physical location, IP address, usage, preferences, and machine address.
Leveraging AI programming algorithms for data mining helps discover data patterns that are extremely helpful in reducing fraud and identifying risks. This technique has been highly useful in banking systems across the globe.
6) Identity Access Management for Cloud Services
Since the cloud is in great demand, organizations have been shifting to cloud services to provide advantages such as efficiency, scalability, and flexibility. While the cloud brings many benefits, few security concerns should not be ignored.
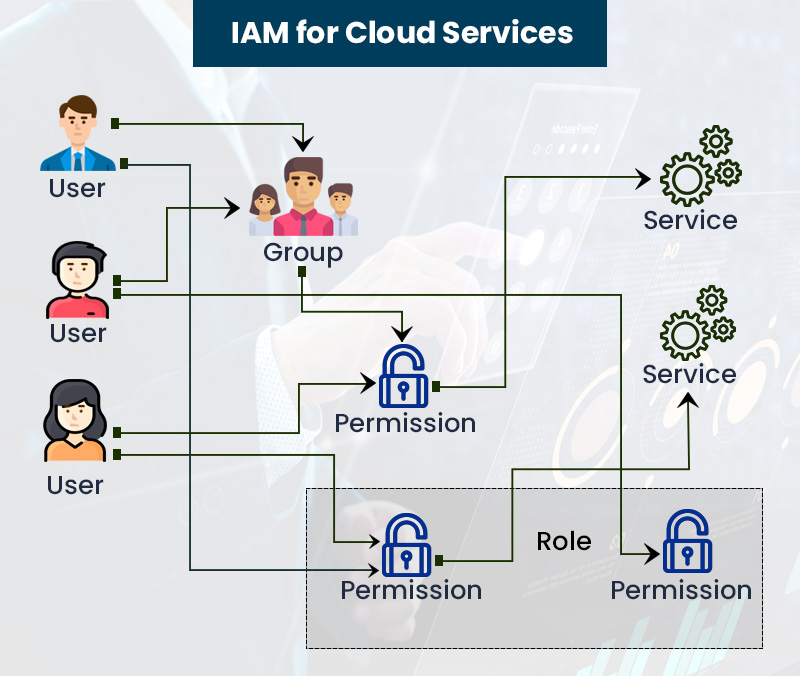
It is essential to employ a secure digital strategy like Cloud User Access Management Software, also known as User Access Management (UAM). Through this system, organizations can create authorized logins for users to access crucial data and applications.
Legacy Applications Vs Modern Applications Explained!
Legacy application modernization helps create new business value from existing, aging applications by upgrading them with modern functionalities, features, and capabilities.
However, modernizing can be successful only when the organization has a well-thought-out plan.
Comparing the characteristics of legacy and modern applications helps gain insight into what must change in the legacy applications during the application modernization process.
Here are some prominent differences between Legacy and Modern Applications:
| Legacy Applications | Modern Applications |
| Text-based User Interface (TUI) – novice users need to learn and use | Graphical user interface (GUI) is user-friendly, intuitive, and familiar |
| Hidden tree-like hierarchy | Visible menus and tree-like hierarchy |
| Fixed path navigation | Point-and-click navigation |
| Integration with other systems is complex and costly | Simplified integration with other applications including Microsoft Word and Excel |
| Monolithic applications – for any small change, a new version of the entire application needs to be rolled out | Multitier application architecture – a specific layer can be modified or added, instead of reworking the entire application |
| Compatibility restricted by device type such as a 5250 terminal | Runs on all types of devices, including personal computers, smartphones, and portable devices |
| Declining skill base and diminishing vendor support | Readily available skills and multi-vendor support |
| Requires specific expertise for maintenance and upgrades | Widely known development languages and tools |
How we, at Veritis, aim to help you

Veritis’ approach to IAM services and solutions is built on core activities, namely, Access Management, Identity Management, Access Governance, and PAM. We help you elevate your organization’s goals towards digital transformation and help develop data strategies in line with revenue maximization and achieve customer satisfaction.
More IAM Services and Solutions Articles:
