The rapidly evolving cybersecurity landscape has proliferated the demand for secure access. With huge amounts of data to be stored, processed and transmitted, it’s imperative for the businesses to ensure the right users have the right access.
However, with the growing digital adoption, managing identities and controlling access is becoming complex and challenging, creating enough scope for potential cyber threats.
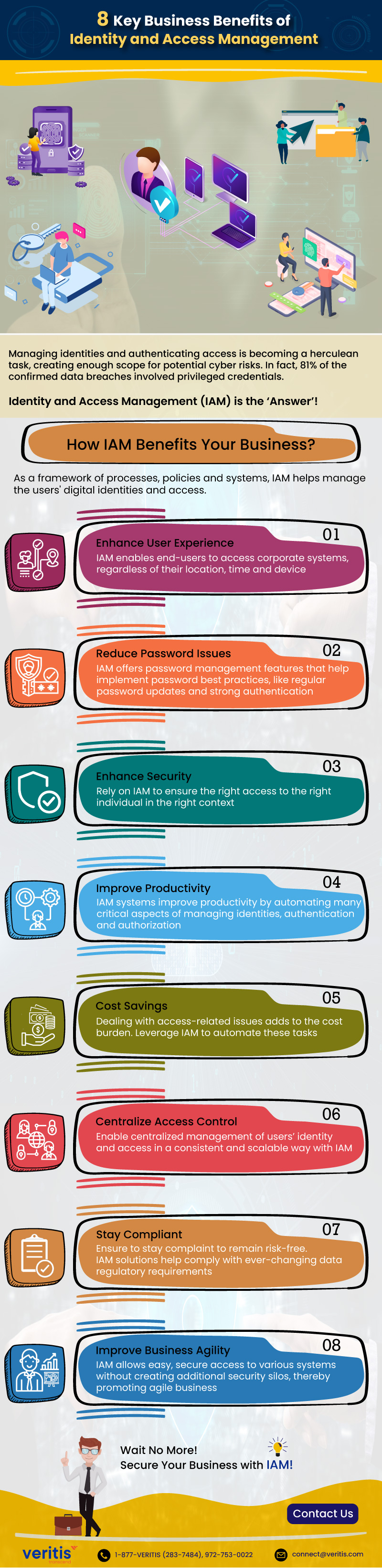
In fact, 81% of the confirmed data breaches are due to weak, stolen and default user passwords.
This is where Identity and Access Management (IAM) stands crucial!
Here is an infographic about ‘8 Key Advantages of Identity and Access Management
Email-us: connect@veritis.com; Call: 972-753-0022
8 Key Benefits of Identity and Access Management for Your IT Business
Managing identities and authenticating access is becoming a herculean task, creating enough scope for potential cyber risks. Identity and Access Management (IAM) is the ‘Answer’!
As a framework of processes, policies, and systems, IAM helps manage users’ digital identities and gain access.
1) Enhance User Experience
IAM enables end-users to access corporate systems, regardless of their location, time, or device.
2) Reduce Password Issues
IAM offers password management features that help implement best practices for password management, such as regular password updates and strong authentication.
3) Enhance Security
Rely on IAM to ensure the right access privileges to the right individual in the right context.
4) Improve Productivity
IAM systems improve productivity by automating many critical aspects of managing identities, authentication and authorization.
5) Cost Savings
Dealing with access-related issues adds to the cost burden. Leverage IAM to automate these tasks.
6) Centralize Access Control
Enable centralized management of users’ identity and access in a consistent and scalable way with IAM.
7) Stay Compliant
Ensure to stay complaint to remain risk-free. IAM solutions help comply with ever-changing data regulatory requirements.
8) Improve Business Agility
IAM allows easy, secure access to various systems without creating additional security silos, thereby promoting agile business.
Wait No More! Secure Your Business with IAM!
Related IAM Stories:
- Identity and Access Management (IAM) Tools to Improve Security
- What to Expect: Future Trends in Identity and Access Management
- Identity and Access Management Audit Checklist and Strategy
- Regulatory Compliance Made ‘Easier’ With Identity and Access Management Solutions in US
- How to Implement Identity and Access Management (IAM)?
- Best Practices for Identity and Access Management

