
Creating and delivering software has become remarkably efficient in our rapidly changing digital landscape thanks to the CI/CD environment and essential tools. However, amidst the seamless code integration facilitated by these CI/CD tools, we must recognize a crucial factor: security.
It highlights the vital task of fortifying your CI/CD environment against cyber threats. As technology advancements, so do the tactics employed by malicious individuals searching for vulnerabilities in your software. Our journey takes us from a discussion of continuous integration tools responsible for merging code from various sources to continuous delivery tools, which help deliver that code to its destination. We’ll explore strategies to shield your CI/CD environment from these threats, ensuring your software remains speedy and secure.
The term CI/CD pipeline encompasses a set of steps that include Continuous Integration (CI) and either Continuous Deployment or Continuous Delivery (CD). Typically employed by DevOps teams, the CI/CD pipeline is an efficient approach for constructing, testing, and deploying code, primarily using automation tools.
Harnessing the power of a CI/CD pipeline has consistently proven to streamline the process of creating and deploying software updates, ultimately resulting in higher-quality updates. This success is primarily attributed to the need for ongoing collaboration and the faithful application of Agile and DevOps CI/CD principles in maintaining robust tools.
So, let’s embark on this journey to bolster your CI/CD setup, where the code integration world meets the security imperative.
Importance of CI/CD?
CI/CD is a methodology enabling DevOps teams to deliver code updates consistently and swiftly. It accomplishes this by leveraging continuous integration (CI) and continuous delivery (CD) principles. At its core, CI/CD tools strongly emphasize automating every stage of the development process, encompassing building, testing, and deploying code.
This automation supersedes the manual processes of traditional development, resulting in more frequent code releases that are not only faster but also notably free of common issues such as bugs and security vulnerabilities.
Useful Link: All You Need to Know About Kubernetes Deployment Strategies
What is Continuous Integration (CI), Continuous Delivery (CD), and Continuous Deployment?
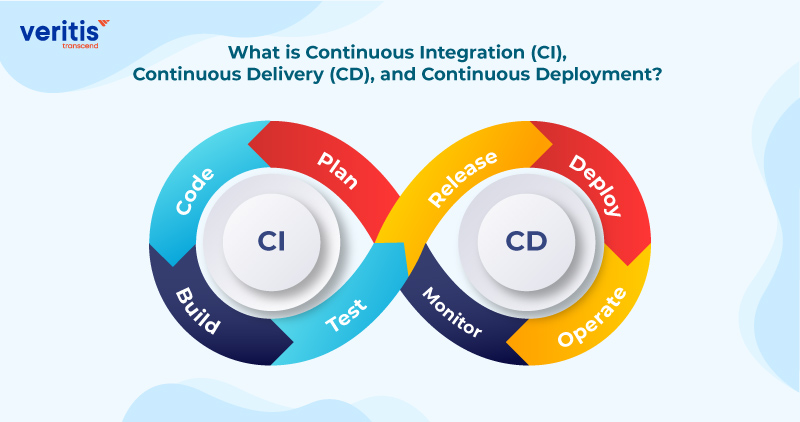
Continuous Integration (CI)
Continuous integration, commonly called CI, is a software development approach where code modifications are consistently incorporated into a communal code repository. These changes are automatically tested as soon as they’re added. Unlike traditional methods where testing happens later, CI tests code as developers write it.
The significant advantage of CI is that it reduces risks. Your team always knows where they stand in their work. They can quickly spot what’s working and what’s not, identify and fix bugs early, and understand what their team members are up to. Code conflicts are less likely because different developers’ work is regularly combined.
Continuous Delivery (CD)
Continuous delivery, an extension of continuous integration tools, means that your team automatically puts new code into a place like GitHub. Depending on what you and your users need, this code can be sent to the live website or app whenever you want.
The cool thing is that continuous delivery uses much automation to make this process easier. It saves you from doing lots of manual work when implementing code. So, with continuous delivery, you can react faster to things like changes in the market or security problems.
But you’ll need a reliable server and good computer equipment to make it work smoothly. Your DevOps CI/CD team (the folks who manage both development and operations) will also need to get comfortable switching from manual to automated testing. This can be a significant change for some companies.
Continuous Deployment (CD)
Continuous deployment is the most advanced part of the CI/CD process. The big difference from continuous delivery is that it automatically sends new code updates to the live website or app.
But here’s the catch: for continuous deployment tools to run smoothly, you must put much effort into automated tests. This is because it removes the manual step, where someone checks the code before it goes live.
Just like with continuous delivery and integration, continuous deployment tools cost a lot initially. But the payoff is that you get feedback from users almost instantly, and there’s minimal delay between when you create code and when it goes live.
What is the CI/CD Pipeline?
Think of the CI/CD pipeline as a series of steps that ensure your software is always up to date-and working well. This is the foundation of what your DevOps CI/CD team does. Usually, your DevOps continuous integration team’s leader ensures these steps run smoothly.
Components of a CI/CD Pipeline
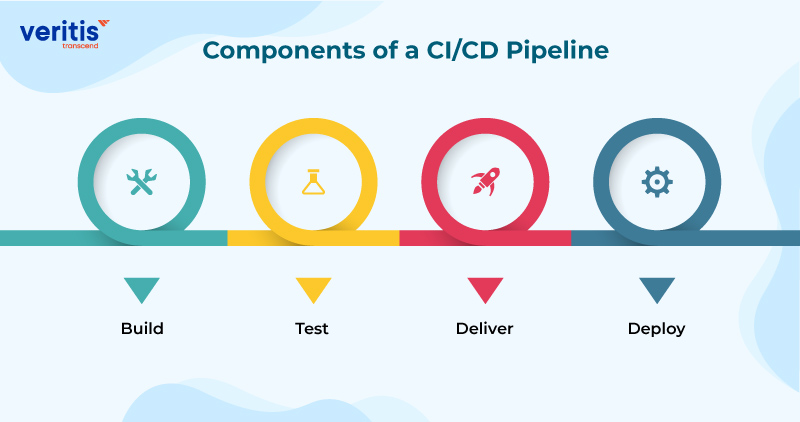
Every CI/CD pipeline uniquely suits your team’s needs and tools. However, they all have four critical stages:
1) Build: This is where you transform your source code into a functional software application. Imagine it’s like assembling a puzzle.
2) Test: You want to test your software in the continuous delivery pipeline. It’s like checking if all the parts of a machine work properly. You do this by doing small tests to ensure new features work and by testing to ensure you didn’t accidentally break anything that was working.
3) Deliver: After testing, your software goes to a place where you can look at it closely before showing it to everyone. It’s like testing a new product in a small market before selling it everywhere. This helps you find problems and lets your Quality Assurance (QA) team see what they need to check.
4) Deploy: When your software passes all the tests, it’s ready to go live. With continuous delivery, a person looks at it one more time before it goes live. But with continuous delivery vs continuous deployment, it goes live automatically, like flipping a switch.
So, these four steps help make sure your software is always good and ready for users.
Useful Link: CI/CD Pipeline: 15 Best Practices for Successful Test Automation
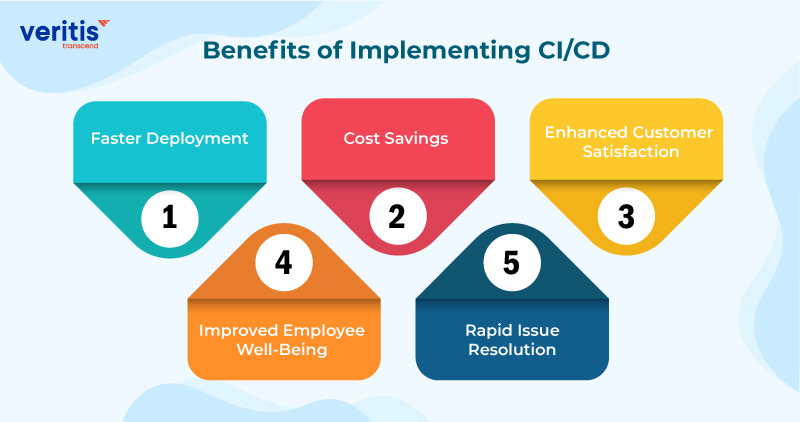
Benefits of Implementing CI/CD
Implementing a CI/CD pipeline offers several advantages to companies and organizations:
1) Faster Deployment
One of the primary advantages of CI/CD DevOps is the acceleration of the deployment process. Traditional software development often involves manual testing and deployment, which can be time-consuming and error-prone. CI/CD, through automation, streamlines these tasks, allowing code changes to be thoroughly tested and deployed quickly and efficiently.
This speed reduces the time it takes to deliver new features or updates to users and enhances a company’s agility in responding to market demands and customer feedback. As a result, companies can stay competitive and maintain a rapid pace of innovation.
2) Cost Savings
Implementing CI/CD DevOps practices can lead to significant cost savings for organizations. Automation reduces the manual effort required in various stages of software development, from testing to deployment. Developers spend less time on repetitive tasks, which means reduced labor costs.
Moreover, the faster deployment of code changes means fewer resources are tied up in lengthy development cycles, resulting in lower operational costs. Additionally, CI/CD helps catch and address issues earlier in the development process, reducing the cost of fixing bugs and vulnerabilities at later stages. These cost savings contribute to a more efficient and economically viable software development process.
3) Enhanced Customer Satisfaction
A continuous feedback loop enhances customer satisfaction through continuous delivery vs deployment. This loop allows development teams to collect insights and feedback from users and stakeholders during development.
By acting on this feedback promptly and making ongoing improvements, development teams can ensure that code changes are not only free of bugs but also align with user expectations and functional requirements. This iterative approach creates a positive user experience, ultimately leading to happier customers and users who see their needs addressed and their feedback valued.
4) Improved Employee Well-Being
In a CI/CD environment, improved employee well-being directly results from task automation. With testing and deployment processes streamlined, developers have more time to focus on creative and fulfilling projects, leading to increased job satisfaction. Furthermore, CI/CD encourages enhanced collaboration among development teams, promoting unity and shared responsibility.
This collaborative atmosphere enhances work quality and reduces the risk of burnout, as team members support each other and distribute work more efficiently. As a result, employees enjoy a healthier work-life balance and a more positive, productive work environment.
5) Rapid Issue Resolution
Frequent and smaller batch deployments, a core principle of CI/CD, lead to a significant reduction in Mean Time to Resolution (MTTR). This means an issue or bug can be identified and fixed more swiftly due to the more minor code changes introduced in each deployment. Furthermore, if a critical problem surfaces, teams can quickly roll back to a prior, stable deployment state.
This agile approach minimizes system downtime and disruption, ensuring a more responsive and reliable software environment for users and enabling faster recovery from any unexpected issues.
Useful Link: DevSecOps Implemention : Enhancing Security for an Energy Services Firm
Best Practices for CI/CD Pipeline Security
To ensure the safety of your data and the authenticity of your processes and to make the most of DevSecOps practices, put these CI/CD pipeline security best practices into action.
1) Start With Research
Before you start writing any code, it’s crucial to identify potential threats to your continuous delivery pipeline’s security and the software you’re building. Look for points where extra security might be needed, conduct threat modeling, and stay vigilant about security updates and verification processes.
Typically, any point where your pipeline connects to an external tool, framework, or service is a potential security risk. Make sure you regularly install and update security patches. Block any devices or software that don’t meet security standards.
2) Implement Strict Access Controls
Ensure that everyone who accesses your pipeline is authenticated correctly. Require measures like one-time passwords and authenticators for people involved in the pipeline’s process.
When securing non-human access (like access needed by automated continuous delivery tools and frameworks), it’s essential to evaluate machine identity. Use authenticators to confirm that the attributes of a container requesting access match what the pipeline recognizes. Remember to destroy containers and virtual machines after they’ve served their purpose.
3) Be Cautious With Access Permissions
Always track who has access to different parts of your pipeline’s functionality. Divide and differentiate access levels based on roles, access time, or specific tasks. Maintain a comprehensive access management database and categorize information based on access levels. Intelligent team management can implement this highly effective CI/CD security practice.
4) Implement the “Least Privilege” Principle
The “least privilege” practice only gives access to information necessary for a particular role or task. In other words, individuals are granted access to a limited dataset and section of the CI/CD pipeline, only as much as they need to accomplish their assigned tasks.
Extend this practice to connected systems, devices, and applications as they require different access levels to perform their functions. Regularly review access levels to strengthen the principle of least privilege and maintain a secure ecosystem.
5) Secure Your Git
Git is a prime target for hackers and security threats, so ensuring its security is essential. Every developer and tester involved in a project should be well-educated on safe Git usage, avoiding common security pitfalls, and following best practices to protect code stored in Git.
Utilize the. Ignore files to prevent accidentally committing generated and cached files. As part of your broader backup strategy, establish and use a locally stored and secure backup repository. Incorporating these CI/CD security best practices can help ensure data safety, protect the authenticity of processes, and optimize your DevSecOps practices difference between continuous delivery and continuous deployment tools while using various CI/CD pipeline tools and automated deployment techniques.
Useful Link: Achieving Continuous Application Security with DevSecOps
Conclusion
Integrating DevSecOps into a development pipeline can be challenging, particularly for teams new to this paradigm. Without a well-planned adoption strategy, internal friction may arise. Start by breaking down the adoption process into manageable steps, allowing teams to become familiar with DevSecOps tools and practices, fostering a shift in the team culture.
At Veritis, a recognized recipient of prestigious awards such as the Stevie and Globee Business Awards, we’ve helped organizations establish robust DevSecOps strategies. Rooted in efficiency and productivity, we use automation and DevOps principles to seamlessly integrate security into the development pipeline. Whether you’re in the planning phase or navigating tool selection, we’re here to streamline your DevSecOps adoption, ensuring it aligns effectively with your CI/CD practices.
Looking for Support? Schedule A Call
Additional Resources:
- Demystifying MLOps vs DevOps: Understanding the Key Differences
- AIOPS Solutions: Enhancing DevOps with Intelligent Automation for Optimized IT Operations
- DevSecOps Implemention : Enhancing Security for an Energy Services Firm
- Building a High-Performing DevOps Culture: Strategies and Best Practices for CEOs and CTOs
- Kubernetes Vs. OpenShift: Which One Should You Choose?
- Future of DevOps: Top DevOps Trends in 2023 and Beyond
- DevOps outsourcing: Things to Know About Before Getting Started
- Explained: Pros and Cons of DevOps Methodology and its Principles